Hello. Can i use the hmac-applet on a iphone?
You can install it yes, but use it? Can you elaborate what you want to do?
If you want to use a HMAC-SHA1 protected KeePass (XC) password database on iOS, both popular apps KeePassium and Strongbox support that. However not tested by me (yet) - I’d appreciate any test reports.
[1] Create a New YubiKey Protected Database - Strongbox
[2] YubiKey hardware keys | KeePassium
I may have misunderstood what it is used for. I thought it was the same function that generates a string on a webpage when i tap a yubikey with my phone
actually yes this is what it will do… generate a string… but how it gets “typed” into a website is probably based on a yubico app on your phone… in theory Apex with this applet on should operate identically to the yubikey with the yubico app… but they might be trying to do extra checks now that could derail this. Have you tried it?
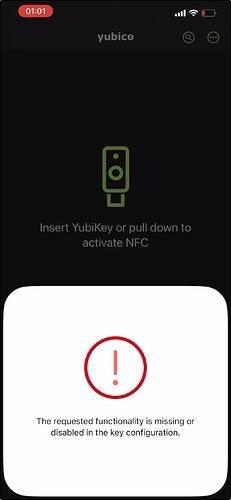
I see an error message that the function is not activated on this yubikey
unfortunately I think yubikey is taking steps to better identify their legitimate products from other products that might be emulating yubikeys. this has recently happened with their OTP authenticator app for example. we may need to explore doing something similar to this in our apex manager app.
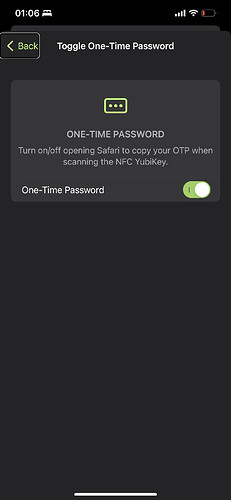
@StarGate01 @yeka - i’m not sure how it copies the OTP to Safari on Apple, but would putting the output into the clipboard be a bad thing security wise?
@hoker - I’m thinking we consider putting the ability to read out OTP data from hmac key slots with keys in them and offer the option to copy to clipboard with a tap?
It generates a random ndef like my.yubico.com redirect
Yubico recently published an all new Authenticator based on a new Codebase (Flutter). I don’t think breaking compatibility was intentional, then new version probably just has a few kinks to work out. I plan to debug an patch this eventually.
Also, don’t confuse HMAC-SHA1 and TOTP. HMAC requires a challenge to produce an answer, see also flexsecure-applets/docs/5-otp-naming.md at master · DangerousThings/flexsecure-applets · GitHub
Ok so a couple things… first is that what is being output when a yubikey is touched is called a YubiOTP and it’s a custom protocol for making up a modhex output from yubikeys. It’s not standardized and it’s not hmac-sha1
The other thing is the NFC NDEF output. That would require a whole new applet to support both YubiOTP and NDEF output. We’re not sure what the total use cases would be for this, so we are not going to develop it for Apex.
However, if you find interest in this application, it can be developed by others and we could publish it for Apex.