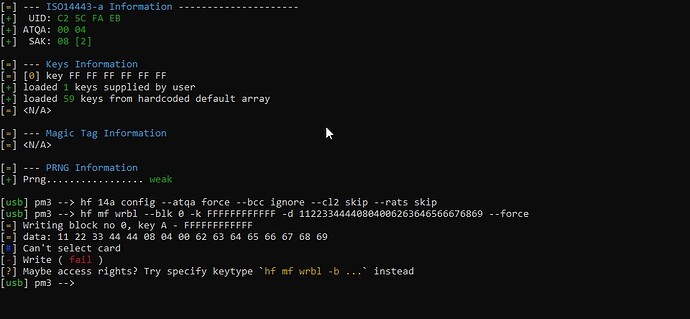
nothing is supposed to happen really.. you are simply setting configuration flags telling the proxmark3 how to behave when dealing with iso14443 transponders. It might be nice though if it said something like “Configuration updated” or something.. but this is normal.
Did you actually run the recovery command after this as mentioned in the threads @Pilgrimsmaster linked above? You need to tell the exact and complete story of what you did.. otherwise we have to play detective, and that only makes things harder for you.
From what you posted above, I assume maybe you have simply set the configuration part, got no response, then did not proceed with the rest of the recovery commands? First do those things.
how gen2 tags work
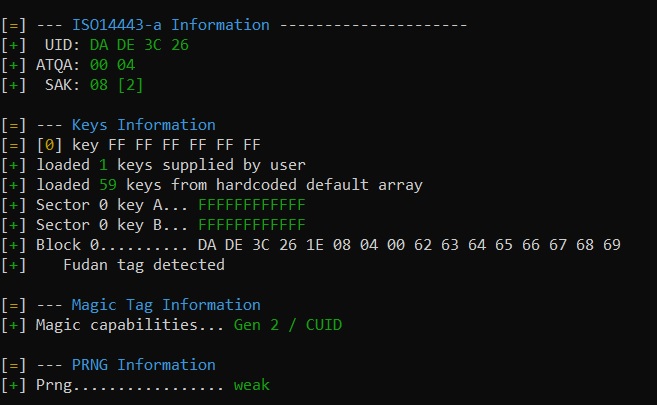
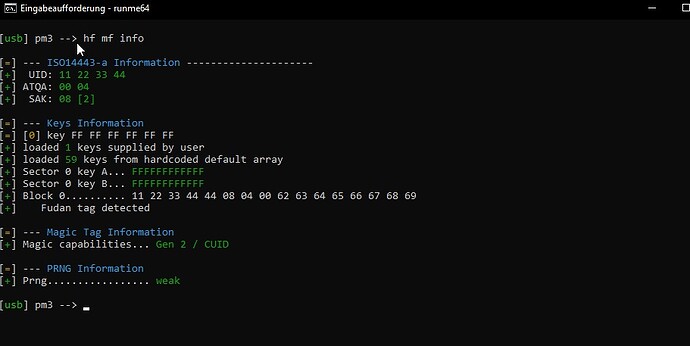
Let me briefly explain how gen2 tags work.. they work just like a normal Mifare S50 1k chip works, except you can change sector 0.. but other than that, they work exactly like a legitimate Mifare S50 1k chip. That means if you change the keys or access bits for any sector (including sector 0) in such a way that the sector is locked, or even protected from reading without first authenticating, then after cloning you will need those keys to access / change / read that sector.. even sector 0.
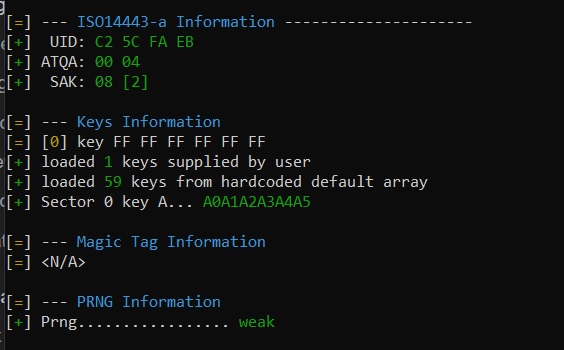
You can see in this screenshot under “Keys information” that there is a key loaded (supplied by user) which is the factory default FF FF FF FF FF FF and a set of 59 “default” keys.. but chances are your gym card’s keys are not included in that list of default keys.. and it’s probably not the factory default FF FF FF FF FF FF key either.. so at this point you can’t change sector 0 without those keys.
Because a gen2 chip works EXACTLY like a legit Mifare S50 1k chip, there is no way for the proxmark3 to really “know” if it’s a gen2 chip or a legit Mifare chip without some way to probe or test sector 0 .. and that’s only really possible if the keys are the factory default keys, or known to the proxmark3 in the default key array. Since it appears something cloned successfully to the chip, chances are sector 0 keys and access bits got changed so the proxmark3 could no longer probe it successfully, hence the missing “magic capabilities” line.
@iceman, this sounding correct so far?
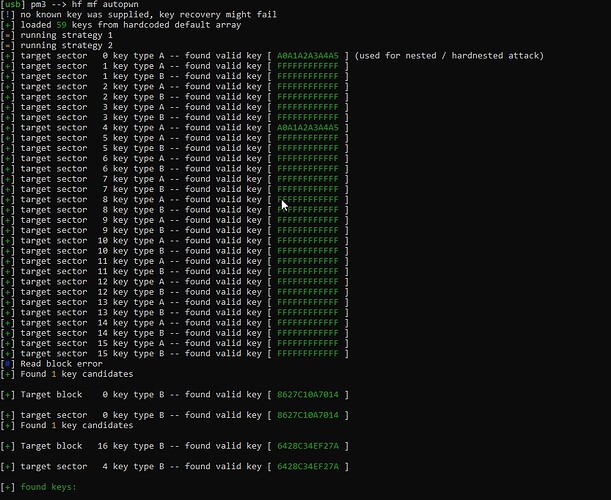
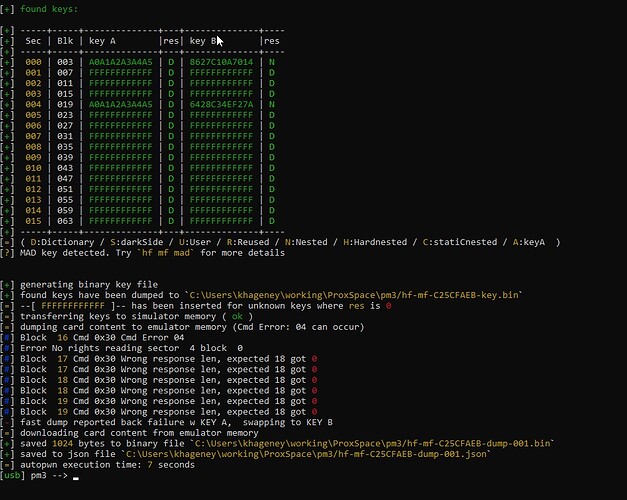
Luckily you can get those keys because you should be able to run autopwn on the gym card again and get the keys from that, then assuming the clone to your chip was exact and complete, use those keys to unlock sector 0.. or you may be able to autopwn your implant as well and get the keys directly.
Once you have the keys, you should be able to wipe sector 0 using those keys. Exactly how to do that I’m not sure but I know you should be able to specify them in the command line or reference a key file that autopwn generates.