I need a custom LUA script written for the proxmark3 and so I’m looking around for someone who might be able to assist?
What are you looking to do? I’ve been writing a Lua script to write NDEF to the flexMN, so I’ve been messing around with it recently, would be happy to help if I can.
I need to serialize a bunch of blank T5577 chips in a way that isn’t mind numbing… basically issue the command
lf em e410 clone --uid 01020300405
but in a way I can serialize the UID from a particular starting point… something like
script run custom_t5577_series --start 0000000001
where I can either press the button on the board to write the next one;
- put tag on LF coil
- issue command
- script waits for button press
- place next tag on LF coil
- press button
- script increments UID and writes
- script waits for button press
- etc.
Or, if acting on button presses is not possible via script, perhaps a serialization file where it contains a starting number like 0102030405 and i issue the script command
script run custom_t5577_series --file emStart
and then it writes the UID and increments the number in the file and exits… then I can simply replace the tag, hit the up arrow and enter to run it again… just something that will remove the tedium of having to backspace and update the UID manually every time I run the command. I know it’s only a few keystrokes more, but its mind numbing hahah
You would be better served with an external script driving the PM client. I tried to implement this sort of thing in LUA and quickly ran into limitations. I ended up using the client as a backend, which is trivial and lets you do anything you can do on the command line, but in an automated way
If you want to see how that goes, look at the client/pyscripts/theremin.py script in the PM3 repo - which I wrote.
What release are you using? I’m looking into this at the moment and I can’t find that command - or anything that looks like it.
Using 4.9237 here.
EDIT: Ah nevermind, found it. Under t55xx
EDIT2: Hmm no I didn’t find it in fact
EDIT3: Is it that? lf em 410x_write 0102030405 1
Here’s your script (not LUA, external Python). Tested in Linux only, as I don’t have Windows. Sorry…
t5577_serializer.zip (2.4 KB)
I would have pasted it inline in the post, but Discourse seems to choke on something in the code. So it’s a ZIP.

yeah ProxSpace is very lacking when it comes to bundled modules…
I will see if there is a way to do this, and failing that I can explore a virtualized linux guest
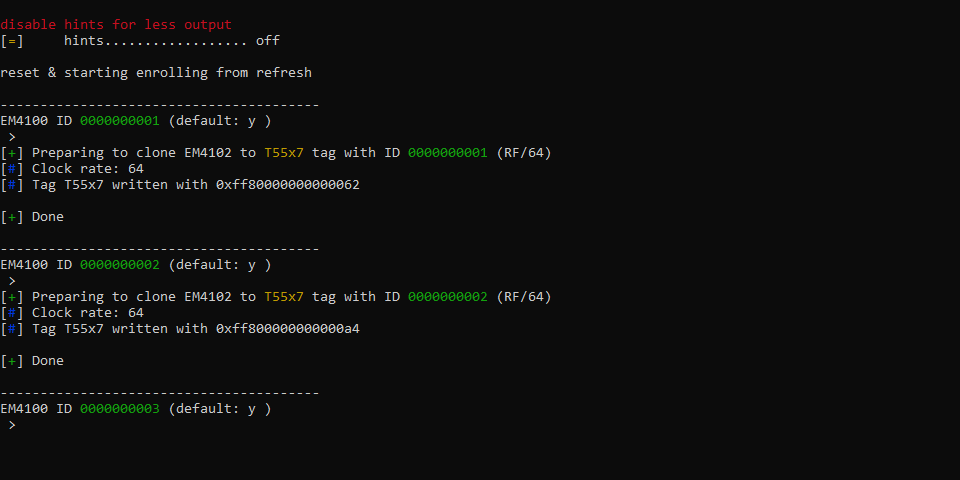
well while I was messing around with getting python modules to work, iceman bumped this to the firmware;
script run lf_em4100_bulk -h
// start with...
script run lf_em4100_bulk -s 0000000001
// continue old session...
script run lf_em4100_bulk -c
Just for you?
Not to rain on your parade, but I might point out that the script from yours truly actually re-reads the EM after writing to check it was written properly. So maybe don’t discard it too quickly ![]()
Aside from that, cool Iceman. And useful too, because good luck doing LF stuff in LUA with the client.
And yeah, get yourself a Linux box. It’s just a matter of installing VirtualBox and Linux Mint or Ubuntu or something. 2 hours tops and then you’re not stuck with Windows no more.
I believe USB drivers / high speed things like the proxmark don’t work very well with virtual instances, but I could be wrong
It does for low-latency stuff. But no issues with USB serial adapters otherwise - which is what the Proxmark USB connection is. I’ve used it many times without any issues in Linux as a guest OS, and in Windows as a guest OS, and most of the Proxmark-related scripts I posted in this forum were made in the Linux guest.
yeah ![]() He also went ahead and put in an HID bulk script too lf_hid_bulkclone.lua… but we hit a snag with lua in ProxSpace only running 32b so the first byte of the ID must be 00 … would work find in mac/linux/etc.
He also went ahead and put in an HID bulk script too lf_hid_bulkclone.lua… but we hit a snag with lua in ProxSpace only running 32b so the first byte of the ID must be 00 … would work find in mac/linux/etc.
actually i think he added checks to the clone commands as while back… but the python script is much appreciated… depending on if i can get proxspace to support 64b lua scripting or not, i may end up using it after all!
yeah i have a few linux guests set up already… i will probably put something together for “rfid stuff” and just go that route
for virtualbox there is also an advanced USB pack you can install that enables things like USB 3.0 and I drastically helps USB speeds… but for whatever reason it’s not included in the virtualbox initial install… probably due to licensing.
Well, the “work” isn’t all wasted: I’ve been meaning to release some kind of generic expect scripter to drive the Proxmark client anyway - one that’s truly multiplatform: the issue you’re having with my script I think is that Windows probably doesn’t support Unix-style PTYs, even with Python wrapping around it. This could be the basis of that.
Exactly that. Also be aware that Oracle has started looking to companies using virtualbox as a potential revenue stream. The company I work for got a licence demand which ended up with the few people using virtualbox having to switch to other products.
And this is why the raspberry pi add on for Proxmark3 is such a good idea. I was thinking of a similar concept with a small display and a couple of buttons on a pi zero 2 to be able to drive the Proxmark3.
Proxmark changed the hitag2 password with an error. Can someone help me create a script to find the password?
lf hitag reader --21 -k A ( A= selected range from-start to end) step -1
I know it can take a long time. Can someone change me this lua file (hf_ntag_bruteforce.lua) to count down from 0xFFFFFFFF to 0x00000000 ???
command = 'lf hitag reader --21 -k %08X'
msg('Bruteforcing Paxton Passwords\n\nStart value: '..start_id..'\nStop value : '..end_id..'\nDelay between tests: '..timeout..' ms')
for hexvalue = start_id, end_id, -1 do
if core.kbd_enter_pressed() then -- abort if key is pressed
print("aborted by user")
break
end
You can close the topic. I found a solution
Thanks for sharing the solution!