There is confusion because they are making it confusing.
Fido was originally a two-factor technology, which is why the first Fido protocol is called u2f… stands for universal 2-factor.
Fido2 came out and it was designed as a passwordless login technology. However, there are many extensions which some relying parties may or may not require. For example the use of a PIN code or user presence of some sort or hmac support… all of these are extensions and they are basically optional. Another optional extension is u2f fallback. This allows old relying parties to use new security keys with fido2 in a u2f capacity.
Because that is a big mess, the mobile phone industry, namely Google an Apple who want to own every aspect of your identity and security, basically carved out a term for themselves called the passkey and worked with the Fido alliance to effectively write a standard after the fact that lets them do this thing.
A passkey is nothing more than a fido2 resident key. That means a special key for a particular relying party is created and stored on the token. That token can be in Apex chip, a yubikey, my mobile phone, your laptop (with proper OS support) etc…
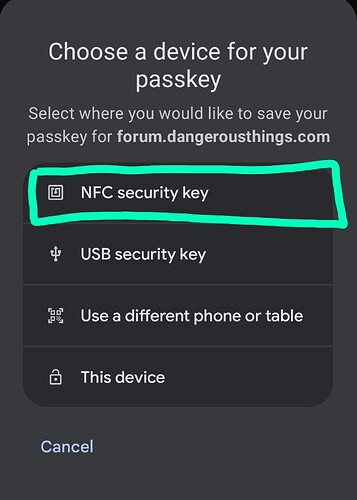
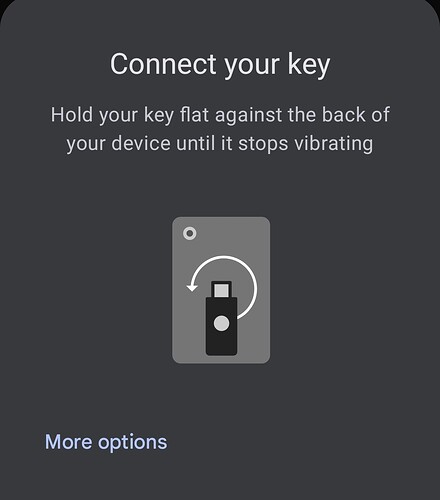
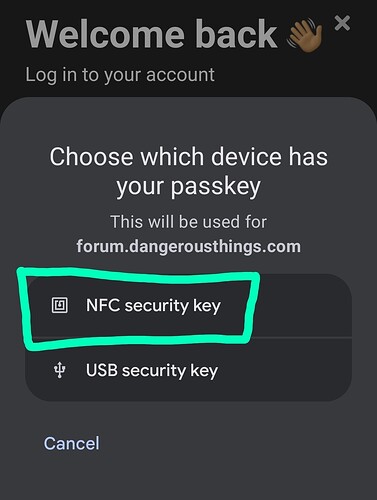
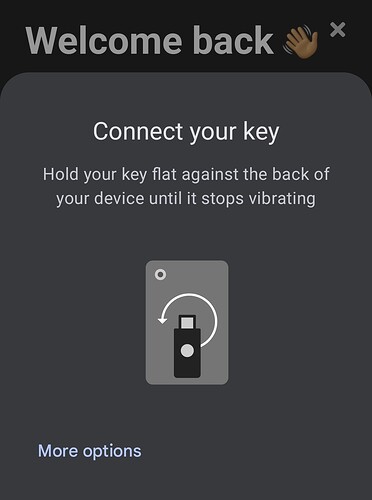
In order to use your Apex as a passwordless authentication token, the relying party needs to support fido2 /passkeys, and not restrict the types of passkey devices it allows (yes a relying party can say it specifically does not want a USB security key or an NFC device as a security key). This usually isn’t a problem though. In addition to this, the entire connectivity chain from browser to operating system to hardware drivers also need to basically be on the same page so that your operating system, when challenged for a Fido authentication, will present a contactless option or at least facilitate a contactless interaction.
So to clarify… u2f is designed as a two factor technology and has no pin code extension or standardized capacity to secure the u2f token. This is why you have to enter a username and password in addition to presenting your u2f token.
Fido2 / passkey passwordless authentication is designed to completely replace both the username and password, although the username is sometimes used to identify accounts. This is why relying parties require some sort of additional user authentication in addition to just having the token. This is typically done using a pin code which is set for the token itself not the relying party. It would be a catastrophe if someone was able to just steal your token and gain access to everything… so a pin code system is the most common method of ensuring the owner is the one wielding the token.
You can use a fido2 token for passwordless authentication without storing a resident key on the token. The public key is used and a challenge responses saved by the relying party is checked during authentication. This allows an infinite number of websites to use the same security key without any storage impact on the token… but this is a non-resident key and it is not a passkey.
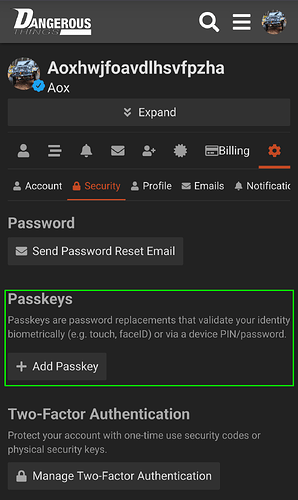
Passkeys, or in fido2 parlance a resident key, is designed so that the relying party gets a unique key and doesn’t have to store anything because the token is storing the unique user data.
The advantage to a passkey of course is that this can be stored on a phone and synchronized with cloud services and used across multiple phones if you have multiple devices… in fact they just recently created an import-export portability standard for the private keys, although the standard is filled with Swiss cheese holes because again they are creating a standard behind the work already done by Google and apple to allow this on their platforms. The one advantage for a token like Apex is that you get to see a list of relying parties because you can manage the stored keys (with proper software which is rare and typically not sure friendly, but we’re working on something). The downside of course is that you will run out of space because each key takes up memory.
On the Apex, each key takes around 330 bytes give or take pending on memory segmentation. As you can imagine this allows for a good number of keys to be stored even on a chip like the Apex.