Okay, so you are on the right track
.
A couple of things.
It looks like you have an ultralight rather than a classic.
Can you do me a favour and scan with TagInfo
So when it comes to implants you will be looking at the FlexMN (Magic NTAG)
It is capable of emulating the Ultralight.
I don’t have one myself so I can’t help you much around specifics.
I do hope to get one in the future, but until then
Here is the link with some info
With regards to your Proxmark3 output above, you have done everything perfect, however, now it appears to be an ultralight, we have to tweak your commands.
As it says at the bottom of you post
So
HF
MiFareUltralight
Info
When it give you a result like you one above (may be different for the Ultralight commands) again I am not infront of my proxmark.
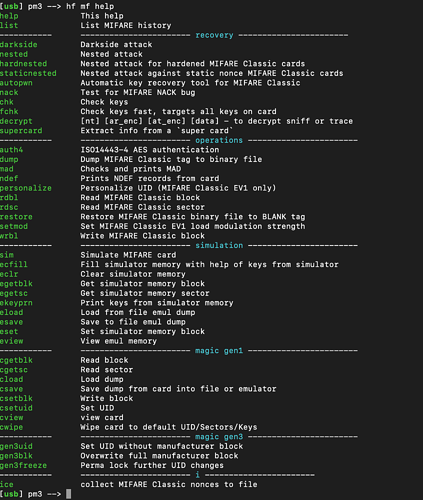
You would simply look at what you are trying to do (blue/green eg. Recovery or operations etc)
Then find the command (green) you want and add that to you previous command
So example for mifare classic
hf mf dump
Which would result in
Is that starting to make sense?
So if you can check you card with taginfo
Then you can try your commands with the
hf mfu commands