Thanks!
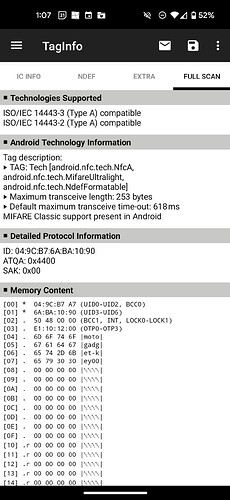
In testing this, I took an NTAG213 fob from the mo-lock NFC product and read it in TagInfo to get memory contents.
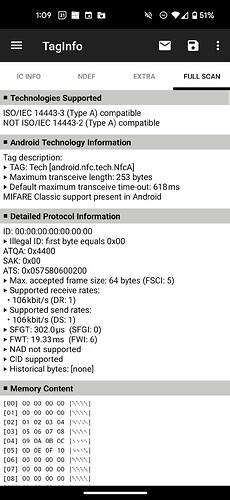
Then I tried to set emulator memory starting with block 0 to match using hf mf eset -b 0 -d 049cb7a76aba109050480000e1101200 and then started emulation.
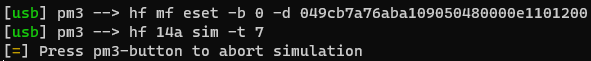
Unfortunately when reading, it did not read any UID or changes memory?