Been playing around with FIDO2 for Windows Logon / Microsoft Account access and I can confirm that:
-
Regular users of personal Microsoft Accounts can use the Apex Flex FIDO2 applet to login to their account on the web. I’ve tested on Edge & Chrome at my PC. Android doesn’t currently work.
-
Users that login to Windows with their Microsoft Account currently cannot use the Apex Flex FIDO2 applet to login. (this is what @amal was talking about RE: becoming “Microsoft compatible”)
-
Buying Windows 10/11 Pro will not allow you to sign in with a FIDO2 or U2F security key, despite what you may read online. The group policy setting will have no effect. FIDO2 & U2F sign-in is an Azure AD feature.
-
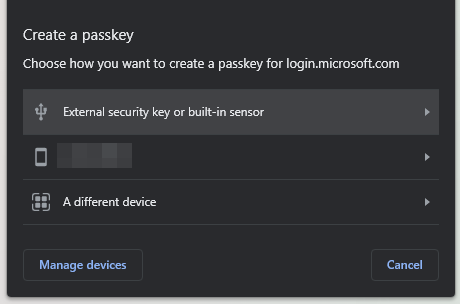
If the account you login to Windows with belongs to an Azure AD organisation, you might be able to add the Apex Flex as a sign-in method, but only if it’s configured to allow FIDO2 as a method, self-service setup is enabled, and “Enforce attestation” is disabled. (Check by trying to login here)
-
If you have a regular Microsoft account, you may sign up for Azure for free, and create your own, entirely free, Azure AD. You’ll need to sign up for the “pay as you go” option, but you’ll not be charged anything unless you explicitly choose to pay for something. You don’t need to. This process is frankly, irritating as hell. The Azure UI is a little janky and as this is all quite new, there is little help available. See below for my experience…
One of two lingering questions I have is - from what I’ve read in another thread here, attestation works. And, from my tests on Android, it functions as expected. However, Microsoft’s Azure AD FIDO2 support refused to accept the Apex Flex until I disabled that requirement. Is this what getting certification from Microsoft will fix?
The other is - Microsoft Azure AD has no options for allowing pin-less registration, and I don’t think it’s likely to happen. Could it possibly be linked to the current need to not enforce attestation? (IE. A pin is required when attestation isn’t available)
Finally, my experience setting up Azure AD with a personal Microsoft account, on a PC I’ve been logging into with a password:
-
Initially, I tried to simply access the Azure AD portal, and ran into many permission-like errors. I expected this, but it looked very broken and “possibly might work”.
-
I then tried to sign-up for Azure using their promo link, only to get turned down (I think I may have used Azure in the past). I then tried signing up for pay-as-you-go, which also turned me down right at the very end. However, once I did that, I had access to the Azure portal and didn’t run into any errors.
-
I found my way to the FIDO2 page (Manage AD > Security > Authentication Methods > FIDO2) and enabled it. There weren’t any clear directions about how exactly to test/use/check any of this so I tried the “Security Key” sign-in option in Windows Account Settings, gave it the ol’ boop, and tried to login. No dice, no reaction on the lock screen. No change after reboot.
-
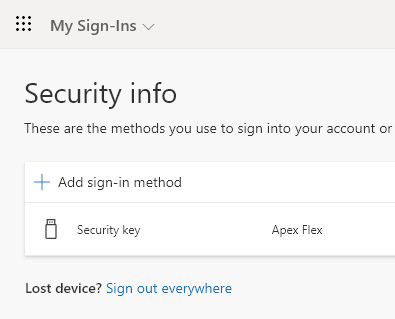
After a bit of reading around, I realised I had to register the security key online, via this page. Previously, when I accessed this page, I was told that my account was not recognised. After signing up for Azure, I was now able to login here. I tried to add my key, but ran into an error. There was no message at all, just a “correlation ID” (which you can view in the Azure portal under “Audit Logs”, after a few minutes have passed).
-
After a bit more reading around, I attempted to manually get, and add, the Apex Flex FIDO2 AAGUID to the “Configure” page in Azure AD’s FIDO2 setup. I managed to snag it as a base64-encoded AAGUID from one of the webauthn test sites, converted it to a traditional GUID, and entered it into Azure AD. No change when I tried to register my Apex.
-
After even more reading, I found a Github thread where it was mentioned that “Enforce attestation” needed to be disabled for Azure AD FIDO2 to function, for some other FIDO2 implementation. I tried this, and it worked! I was able to add my Apex Flex as a sign-in option. Login via Chrome & Edge was working beautifully, using my personal Microsoft account’s email address.
-
After rebooting (for no reason other than making sure my PC had “current AD config”), I attempted login with my Apex Flex. Once it was recognised, my profile picture disappeared, and I saw “Other User” instead. I entered my security pin, and Windows created a brand new account for me. WTF.
-
I logged back into my actual account, and deleted the new one. I dug around more and figured out that it was the “principal name” of my user in Azure AD. I have a custom domain for my account, so that’s not unexpected. Microsoft had generated me one that was completely different to my actual email address. I registered my domain with Azure and updated my principal name. Another reboot later, and I attempted login again. Same thing, except now, the new user had a name that made sense.
-
Switched back to my normal account and I noticed that the “new account” isn’t visible in any control panel, settings window, nor console command. The user profile folder exists, but otherwise this user doesn’t. No idea what’s going on here and I’m concerned that I may have to re-create my user account just to get this working via Azure AD.
I enjoy dicking around with stuff like this, but at the moment I think I’m at a brick wall. My limit for jank and “special setup” ends at requiring me to move user accounts on this PC, so for now I’m gonna sit tight and see what happens.
So close!