fonzogl
February 9, 2025, 9:27am
21
[usb] pm3 → hf 14a config --bcc ignorepm3 → hf 14a info
[=] ---------- ISO14443-A Information ----------
[?] Hint: try hf mf commands
1 Like
Hmmmmmmmm… Nope, still don’t understand this error…
Just to satisfy my curiosity, would you run an hf mfp info?
1 Like
fonzogl
February 9, 2025, 9:33am
23
Aoxhwjfoavdlhsvfpzha:
hf mfp info
[usb] pm3 → hf mfp info
[=] — Tag Information ---------------------------
[=] ---------- ISO14443-A Information ----------
[#] BCC0 incorrect, got 0x32, expected 0x72
1 Like
fonzogl
February 9, 2025, 9:36am
24
I run it again, and the output is different.
[usb] pm3 → hf mfp info
[=] — Tag Information ---------------------------
[=] ---------- ISO14443-A Information ----------
[?] Hint: try hf mf commands
[#] BCC0 incorrect, got 0x32, expected 0x72
1 Like
Dang…
The one card I have that has this same error is a MFP with MFC emulation mode enabled, I was kind of hoping that would be a trend, as that might give a clue to the root cause…
But this seems to be a genuine Mifare Classic as far as I know how to check anyways…
1 Like
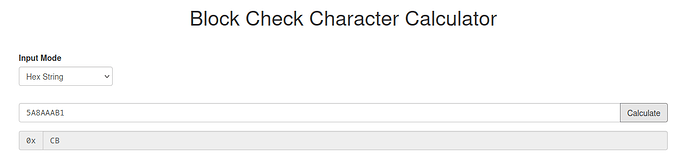
Anybody know why the BCC the PM3 is looking for is different than the BCC online calculators think it should be?
1 Like