Ok.. I did some testing with some bullseye ntag216s..
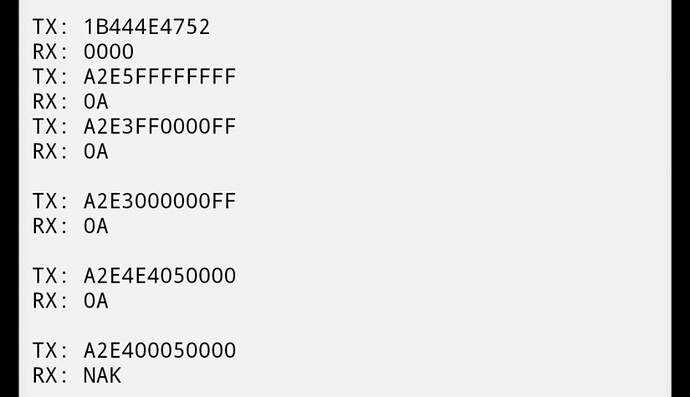
The screenshot
The rundown
• The first scan authenticates with DNGR (this was an older bullseye tag that was set up as a NExT using the password DNGR), writes a new password to the default value FF FF FF FF, then writes page E3 to FF 00 00 FF. This all works as expected.
• The second scan changes the value of E3 to 00 00 00 FF to prove that the CFG byte being set to FF has no effect on page E3. This works as expected.
• The third scan changes the value of E4 to E4 05 00 00. I leave the RFU byte 1 set to 05 because well, it’s just set this way to begin with and I don’t want to change it. This works.
• The final scan attempts to change E4 back to 00 05 00 00. This fails.
Conclusion
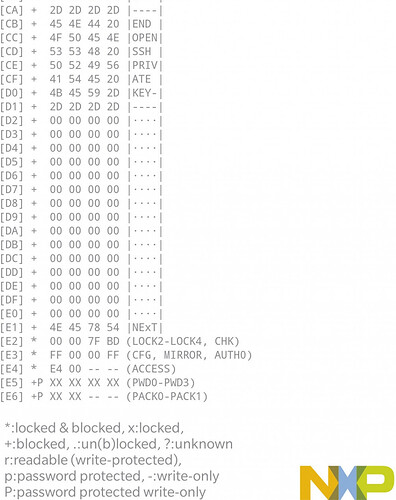
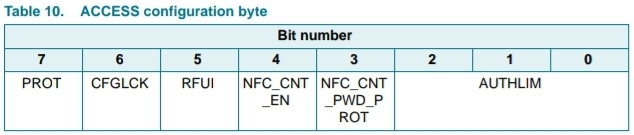
Setting byte 0 of page E4 to 1110 0100 (E4 in hex) results in the entire configuration section locking down.. but why? Let’s take a look again at the memory breakdown for the ACCESS byte (byte 0 of page E4);
Notice how bit 0 is on the right side of the bit list, not the left side?
Since E4 = 1110 0100 in binary, and when reading binary the LSB (least significant bit) is on the right side, it means when reading the binary in the “traditional” left to right way, the first 3 bits starting on the left are actually bits 7, 6, and 5 listed on the memory map, or in other words, PROT, CFGLCK, and RFUI, which are all value 1. Your CFGLCK bit is flipped to 1, and your configuration pages are locked.
Basically, NXP is trying to help people out by reversing the bit numbering order in their documentation in order to allow you to simply read the binary left to right as normal, rather than having to reverse it in your head.
![]()
![]() I wonder if they use it during testing and cbf to change it back.
I wonder if they use it during testing and cbf to change it back.