I’m back at it and still trying to authenticate.
I have a couple different EV1, EV2, and EV3 cards with different configurations. Key types, AIDs, files, etc.
My current test card is an EV3 with no AID. It has default settings.
Displaying the 8 byte DES key and auth via Proxmark:
[fpc] pm3 --> hf mfdes detect
[=] Found key num: 0 (0x00)
[=] channel ev1 key des [8]: 00 00 00 00 00 00 00 00
[fpc] pm3 --> hf mfdes auth -n 0 -t des -k 0000000000000000
[+] PICC selected and authenticated succesfully
[+] Context:
[=] Key num: 0 Key algo: des Key[8]: 00 00 00 00 00 00 00 00
[=] Secure channel: ev1 Command set: niso Communication mode: plain
[=] Session key [8]: 01 02 03 04 61 8C 65 4B
[=] IV [8]: 00 00 00 00 00 00 00 00
My first Python authentication script uses:
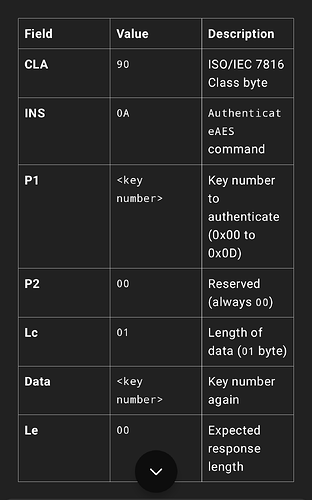
apdu = [0x90, 0x0A, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
Response: []
Status Words: 91 7E
Which means:
(0x91, 0x7E): “91 7E: Length of command string invalid”
The complete script is:
from smartcard.System import readers
# Get available smartcard readers
r = readers()
if not r:
print("No smartcard readers found!")
exit()
# Connect to the first available reader
connection = r[0].createConnection()
connection.connect()
# Manually send the APDU (e.g., for DES authentication)
apdu = [0x90, 0x0A, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
# Send the APDU command to the card
response, sw1, sw2 = connection.transmit(apdu)
# Print response
print("Response:", response)
print(f"Status Words: {sw1:02X} {sw2:02X}")
I’ve also tested the command_des_auth and command_legacy_auth functions at apdu_utils/security_commands.py at master · HotelSierraWhiskey/apdu_utils · GitHub
The output for this is the same:
Sending APDU for authentication: [144, 10, 0, 0, 8, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Response: []
Status Words: 91 7E
Here is the script I built around those functions:
from smartcard.System import readers
from security_commands import command_aes_auth, command_des_auth, command_legacy_auth
# Get available smartcard readers
r = readers()
if not r:
print("No smartcard readers found!")
exit()
# Connect to the first available reader
connection = r[0].createConnection()
connection.connect()
# Define the DES key (8 bytes of 0s for your key)
key_id = [0x00] * 8
# Choose the correct authentication function
# Use legacy DES authentication if you're using 3DES or legacy DES keys
apdu_auth = command_legacy_auth(key_id) # Change to command_aes_auth if you're using AES keys
print("Sending APDU for authentication:", apdu_auth)
# Send the APDU for authentication
response, sw1, sw2 = connection.transmit(apdu_auth)
# Print the response
print("Response:", response)
print(f"Status Words: {sw1:02X} {sw2:02X}")
I’ve had no luck on this.
I’m wondering about the LC field. (length of data). Why is it 0x01? Is it the length of the key? I tried changing it to 0x08.
Is there a way I can view the APDU that is sent when I authenticate via the Proxmark? I have 2 Proxmarks. I tried the sniff command, but couldn’t understand what I was looking at in the .pm3 file it generated.