Switch 2/ p10 Downgrade selection tutorial
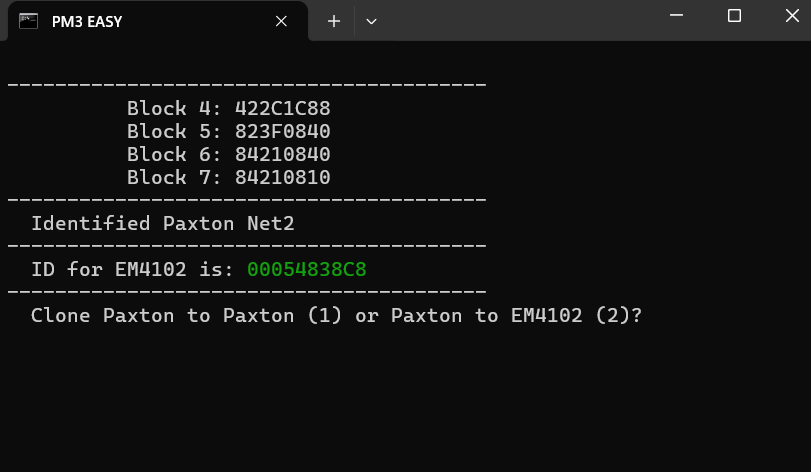
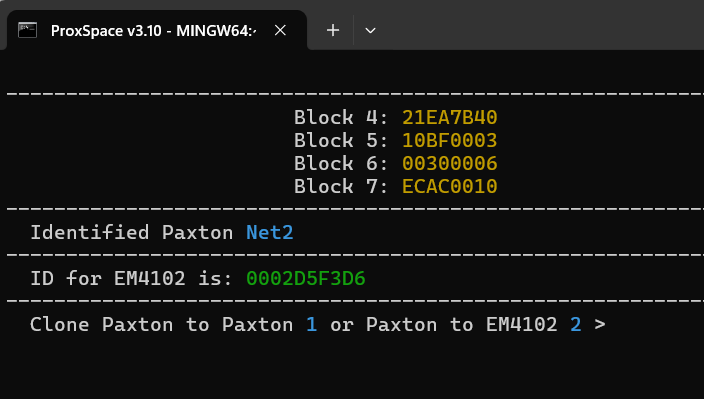
→ Blocks 4/5/6/7:
84030140
20422820
3D824840
0C201084
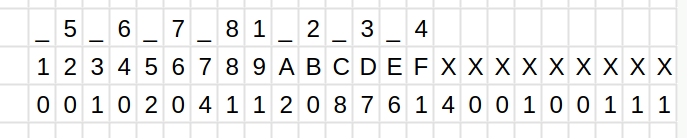
→ Convert to binary, split into 5 bit chunks, disregard the last two bits of each block, they mean nothing.
10000 10000 00001 10000 00010 10000 00
00100 00001 00001 00010 10000 01000 00
00111 10110 00001 00100 10000 10000 00
00001 10000 10000 00001 00001 00001 00
→ the first bit of every 5bit pad is an odd-parity bit. remove it and convert every nibble into decimal.
result:
0000 0000 0001 0000 0010 0000
0100 0001 0001 0010 0000 1000
0111 0110 0001 0100 0000 0000
0001 0000 0000 0001 0001 0001
converted nibbles: 001020411208761400100111
apply this funky selection mask (capped because trying to align text with spaces is so hard its easier to do in a sheet)
resultant switch2 ID: 10710001 (decimal)
convert to hex: A36BF1
pad with leading 0s to reach 5 bytes for em4100 ID:0000A36BF1
for NET2
net2 is exactly the same but actually way easier, the second nibble of the second byte in block 5 will always be F, you do the same conversion and removal of the off parity but instead of selecting the digits in a mask you just take all the digits in order leading up to the F.
42 2C 1C 88
01000 01000 10110 00001 11001 00010 00
8 8 6 1 9 2
82 3F 08 40
10000 01000 11111 10000 10000 10000 00
0 8 F 0 0 0
84 21 08 40
10000 10000 10000 10000 10000 10000 00
0 0 0 0 0 0
84 21 08 10
10000 10000 10000 10000 10000 00100 00
0 0 0 0 0 4
net2 ID:88619208
em4100 ID (hex with padding): 00054838C8
@amal sorry for the delay good sire my brain took a bit to upload
if anyone needs further clarification on anything lmk, this was speedy but i hope it gets the method across.
E2A fun fact, if youre using multi tech readers you can encode this as mifare classic 4Byte UID so long as you use little endian (reverse the byte order)