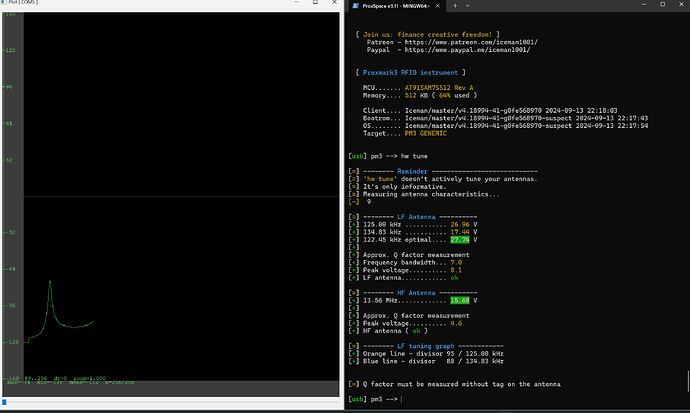
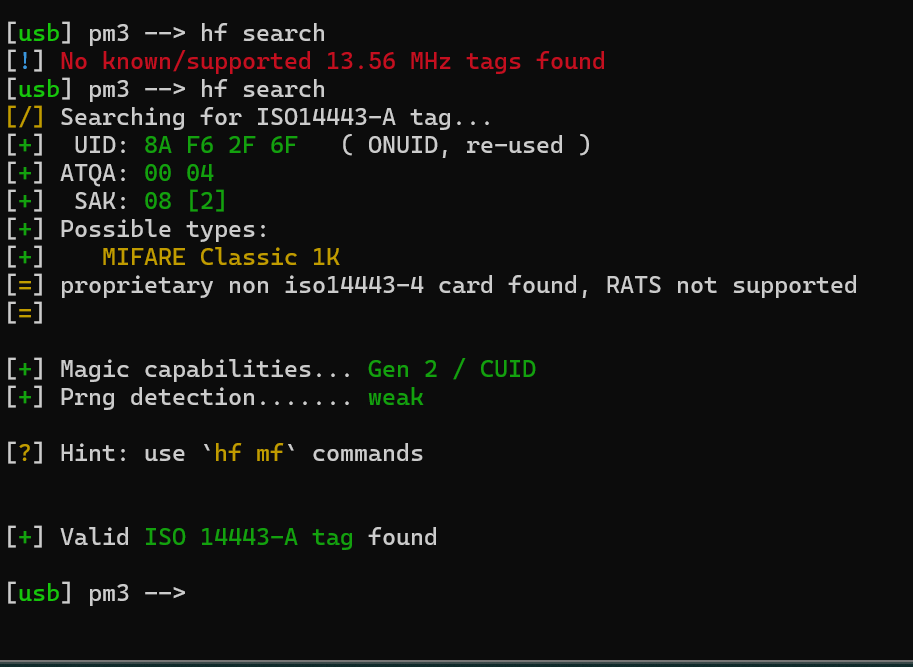
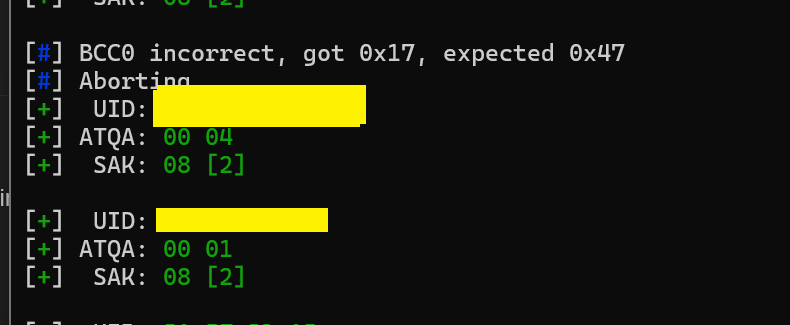
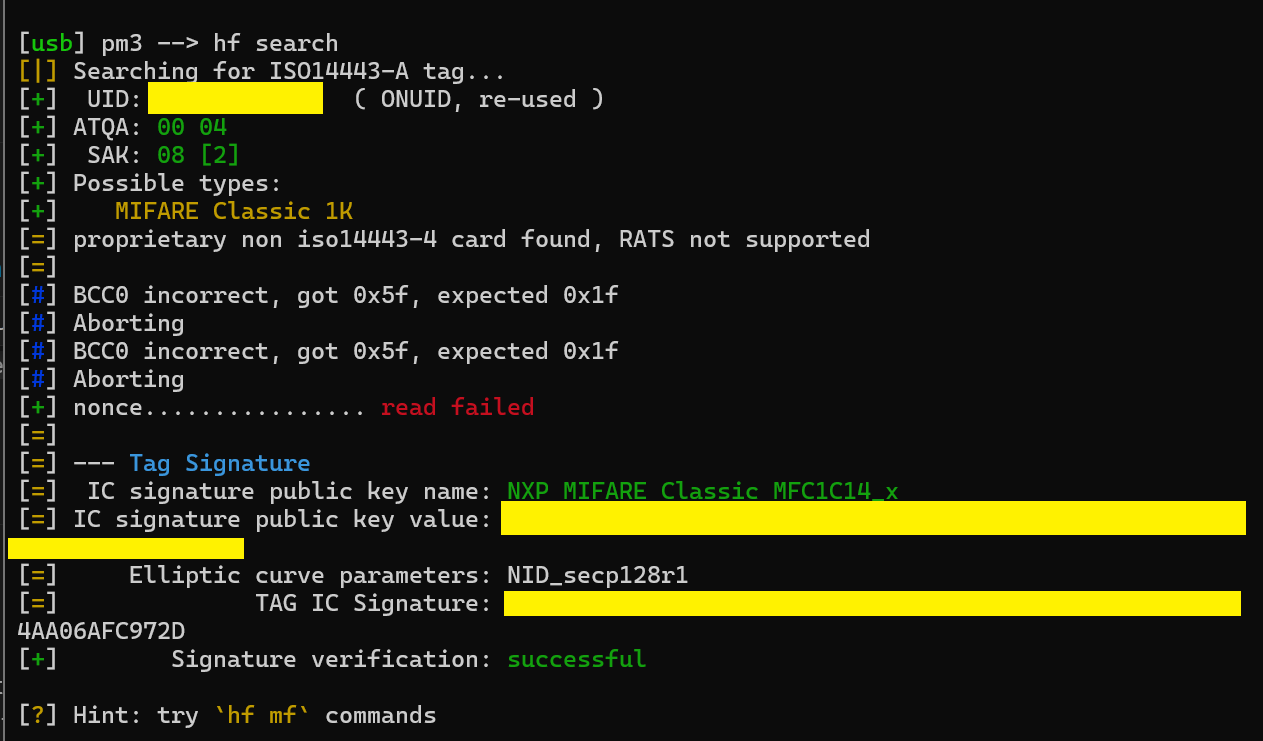
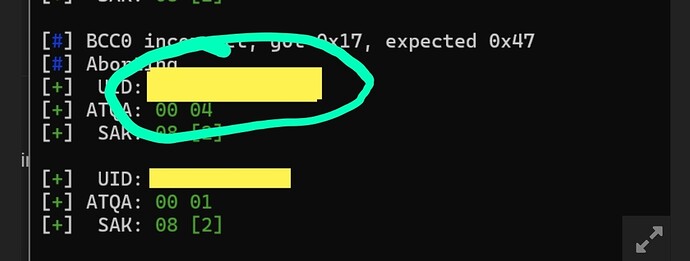
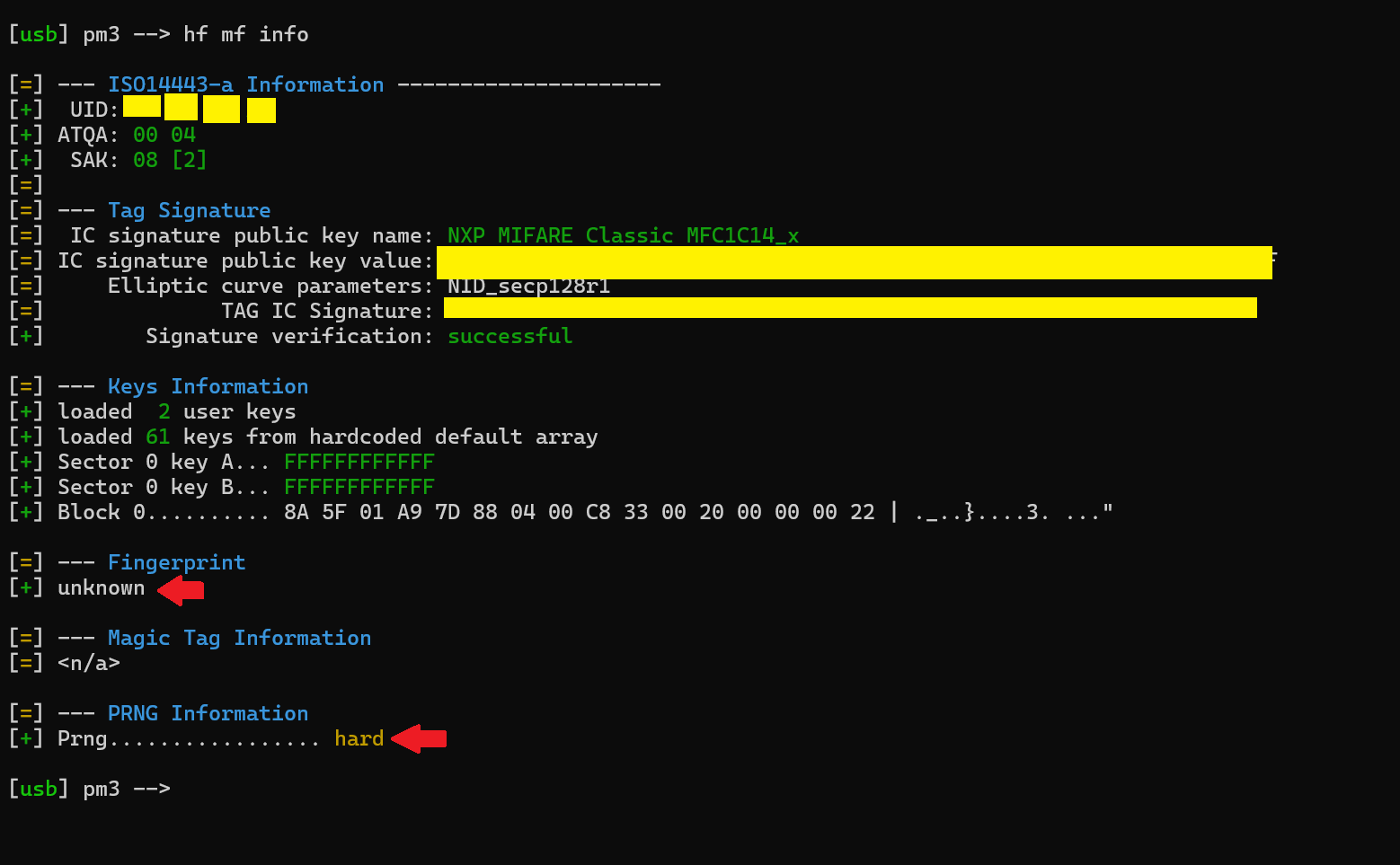
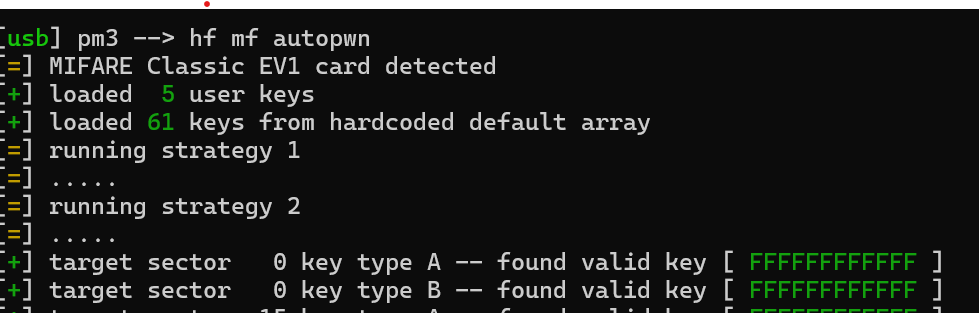
Going to be uploading the TagInfo scan here in case it comes in handy. My ultimate goal is to copy this fob to a card of some sort. Hopefully one that the PM3 came with.
** TagInfo Scan (version 5.0.0) 14-Sep-24 10:05:21 **
Report Type: – IC INFO ------------------------------
IC Manufacturer:
NXP Semiconductors
IC Type:
MIFARE Classic EV1 (MF1S50)
– NDEF ------------------------------
No NDEF Data Storage Present:
Maximum NDEF storage size after format: 716 bytes
– EXTRA ------------------------------
Memory Information:
1 kB
- 16 sectors, with 4 blocks per sector
- 64 blocks, with 16 bytes per block
IC Information:
Full product name: MF1S503xX/V1
Block 0 analysis:
UID: XX:XX:XX:XX
- NXP Semiconductors
- Re-used (Old) Non-Unique ID
Check Byte: 0x7D
SAK: 0x88
ATQA: 0x0400
Manufacturer data:
- C8 33 00 20 00 00 00 22 |.3. …"|
- Revision: C8
- Fab: TSMC
- Production date: week 33, 2022
~ PQE0/1: 33 22
Originality Check (asymmetric):
Signature verified with NXP public key
Version :5.0.0
Device Info:
Device Model :Google ( Pixel 3 )
Android OS Version :13
– FULL SCAN ------------------------------
Technologies Supported:
MIFARE Classic compatible
ISO/IEC 14443-3 (Type A) compatible
ISO/IEC 14443-2 (Type A) compatible
Android Technology Information:
Tag description:
- TAG: Tech [android.nfc.tech.NfcA, android.nfc.tech.MifareClassic, android.nfc.tech.NdefFormatable]
- Maximum transceive length: 253 bytes
- Default maximum transceive time-out: 618 ms
Detailed Protocol Information:
ID: XX:XX:XX:XX
ATQA: 0x0400
SAK: 0x08
Memory Content:
Sector 0 (0x00)
[00] r-- 8A 5F 01 A9 7D 88 04 00 C8 33 00 20 00 00 00 22 |._..}…3. …"|
[01] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |…|
[02] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |…|
[03] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 1 (0x01)
[04] ??? – – – – – – – – – – – – – – – –
[05] ??? – – – – – – – – – – – – – – – –
[06] ??? – – – – – – – – – – – – – – – –
[07] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 2 (0x02)
[08] ??? – – – – – – – – – – – – – – – –
[09] ??? – – – – – – – – – – – – – – – –
[0A] ??? – – – – – – – – – – – – – – – –
[0B] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 3 (0x03)
[0C] ??? – – – – – – – – – – – – – – – –
[0D] ??? – – – – – – – – – – – – – – – –
[0E] ??? – – – – – – – – – – – – – – – –
[0F] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 4 (0x04)
[10] ??? – – – – – – – – – – – – – – – –
[11] ??? – – – – – – – – – – – – – – – –
[12] ??? – – – – – – – – – – – – – – – –
[13] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 5 (0x05)
[14] ??? – – – – – – – – – – – – – – – –
[15] ??? – – – – – – – – – – – – – – – –
[16] ??? – – – – – – – – – – – – – – – –
[17] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 6 (0x06)
[18] ??? – – – – – – – – – – – – – – – –
[19] ??? – – – – – – – – – – – – – – – –
[1A] ??? – – – – – – – – – – – – – – – –
[1B] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 7 (0x07)
[1C] ??? – – – – – – – – – – – – – – – –
[1D] ??? – – – – – – – – – – – – – – – –
[1E] ??? – – – – – – – – – – – – – – – –
[1F] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 8 (0x08)
[20] ??? – – – – – – – – – – – – – – – –
[21] ??? – – – – – – – – – – – – – – – –
[22] ??? – – – – – – – – – – – – – – – –
[23] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 9 (0x09)
[24] ??? – – – – – – – – – – – – – – – –
[25] ??? – – – – – – – – – – – – – – – –
[26] ??? – – – – – – – – – – – – – – – –
[27] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 10 (0x0A)
[28] ??? – – – – – – – – – – – – – – – –
[29] ??? – – – – – – – – – – – – – – – –
[2A] ??? – – – – – – – – – – – – – – – –
[2B] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 11 (0x0B)
[2C] ??? – – – – – – – – – – – – – – – –
[2D] ??? – – – – – – – – – – – – – – – –
[2E] ??? – – – – – – – – – – – – – – – –
[2F] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 12 (0x0C)
[30] ??? – – – – – – – – – – – – – – – –
[31] ??? – – – – – – – – – – – – – – – –
[32] ??? – – – – – – – – – – – – – – – –
[33] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 13 (0x0D)
[34] ??? – – – – – – – – – – – – – – – –
[35] ??? – – – – – – – – – – – – – – – –
[36] ??? – – – – – – – – – – – – – – – –
[37] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 14 (0x0E)
[38] ??? – – – – – – – – – – – – – – – –
[39] ??? – – – – – – – – – – – – – – – –
[3A] ??? – – – – – – – – – – – – – – – –
[3B] ??? XX:XX:XX:XX:XX:XX --:–:-- – XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 15 (0x0F)
[3C] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |…|
[3D] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |…|
[3E] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |…|
[3F] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
r/R=read, w/W=write, i/I=increment,
d=decr/transfer/restore, x=r+w, X=R+W
data block: r/w/i/d:key A|B, R/W/I:key B only,
I/i implies d, *=value block
trailer (order: key A, AC, key B): r/w:key A,
W:key B, R:key A|B, (r)=readable key
AC: W implies R+r, R implies r