OK Gents, thanks for your patience with me! Please stay with me me as I try to figure this out. I’ve read a lot of posts but still can’t figure out what exactly I need to do and what commands.
I can’t get NFC TagInfo in my iPhone 14 to read anything. Tried credit cards, bank cards, and a UID 13.56MHZ that came with my Proxmark3 Easy I bought 4-5 years ago.
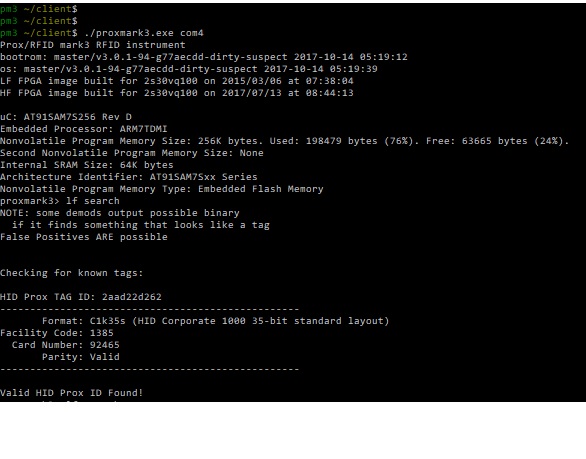
To date, all I did was copy the HID 125MHz info on to a blue pastiche tag but that does not work. Here are some screenshots I recently done:
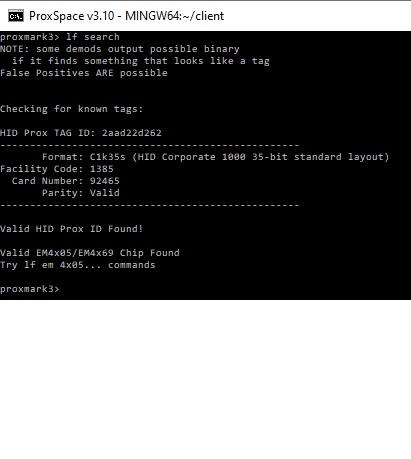
But if I keep moving the card around a bit, the LF SEARCH finds an EM4X05 chip. Do I need to copy this info on another blue tag?
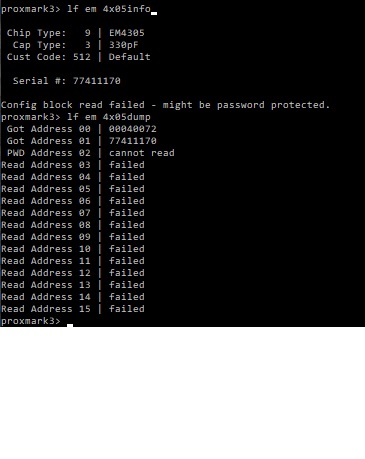
Not really sure what all this LF EM 4X05INFO and 4X05DUMP information means:
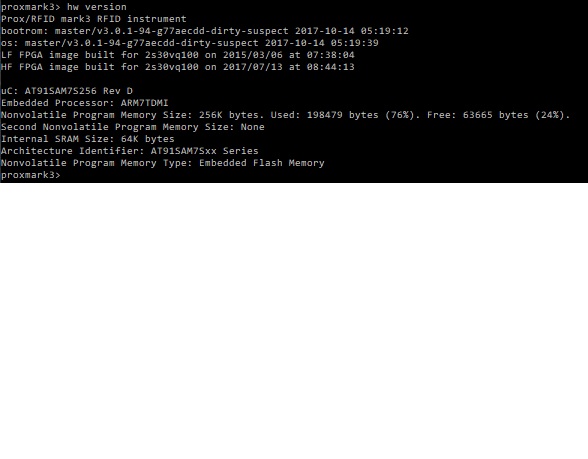
Oh yah, the HW VERSION info that likely tells you I’m running ancient software. Not sure how I update any of this.
So, where does this leave me? Who knows!
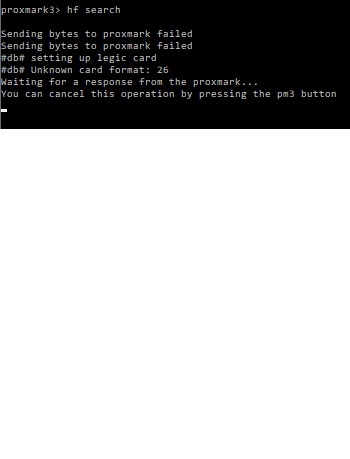
An HF SEARCH just crashes my Proxmark:
Any recommendations what I do next would me much appreciated. I’m using Windows 10. Please link any specific guides if available.
Thanks again for your patience! I will buy a new Proxmark some day but am hoping my Proxmark3 Easy can handle this task.
~Blackhawks