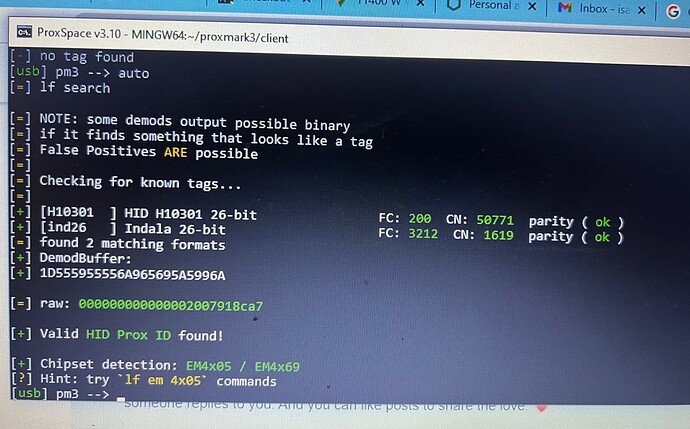
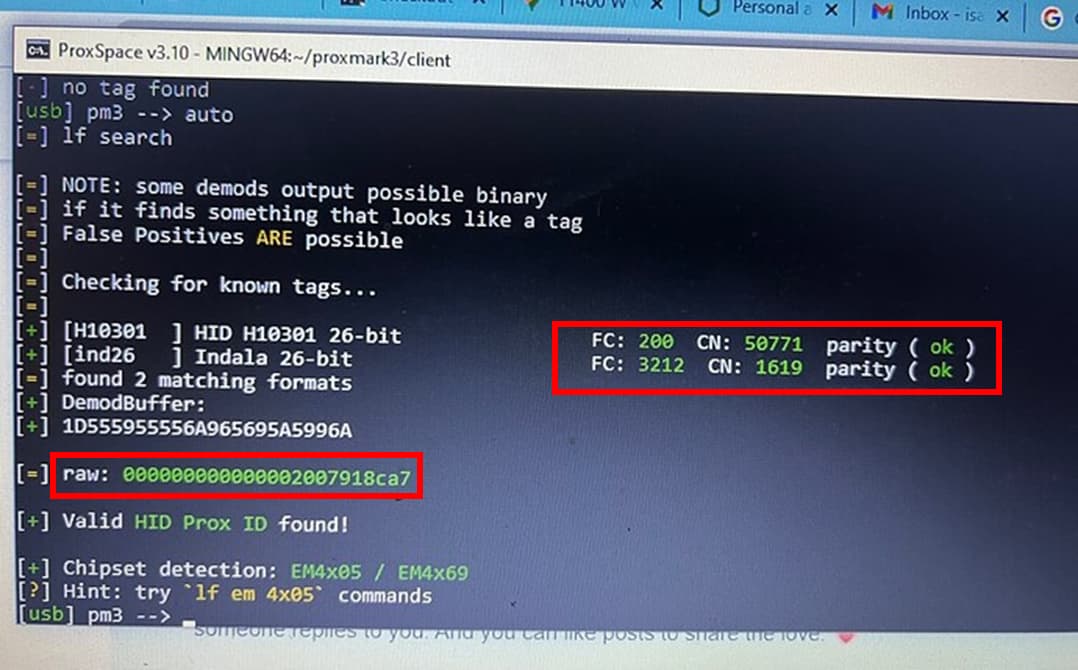
here is a picture of what my proxmark3 reader found as info when i ran the auto command on it.
how do i copy this key ? or which command line do i use to copy it .
thx
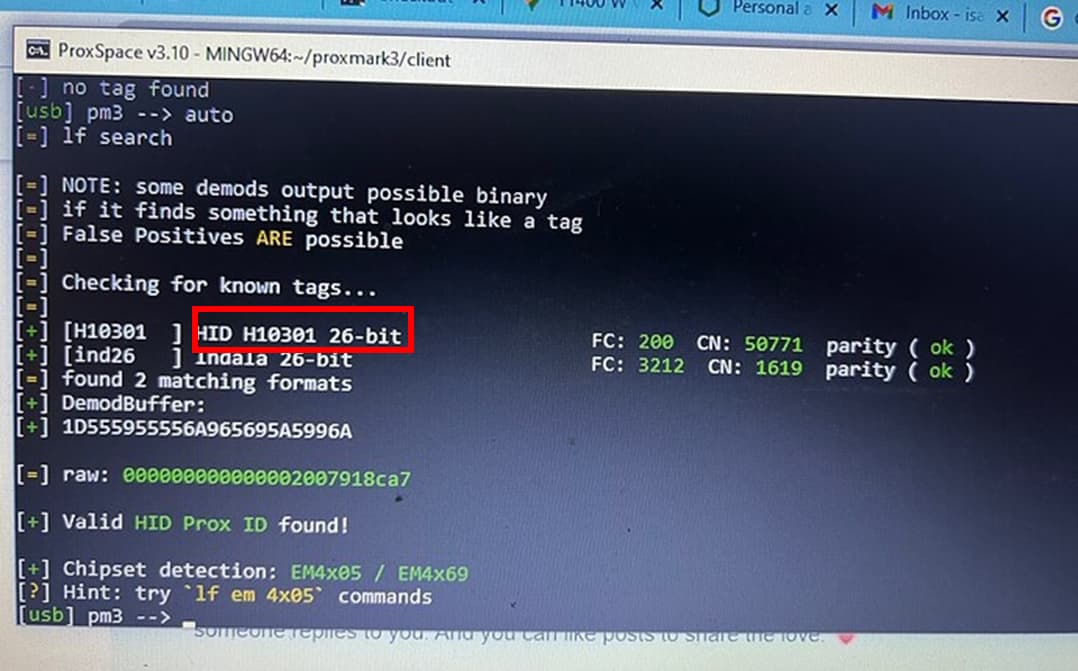
First be sure the ID is consistent across multiple reads… could be noise. Make sure it’s correct and matches each read.
Next if you are sure it’s HID then you’d go
lf hid clone
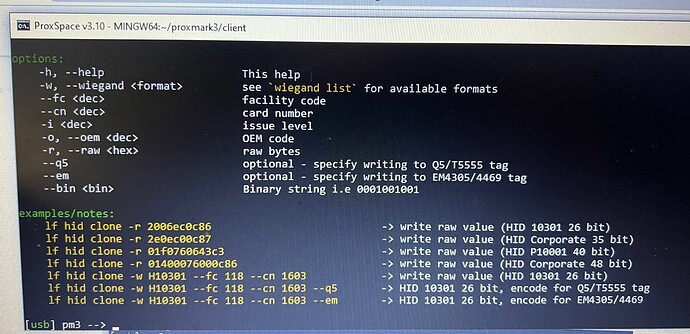
And check the help screen to see your options.
do i need to buy the identical fob key or can a generic fob do?
this is the picture of the original fob
IF you get the repeated same results as Amal asked you to check
THIS is the command you want to send
lf hid clone -r 000000000000002007918ca7
when you have done that, try
lf hid reader to verify
you should get the same results as above
How I got that answer!?
The PM3 steps you through the process and luckily it gives you answers and examples
You knew it was LF
so simply putting in
lf
yields you all the LF options
you knew it was HID
so
lf hid
Gives you the LF HID options
[usb] pm3 --> lf hid
help this help
demod demodulate HID Prox tag from the GraphBuffer
reader attempt to read and extract tag data
clone clone HID tag to T55x7
sim simulate HID tag
brute bruteforce card number against reader
watch continuously watch for cards. Reader mode
you knew you wanted to clone, so
lf hid clone
examples/notes:
lf hid clone -r 2006ec0c86 -> write raw value for T55x7 tag (HID 10301 26 bit)
lf hid clone -r 2e0ec00c87 -> write raw value for T55x7 tag (HID Corporate 35 bit)
lf hid clone -r 01f0760643c3 -> write raw value for T55x7 tag (HID P10001 40 bit)
lf hid clone -r 01400076000c86 -> write raw value for T55x7 tag (HID Corporate 48 bit)
lf hid clone -w H10301 --fc 118 --cn 1603 -> HID 10301 26 bit, encode for T55x7 tag
lf hid clone -w H10301 --fc 118 --cn 1603 --q5 -> HID 10301 26 bit, encode for Q5/T5555 tag
lf hid clone -w H10301 --fc 118 --cn 1603 --em -> HID 10301 26 bit, encode for EM4305/4469
from your screenshot
you can see that ties in with this
lf hid clone -r 2006ec0c86 -> write raw value for T55x7 tag (HID 10301 26 bit)
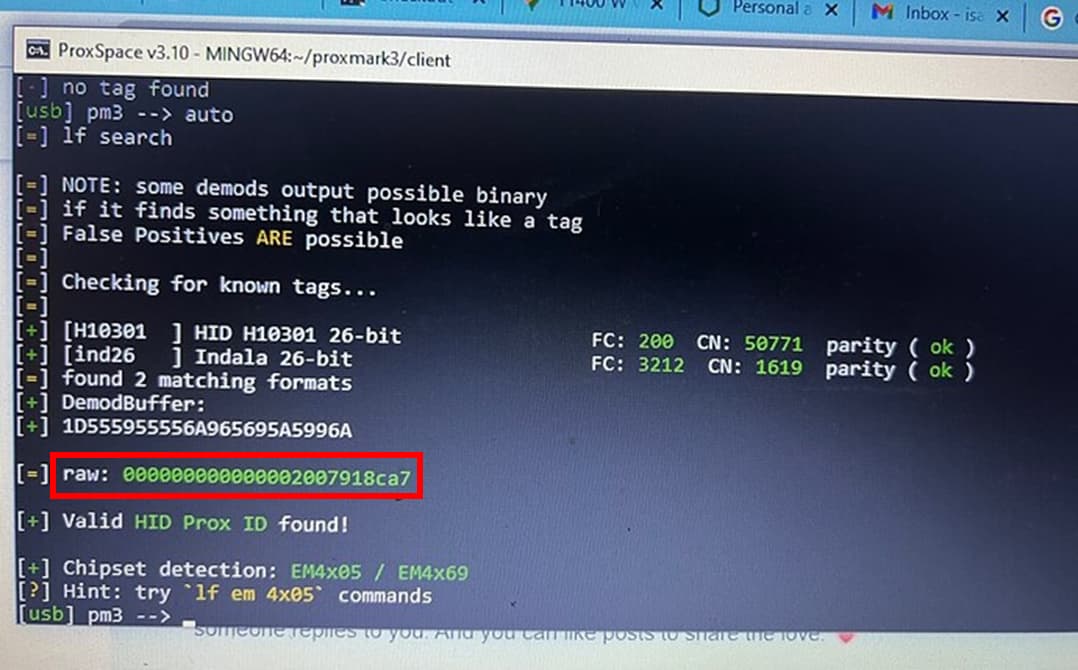
So taking your raw data
we add this to the command line
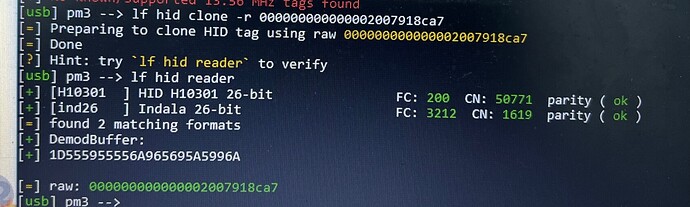
lf hid clone -r 000000000000002007918ca7
and then we check to confirm
lf hid reader or lf search
and we get
[usb] pm3 --> lf hid reader
[+] [H10301 ] HID H10301 26-bit FC: 200 CN: 50771 parity ( ok )
[+] [ind26 ] Indala 26-bit FC: 3212 CN: 1619 parity ( ok )
[=] found 2 matching formats
[+] DemodBuffer:
[+] 1D555955556A965695A5996A
[=] raw: 000000000000002007918ca7
compare this to
And we have a winner baby !
I hope this makes sense, and is easy to follow.
Just remember when writing to an implant, it is important to get good coupling, so do some test reads first to ensure you are in the right place, when you have confirmed this,
DO NOT MOVE, then WRITE
I was composing a reply when you posted this,
can you just do an lf read a couple of times,
make sure the result is the same, then show us the output.
If it is the same as your first post, just follow my “guide” above
What do you have?
A generic T5577 card or tag will work… that’s what I used for your answer
if you have some spare cards lying around, try an
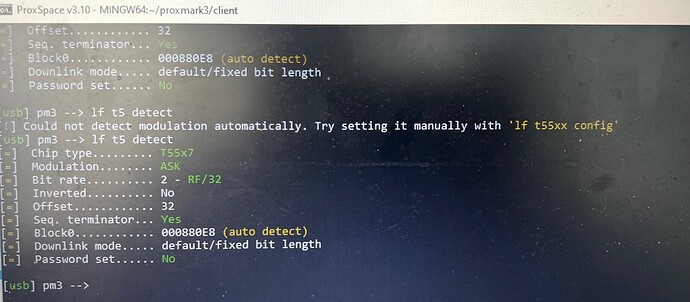
lf t5 detect
That will identify if it has a T5577 chip, if so, you are onto a winner winner ![]()
![]()
thanks for taking time to explain it .
I seem not to have the correct fob keys that are compatible . when i run an auto command on both fobs keys it comes back saying “no data found” so i will have to look for an exact fob key like the picture above online and try those command lines you suggested.
these were the fob keys i had thinking they were compatible but unfortunately there’s nothing on them
Quite possibly they are T5577
But let’s first check that they are LF
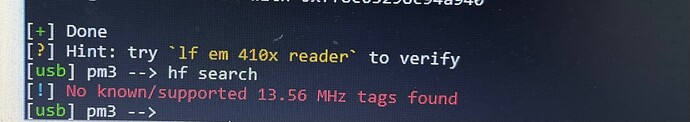
Please put them on the HF antenna ( the underside of the bottom PCB )
then
hf search
If no result
then put it back on the LF antenna ( Top Red coil )
then
lf t5 detect
what does it return?
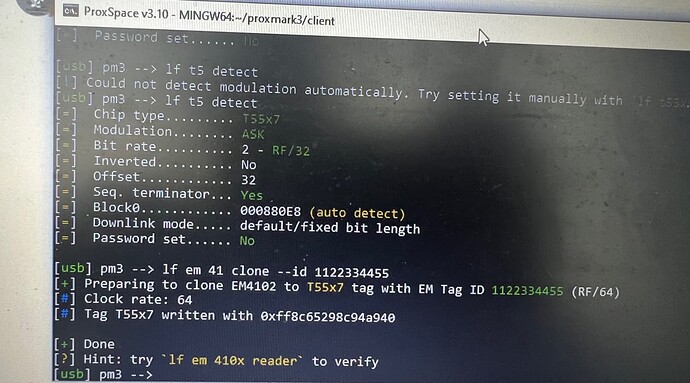
can you try a
lf em 41 clone --id 1122334455
then
lf search
what are the results?
not knowing the background to the fobs, they may have a password on them ![]()
It could be anything, but let’s cross that bridge if we need to
The black one is a HF, so you won’t be able to use that to clone your HID tag.
Can you do a HF search on the blue one as well? It looks like it might also be HF given he results when you did the LF t5 detect command.
lf hid clone -r 000000000000002007918ca7
then
lf hid reader or lf search
lf hid reader or lf search
![]()
This, on the blue tag. It may take a couple of goes to get it to work, so do a LF search after each write attempt. You are looking for the “raw” to be 000000000000002007918ca7. Once that happens, the cloning will have worked.
so u think its cloned after seeing the last photo from the original key?
That suggests it worked.