I believe you should only need to use —ki 0
I’ve been working everyday here lately, but had a few min tonight to dedicate to this. I manually wrote blocks 6-9 to the iclass card from redteamtools. (or at least and semi confident that it worked) and now all of a sudden I can’t dump or rdbl from the card. I have full function on my original card. But, the “blank” responds to hf search and hf info, but doesn’t show any data block info. Did I smoke check the card unintentionally?
As I said, I’m not 100% sure 6-9 blocks were successfully written. The card did not work at the reader.
Also, I have an old work ID that I thought I had lost a while back that I had replaced. both Iclass legacy and em4305 chip types (same as the card I’m trying to clone to the flexclass, iclass only) and I was worried that the readers used both HF and LF chips for access control. I used the lf em 4x05 wipe and verified that the PM3 no longer read the em4305 tag and I still got in through the gate. So, am I doomed and the access control system is actually using the uid? If so, the flexclass implants come blank or can the uid be written?
A lot in one post, I know. I think I might order a couple more of the cards from redteam just to have anyways.
EDIT:
I manually read each block using the credit key and I had a digit off on block 8 and 9 (they were the same so I copy&pasted) will try again in the morning on the way out of work. Still unclear as to why the dump isn’t working…
As I understand it, UIDs can not be changed on the flexClass. Let me know how the new try works.
no dice on the try the other morning, but I did manage to grab my old card and it does still let me in. I’m starting to think that the security guards just grab a new card, have the image printed on it, and enroll it to the database. which concerns me because my old card has a diff uid and it still works
![]()
![]()
![]()
security through obscurity…gotta love it
I’ve been monitoring my email for a response to the thread, only to realize I never actually posted the last message on here ![]()
ANYWAYS
I ordered 2 more iclass cards from redteam and copied ONLY blocks 6-9 from my active credential to the iclass card. Still no dice.
One of my coworkers had to have his card replaced recently, and I asked to look at it. He’s intrigued by the whole thing and agreed. When I shined my flashlight against the back, all I can see is a single coil and chip.
This may sound silly, but…I know there are multi-class readers. Has anyone encountered a system that has adopted a new card/chip type and phase out the others over time?
I thought the point of dual frequency reader was a “smooth” transition from one technology to the next …
I’m sure there could be both in use at the same time.
Generally, multiclass can mean both LF/HF as well as meaning having access with non-secure readers and secure readers.
HID cards generally don’t use UID to authenticate, instead using blocks 6-9. It’s possible that your system is using SE readers that are checking for something else. Can you share a photo of the reader you are trying to use the card with?
LF HID cards do use UID to authenticate. I have an LF HID pad here and all it sends is the UID.
Sorry, I should have been more specific. All HID iClass cards AFAIK don’t use UID.
I can try to snap a picture wednesday on my way in the turnstile. If we have a slow night I might be able to try to get a number off the back without security seeing me. ![]() Someone knocked one of them off the mount bracket the other day and I tried to get a quick peak for a model number or something useful, but with everyone that was around…probably not the best idea.
Someone knocked one of them off the mount bracket the other day and I tried to get a quick peak for a model number or something useful, but with everyone that was around…probably not the best idea.
Trying to do this surreptitiously will look suspicious. Walk up to it and copy numbers whatever with confidence.
If anyone does ask just reply that you are looking for model numbers to determine compatibility. Most likely nobody will ask. If you try to be surreptitious you can guarantee that people will treat you with suspicion.
Noted. I had a brilliant idea and text a buddy on the other shift to snap a pic for me on his was out this evening. It’s not the best quality, but maybe it will shed some light on what I’m missing?
edit:
So after remembering a couple things and reading up again. SE readers use encrypted blocks after 6-9 correct?
would hf ic rdbl 10-25 (I stopped after 25) on my authorized work credential read anything other than all FF’s if there was anything at all written? I’d assume no?
Hmm. I’ve had success with a very similar looking device and a flexClass.
You would see data, but it would be encrypted in a way that would make it unusable.
Can you do hf ic dump and share the results?
I would suspect that blocks 10 to 31 do not contain data, but given the different values block 19 onwards are probably never used by that application.
so am i missing something other than writing blocks 6-9?
is there a config that i need to get right?
Looking at it again App Area 2 is blocks 19 to 31.
If you can copy the blocks 0 to 9 then you should be good. I think.
You’ll need to clone blocks 6-9, but it sounds like you’ve already done that. Can you share the dump from the cloned cards as well?
Unfortunately, 0-5 are unclonable AFAIK. No changing the UID on these things ![]()
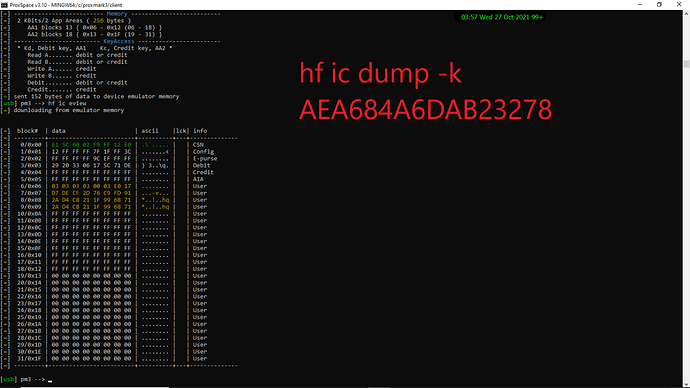
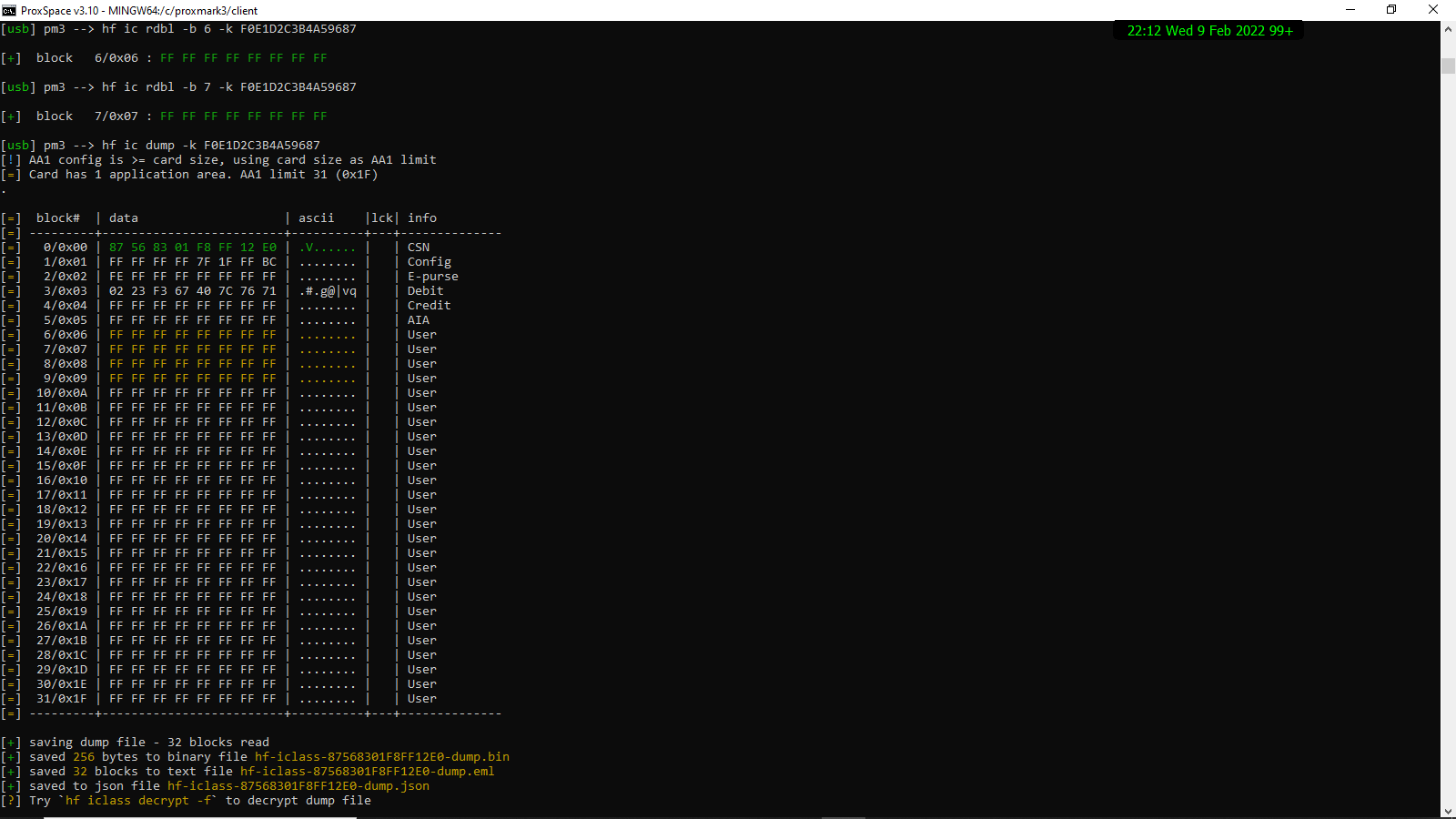
well that was weird? I pulled out my two original clock cards from work and dumped again ( to make sure I posted the correct screenshot)
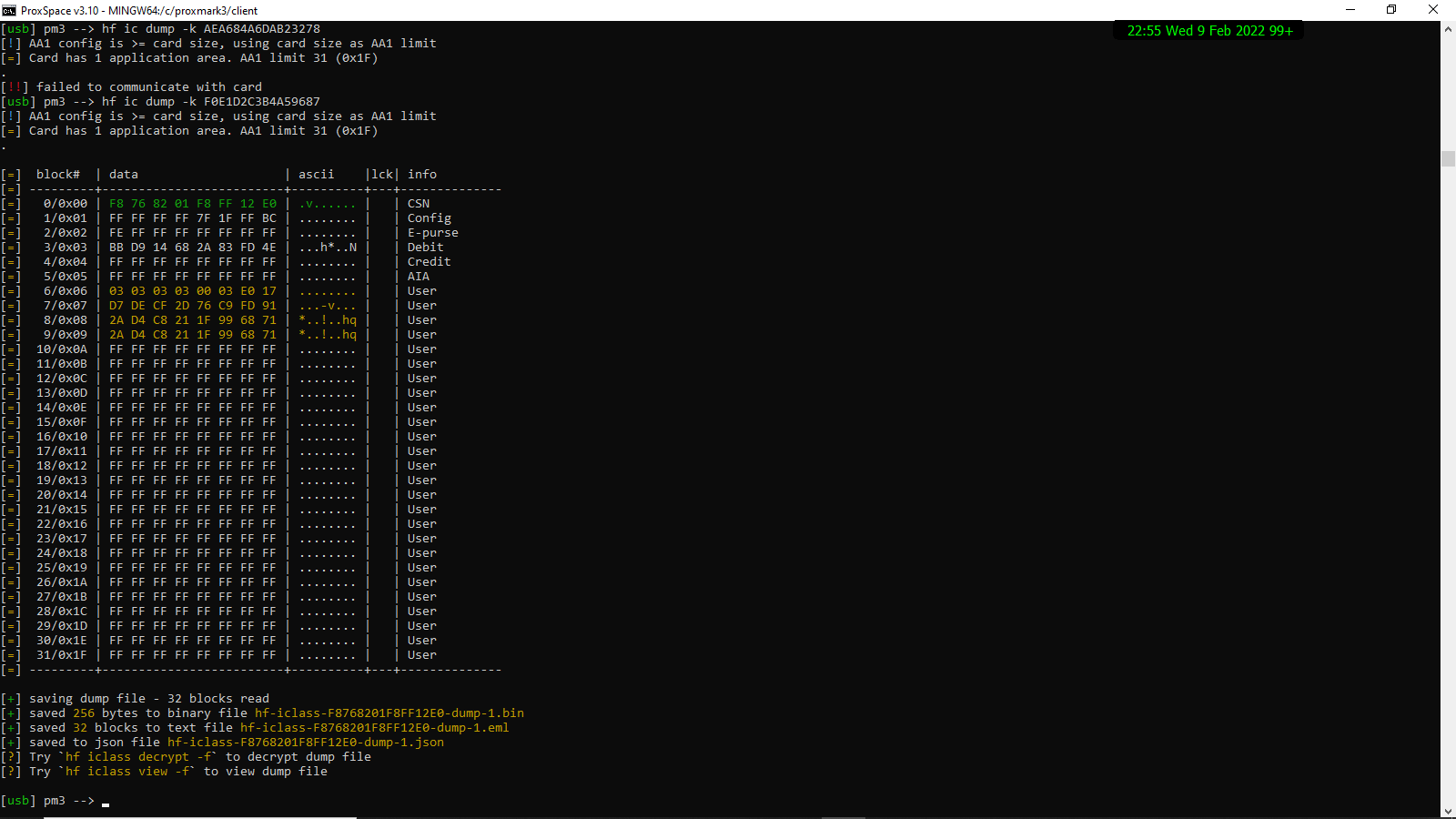
for whatever reason, the dump would not work for the “cloned cards” using the same key. However, when using the Kd from picopass F0E1D2C3B4A59687 key, I got a successful dump file. Have I somehow been writing to the cards using the wrong key and thinking that it was successful? It’s been a couple months but I’m certain that the wrbl commands worked after verifying with rdbl after each, using the AEA684A6DAB23278 key
and then after writing with the kd key F0E1D2C3B4A59687 this is the dump. It seems that the blocks have been written? Not getting a response from cmds using the AEA684A6DAB23278 key at all.
I tend not to use explicitly typed keys, as it leaves open the option for corrupted cards. Mess around with the pre-stored iClass keys. I think there are 3 or 4 of them. You can access them by changing -k {key} to --ki {int 0-3}.
Try that and report back ![]()