I saw this thread about this topic, but I couldn’t find an answer for what I’m looking for.
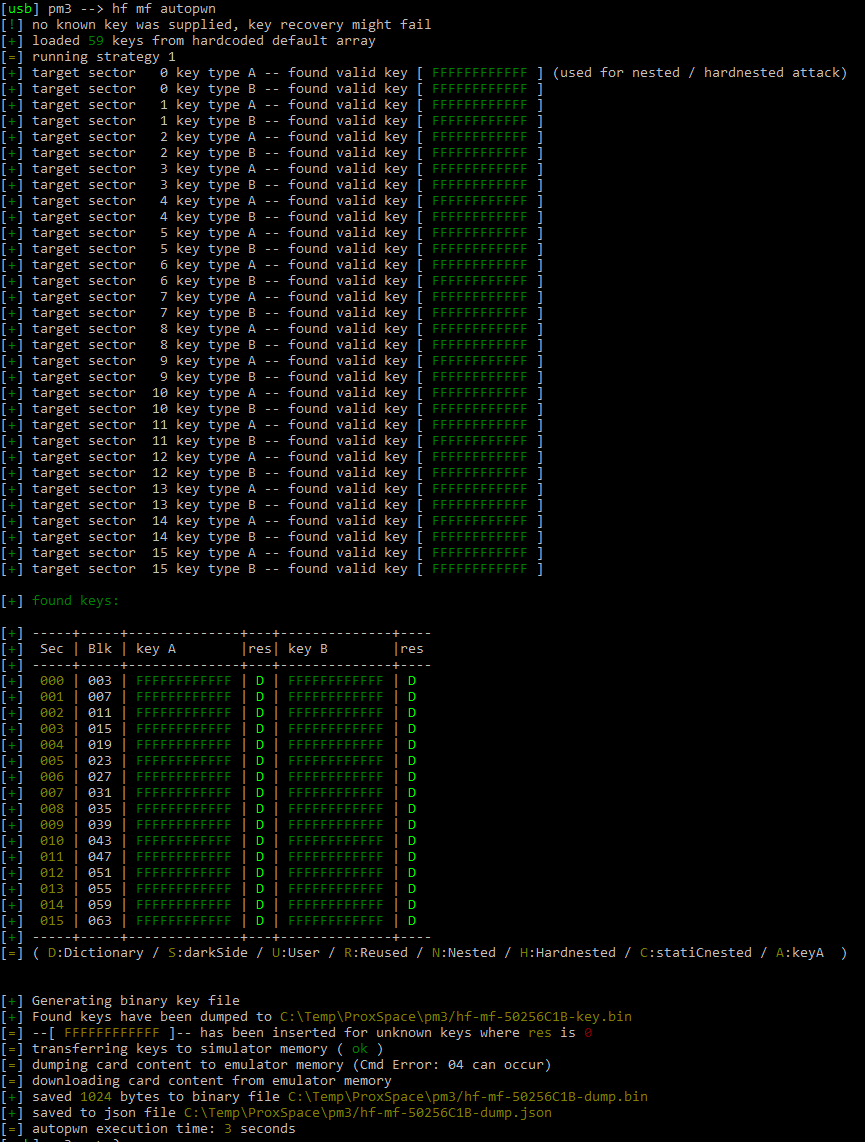
I am trying to dump a card’s content using the hf mf autopwn command.
However, the output files are only json and bin:
[+] Generating binary key file
[+] Found keys have been dumped to C:\Temp\ProxSpace\pm3/hf-mf-50256C1B-key.bin
[=] --[ FFFFFFFFFFFF ]-- has been inserted for unknown keys where res is 0
[=] transferring keys to simulator memory ( ok )
[=] dumping card content to emulator memory (Cmd Error: 04 can occur)
[=] downloading card content from emulator memory
[+] saved 1024 bytes to binary file C:\Temp\ProxSpace\pm3/hf-mf-50256C1B-dump.bin
[+] saved to json file C:\Temp\ProxSpace\pm3/hf-mf-50256C1B-dump.json
[=] autopwn execution time: 3 seconds
Please advise, thanks!
I’m attaching a screenshot of the entire output…