Hi all,
So I recently got into the whole proxmark space and have successfully cloned my iClass card to the redteam 2k and 16k cards. I got my hands on a ISO 14443-A wearable and I’d like to copy it to that. The readers at my work are configured to accept it, so it’s just a matter of programming the card properly.
I was able to decrypt the data on my card and get the wiegand binary, which I presume would be what the reader is looking for. The question is, how do I program this onto the new card? Does wiegand encode do what I want? I tried the hf mf command for writing the UID but it wanted 5 or 7 bytes, and my data was 9 bytes. I did already use autopwn successfully and read the 14443 card, which is a good first step.
Thanks!
Take a look at the hf mf encodehid command, it should be what you want
2 Likes
The command looks like exactly what I need. I ran it and it seems to have gone fine. However, I notice that when I scan it with an HID reader, the facility code and card number don’t come up as the right numbers.
I ran:
hf mf encodehid --fc xxxx --cn xxxxxx --w C1k35s
since my original card format is HID Corporate 1000 35-bit std but the numbers I get when I scan are totally different. It does read/decode properly though which is a good start. Any ideas?
1 Like
Last I heard the PM3 was still a little buggy with formats other than H10301
Unfortunately, I have never played with Corporate 1000 and don’t have any credentials to test on at the moment
I would probably try encoding the same FC and CN but with the H10301 format and just see if your readers are set up to work with it as well, you might get lucky
When I get a chance I’ll see if I can find someone else’s C1000 dump and mess with it
1 Like
Unfortunately, it seems it won’t let me encode in any other format. I’m assuming it’s because the number of bits isn’t right. I can give you my C1000 dump privately if you’re interested in poking around.
That makes sense, my bad!
I was able to successfully clone a C1k35s Fc and Cn to a mifare classic card by issuing the following commands:
hf mf autopwn
hf mf wipe
hf mf encodehid --fc xxx --cn xxxxxx -w c1k35s
Can you expand on this? How are you checking to see if the encoding was completed correctly?
I’ve been looking at hf mf cview to see what’s on the card and if it encoded properly. I did notice that encodehid adds a few other extra bits in block 5 and I’m not really sure what they do.
I’ve also tried writing manually to block 5 just the data as encoded by wiegand encode, which is nearly identical to the decrypted data from block 7 on my HID card. Thinking the difference may be why it wouldn’t work, I also tried just copying the block 7 data directly over, but no matter what I do, the numbers won’t come up right on the reader.
Looking at the decrypted binary from my original card and comparing to what was encoded by wiegand encode, the whole string matches except the very left most byte which is a 9 on my original card and a 1 as encoded by wiegand encode. It’s just one flipped bit. Maybe this is part of the problem?
For whatever reason, the contents of block 5 are just nowhere even remotely close to what comes through on the HID reader.
If your HID reader is outputting plaintext wiegand data it’s definitely not going to look like block 5
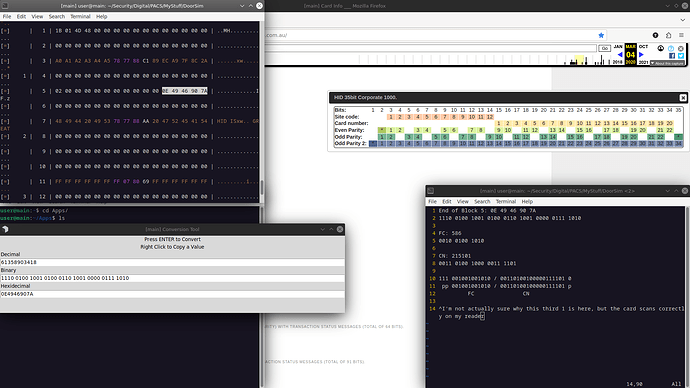
Here’s a screenshot that might sort of explain what’s going on here, does it look like it might be what’s happening for you?
On the top left we see the card dump, I’ve highlighted the part we’re interested in.
To the right of that we see the actual C1k35s format.
and under that some conversions to binary to show that everything matches up for me
I can confirm that this card scans correctly on an HID reader
Actually that first 1 that was throwing me off is an important part of the preamble, definitely don’t forget to include that if you’re going to convert back to hex
1 Like
Ah ok. I was also getting a bit confused about the extra 1. But anyway. No im not outputting plaint text from the reader. It is connected to an arduino with an HID wiegand library that then outputs the FC and CN. The problem is that the FC and CN dont match the original card at all. But converting those two numbers to binary and comparing them to the C1k35s format, they look similar, just shifted over slightly and missing bits here and there. Namely the end of the CN has a lot of bits zeroed out. The arduino also says its receiving less bits than it should be. 32 instead of 35. I’ll tinker with this more later today and see if I can get some data to show you.
1 Like
Alright, so I’ve abandoned my effort to anonymize the numbers here since the troubleshooting has become more advanced. My original card had FC 3646 and CN 352741. Block 7 on my HID card reads 9C7CAC3CB, which now perfectly matches block 5 on my MF card using encodehid after a full wipe and autopwn. My HID card when scanned gives the right FC and CN. When I scan the MF card, I get 2936 for FC and 22016 for CN. See below for dump of MF card:
[+] View magic Gen1a MIFARE Classic 1K
[=] .................................................................
[=] -----+-----+-------------------------------------------------+-----------------
[=] sec | blk | data | ascii
[=] -----+-----+-------------------------------------------------+-----------------
[=] 0 | 0 | 00 56 78 BB 95 08 04 00 02 B2 1E 24 23 27 1E 1D | .Vx........$#'..
[=] | 1 | 1B 01 4D 48 00 00 00 00 00 00 00 00 00 00 00 00 | ..MH............
[=] | 2 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 3 | A0 A1 A2 A3 A4 A5 78 77 88 C1 89 EC A9 7F 8C 2A | ......xw.......*
[=] 1 | 4 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 5 | 02 00 00 00 00 00 00 00 00 00 00 09 C7 CA C3 CB | ................
[=] | 6 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 7 | 48 49 44 20 49 53 78 77 88 AA 20 47 52 45 41 54 | HID ISxw.. GREAT
[=] 2 | 8 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 9 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 10 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 11 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 3 | 12 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 13 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 14 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 15 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 4 | 16 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 17 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 18 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 19 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 5 | 20 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 21 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 22 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 23 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 6 | 24 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 25 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 26 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 27 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 7 | 28 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 29 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 30 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 31 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 8 | 32 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 33 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 34 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 35 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 9 | 36 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 37 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 38 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 39 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 10 | 40 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 41 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 42 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 43 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 11 | 44 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 45 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 46 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 47 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 12 | 48 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 49 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 50 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 51 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 13 | 52 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 53 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 54 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 55 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 14 | 56 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 57 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 58 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 59 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] 15 | 60 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 61 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 62 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] | 63 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......
[=] -----+-----+-------------------------------------------------+-----------------
[?] cyan = value block with decoded value
[?] MAD key detected. Try `hf mf mad` for more details
And then here is the decrypted dump from my HID card:
[=] --------------------------- Card ---------------------------
[+] CSN... EB EE 9E 13 FE FF 12 E0 uid
[+] Config... 12 FF FF FF 7F 1F FF 3C card configuration
[+] E-purse... 05 F6 FF FF FF FF FF FF card challenge, CC
[+] Kd... F3 A4 41 43 EC 8D A0 AA debit key
[+] Kc... FF FF FF FF FF FF FF FF credit key ( hidden )
[+] AIA... FF FF FF FF FF FF FF FF application issuer area
[=] -------------------- Card configuration --------------------
[=] Raw... 12 FF FF FF 7F 1F FF 3C
[=] 12 ( 18 )............. app limit
[=] FFFF ( 65535 )...... OTP
[=] FF............ block write lock
[=] 7F......... chip
[=] 1F...... mem
[=] FF... EAS
[=] 3C fuses
[=] Fuses:
[+] mode......... Application (locked)
[+] coding....... ISO 14443-2 B / 15693
[+] crypt........ Secured page, keys not locked
[=] RA........... Read access not enabled
[=] PROD0/1...... Default production fuses
[=] -------------------------- Memory --------------------------
[=] 2 KBits/2 App Areas ( 256 bytes )
[=] 1 books / 1 pages
[=] First book / first page configuration
[=] Config | 0 - 5 ( 0x00 - 0x05 ) - 6 blocks
[=] AA1 | 6 - 18 ( 0x06 - 0x12 ) - 13 blocks
[=] AA2 | 19 - 31 ( 0x13 - 0x1F ) - 18 blocks
[=] ------------------------- KeyAccess ------------------------
[=] * Kd, Debit key, AA1 Kc, Credit key, AA2 *
[=] Read AA1..... debit
[=] Write AA1.... debit
[=] Read AA2..... credit
[=] Write AA2.... credit
[=] Debit........ debit or credit
[=] Credit....... credit
[=] --------------------------- Tag memory ----------------------------
[=] block# | data | ascii |lck| info
[=] ---------+-------------------------+----------+---+----------------
[=] 0/0x00 | EB EE 9E 13 FE FF 12 E0 | ........ | | CSN
[=] ......
[=] 6/0x06 | 03 03 03 03 00 03 E0 14 | ........ | | User / HID CFG
[=] 7/0x07 | 00 00 00 09 C7 CA C3 CB | ........ | | User / Cred
[=] 8/0x08 | 00 00 00 00 00 00 00 00 | ........ | | User / Cred
[=] 9/0x09 | 00 00 00 00 00 00 00 00 | ........ | | User / Cred
[=] 10/0x0A | FF FF FF FF FF FF FF FF | ........ | | User
[=] 11/0x0B | FF FF FF FF FF FF FF FF | ........ | | User
[=] 12/0x0C | FF FF FF FF FF FF FF FF | ........ | | User
[=] 13/0x0D | FF FF FF FF FF FF FF FF | ........ | | User
[=] 14/0x0E | FF FF FF FF FF FF FF FF | ........ | | User
[=] 15/0x0F | FF FF FF FF FF FF FF FF | ........ | | User
[=] 16/0x10 | FF FF FF FF FF FF FF FF | ........ | | User
[=] 17/0x11 | FF FF FF FF FF FF FF FF | ........ | | User
[=] 18/0x12 | FF FF FF FF FF FF FF FF | ........ | | User
[=] ---------+-------------------------+----------+---+----------------
[?] yellow = legacy credential
[=] Block 7 decoder
[+] Binary..................... 100111000111110010101100001111001011
[=] Wiegand decode
[+] [C1k35s ] HID Corporate 1000 35-bit std FC: 3646 CN: 352741 parity ( ok )
[=] found 1 matching format
Ah! I actually just made a bit of a break through. So I noticed in the UID, the beginning reads 00 56 78 BB. The raw data read off of the MF card by the HID reader is BB 78 56 00. So it seems the reader is looking at UID instead of block 5.
1 Like
Block 5 looks good to me, I don’t think that’s where the issue lies
Try hf mf mad and see what the output is
Mad says there is an HID key in sector 1
Here is the full printout:
[=] --- MIFARE App Directory Information ----------------
[=] -----------------------------------------------------
[=] ------------ MAD v1 details -------------
[+] Card publisher sector 0x01
[=] ---------------- Listing ----------------
[=] 00 MAD v1
[=] 01 [484D] Access Control [HID Global]
[=] 02 [0000] free
[=] 03 [0000] free
[=] 04 [0000] free
[=] 05 [0000] free
[=] 06 [0000] free
[=] 07 [0000] free
[=] 08 [0000] free
[=] 09 [0000] free
[=] 10 [0000] free
[=] 11 [0000] free
[=] 12 [0000] free
[=] 13 [0000] free
[=] 14 [0000] free
[=] 15 [0000] free
Ah poop, I seem to have gone and goofed my test HID reader, it can’t read non-SIO mifare classic cards anymore.
That is to say, I don’t have a way to check the wiegand output anymore to keep troubleshooting 
At this point I am sort of leaning towards it being a reader config error on your side as well, but like I said I just can’t check it at the moment
If I can figure out how to reconfigure this thing I’ll get back to you
1 Like
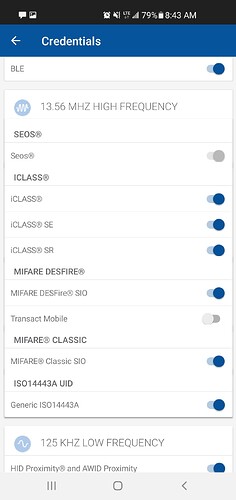
Attached image is the reader config. So it seems it is preferring to read the tag as generic ISO14443A UID as opposed to Mifare classic. As such, its reading the UID instead of block 5. So it seems then that I need to figure out how to encode the right data into the UID. No idea how to do this though.
hf mf csetuid wants 5 or 7 bytes, which is not what my data has. I tried appending a 0 to fill it out to 7 bytes, but the BCC0 check doesn’t pass anymore and the tag can’t be read by the HID reader. I wish it were as simple as disabling ISO14443A on the reader, but I’m not in a position to reconfigure our readers at work.
Have you tried it on one of your work readers yet, or just the one hooked up to your Arduino?
It’s possible they could be configured to accept non-SIO Mifare Classic credentials
1 Like
Nope havent tried it at work yet, I’ve been off all these days. That screenshot was of the one at work actually. But mine is the same reader with the same config
1 Like