Alright, so i finally found someone who is willing to install the flex for me, so i went ahead and checked if i can get the features i want to work.
Fortunatly applet discovery seems to work by now, so selecting and installing them doesn’t require manual codes anymore.
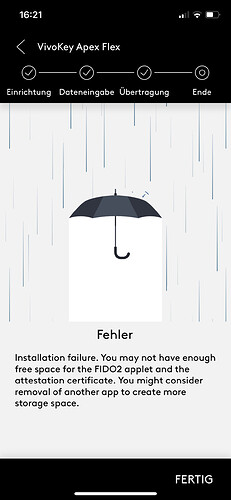
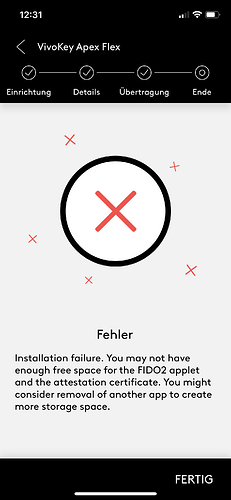
Now, when i try to install either the FIDO2 or U2F app, i get this message:
With the U2F it instantly throws an conection error in addition, with the FIDO2 it gives a checkmark like this:
And that, even when my Apex doesn’t have anything installed. Detecting installed applets works by now, with other ones i can install, even when removing it from the app and rediscovering it.
Now i have tried to install applets manually in the past, but removed them all again, and now again just to be sure.
Now another issue i had, was to discover that the OTP password applett (which i was able to install) isn’t compatible with the yubi-key app anymore, and neither is the HMAC-SHA1 Generator. After searching the forum, i saw the post explaining that it is due to the added security functionallity of a read-password, which is great, however what’s not great is that neither the VivoKey Authenticator app, nor the APEX manager app is avivable on IOS, so i can’t use the Apex for OTP passwords this way either. (The other beeing FIDO2 + Token Companion app).
I urge you to either release those apps for IOS, or release a legacy applet version that works with yubi-key.
NDEF works fine, but i sadly can’t find any documentation on the applets github, on how to change the tags serial number/ id.
On an unrelated note, my Apex seems to have become a bit brown around the edges, which i don’t remember beeing the case about 4-5 months ago, when i got it. But maybe it’s just the paper reflecting the yellow edges, and playing a trick on my eyes. Is this a cause for concern?
So yeah, i hope someone knows a way to get OTP to work on IOS, i would be very thankfull. ![]()
Let me know if i should run some additional tests.