Hi,
I just got my Proxmark3 easy and trying to do some basic practice. I try to clone my room key:
[usb] pm3 → hf search
[!] No known/supported 13.56 MHz tags found
[usb] pm3 → hf search
[/] Searching for ISO14443-A tag…
[=] ---------- ISO14443-A Information ----------
[+] UID: 04 B9 18 B2 87 10 94 ( double )
[+] ATQA: 00 44
[+] SAK: 00 [2]
[+] Possible types:
[+] MANUFACTURER: NXP Semiconductors Germany
[+] MIFARE Ultralight EV1 ~32B
[=] proprietary non iso14443-4 card found, RATS not supported
[=]
[?] Hint: Try hf mfu info
[+] Valid ISO 14443-A tag found
[usb] pm3 → hf mfu info
[=] — Tag Information --------------------------
[+] TYPE: MIFARE Ultralight EV1 48bytes (MF0UL1101)
[+] UID: 04 B9 18 B2 87 10 94
[+] UID[0]: 04, NXP Semiconductors Germany
[+] BCC0: 2D ( ok )
[+] BCC1: B1 ( ok )
[+] Internal: 48 ( default )
[+] Lock: 08 00 - 0000100000000000
[+] OTP: 88 01 C9 18 - 10001000000000011100100100011000
[=] — Tag Counters
[=] [0]: 00 00 00
[+] - BD tearing ( ok )
[=] [1]: 00 00 00
[+] - BD tearing ( ok )
[=] [2]: 00 00 00
[+] - BD tearing ( ok )
[=] IC signature public key name: NXP Ultralight EV1
[=] IC signature public key value: 0490933BDCD6E99B4E255E3DA55389A8
[=] : 27564E11718E017292FAF23226A96614
[=] : B8
[=] Elliptic curve parameters: secp128r1
[=] TAG IC Signature: 6D7D5D6BEDAD8B09345B10F308AC1A48
[=] : 9F2797B124C0C74BED716AE5C3EC401F
[+] Signature verification: successful
[=] — Tag Silicon Information
[=] Wafer Counter: 19009782 ( 0x12210F6 )
[=] Wafer Coordinates: x 185, y 280 (0xB9, 0x118)
[=] Test Site: 2
[=] — Tag Version
[=] Raw bytes: 0004030101000B03
[=] Vendor ID: 04, NXP Semiconductors Germany
[=] Product type: Ultralight
[=] Product subtype: 01, 17 pF
[=] Major version: 01
[=] Minor version: 00
[=] Size: 0B, (64 ↔ 32 bytes)
[=] Protocol type: 03, ISO14443-3 Compliant
[=]
[=] — Fingerprint
[=] n/a
To this sticker which advertises that the UID can be changed: 13.56mhz UID changeable S50 1K NFC Sticker Wet Inlay NFC tag Sector Blank Car*k* | eBay UK
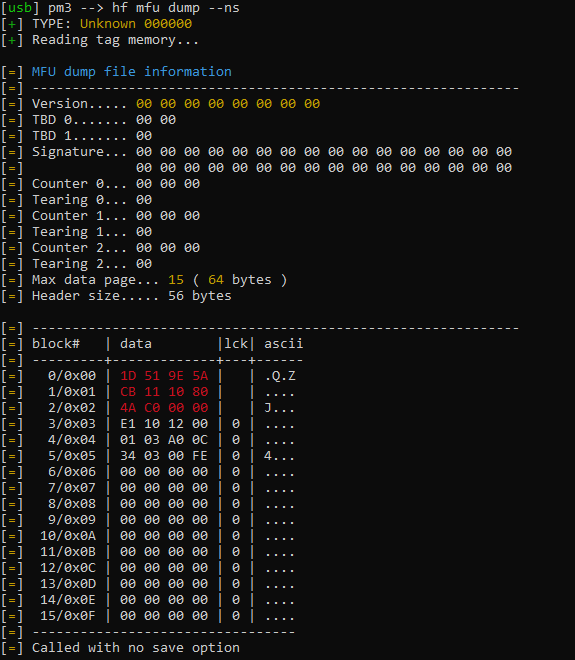
[usb] pm3 → hf search
[|] Searching for ISO14443-A tag…
[=] ---------- ISO14443-A Information ----------
[+] UID: 1D CE 9D CB 11 10 80 ( double )
[+] ATQA: 00 44
[+] SAK: 00 [2]
[+] Possible types:
[+] MANUFACTURER: Shanghai Fudan Microelectronics Co. Ltd. P.R. China
[+] TYPE: Unknown 000000
[+] MIFARE Ultralight/C/NTAG Compatible
[!] No known/supported 13.56 MHz tags found
[usb] pm3 → hf mfu info
[=] — Tag Information --------------------------
[+] TYPE: Unknown 000000
[+] UID: 1D CE 9D CB 11 10 80
[+] UID[0]: 1D, Shanghai Fudan Microelectronics Co. Ltd. P.R. China
[+] BCC0: C6 ( ok )
[+] BCC1: 4A ( ok )
[+] Internal: C0
[+] Lock: 08 00 - 0000100000000000
[+] OTP: E9 11 DB 18 - 11101001000100011101101100011000
[=]
[=] — Fingerprint
[=] n/a
Is it possible to do this, and how to do it step by step? Please let me know which document I need to study. Thank you very much!