I have saved a .bin file after i ran HF MF AUTO but I don’t know how to then go on and write that onto a new card - any advice appreciated. I tried to look into converting a .bin to a dump file to write with a different device i have but couldn’t
What kind of new card do you have?
Is it a magic card? If so, which gen?
If you don’t know, try running hf mf info on your blank card and post the output here
[=] No previous history could be loaded
[usb] pm3 → hf mf info
[=] — ISO14443-a Information ---------------------
[+] UID: BC 95 D4 03
[+] ATQA: 00 04
[+] SAK: 08 [1]
[=] — Keys Information
[+] loaded 2 user keys
[+] loaded 61 hardcoded keys
[+] Sector 0 key A… FFFFFFFFFFFF
[+] Sector 0 key B… FFFFFFFFFFFF
[+] Sector 1 key A… FFFFFFFFFFFF
[+] Block 0… BC95D403FE0804006263646566676869 | bcdefghi
[=] — Fingerprint
[+] Fudan based card
[=] — Magic Tag Information
[=] <n/a>
[=] — PRNG Information
[#] Static nonce… 009080a2
[+] Static nonce… yes
Since this doesn’t appear to be a magic card the command you’ll want to use is hf mf restore -f <dump file>
If the blank card doesn’t have all its keys set to FFFFFFFFFFFF you’ll need to find its keys with hf mf auto and append -k <blank's key file> --ka to the restore command
Additionally, you should know that since this isn’t a magic card not everything will be copied across, in particular the UID is not capable of being overwritten, this may cause the clone to not work correctly with whatever you might be using it for
If it doesn’t work, or you just want it to be a touch easier, you might look into picking up some Gen1A magic chips
thanks for all that, appreciated, i will work though that advice
Imagine a language you don’t speak or understand a word of - perhaps, Russian .
Thats me, with this . So- thanks again
ok - I just found a magic gen1a card in a lot i bought ages ago… is it a different command to the one you gave before to try and dump to this one? (by the way, that other card i was trying did not work )
[usb] pm3 → hf mf info
[=] — ISO14443-a Information ---------------------
[+] UID: 89 74 07 2F
[+] ATQA: 00 04
[+] SAK: 08 [1]
[=] — Keys Information
[+] loaded 2 user keys
[+] loaded 61 hardcoded keys
[+] Sector 0 key A… FFFFFFFFFFFF
[+] Sector 0 key B… FFFFFFFFFFFF
[+] Sector 1 key A… FFFFFFFFFFFF
[+] Block 0… 8974072FD50804006263646566676869 | bcdefghi
[=] — Fingerprint
[+] Fudan based card
[=] — Magic Tag Information
[+] Magic capabilities… Gen 1a
[+] Magic capabilities… Gen 4 GDM / USCUID ( ZUID Gen1 Magic Wakeup )
[=] — PRNG Information
[+] Prng… weak
I just found a magic gen1a card in a lot i bought ages ago…
Ah, brilliant, you should be able to just use hf mf cload -f <original card dumpfile> no fussin’ about with keys or anything
and this is the dump file created from doing hf mf auto? or something different?
Correct, that dumpfile should work
That’s from the card you wish to clone, not the blank you’re cloning to
hf-mf-831FE1BA-dump.bin
hf-mf-831FE1BA-dump.json
hf-mf-831FE1BA-key.bin
which of these am I loading?
hopefully this is end of questions !
Either of the ones that have dump in the name, the other one is the keyfile
hmm that gave a different set of failure beeps when loaded and tested.
Is the following info any use? The plot thickens
pm3 → hf mf auto
[#] Auth error
[!] no known key was supplied, key recovery might fail
[+] loaded 5 user keys
[+] loaded 61 hardcoded keys
[=] Running strategy 1
[=] Running strategy 2
[=] …
[=] Expected execution time is about 25 seconds on average
[=] Press pm3 button to abort
[=] Running darkside …
[-] Card is not vulnerable to Darkside attack (its random number generator seems to be based on the wellknown
[-] generating polynomial with 16 effective bits only, but shows unexpected behaviour.
[-] No usable key was found!
[?] Hint: Try hf mf autopwn -f mfc_default_keys i.e. the Randy special
[usb] pm3 →
hmm that gave a different set of failure beeps when loaded and tested.
It is possible that the system you’re using is capable of detecting magic cards, but that’s pretty rare
This is an autopwn of the cloned card?
Try hf mf cview and see if it matches the dump of the original
this is the copied card - it only is showing 15 sectors -
all the same . I’ll post the original after this
sec | blk | data | ascii
[=] -----±----±------------------------------------------------±----------------
[=] 0 | 0 | FF FF FF FF FF 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 1 | 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 2 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 3 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 1 | 4 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 5 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 6 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 7 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 2 | 8 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 9 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 10 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 11 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 3 | 12 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 13 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 14 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 15 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 4 | 16 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 17 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 18 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 19 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 5 | 20 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 21 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 22 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 23 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 6 | 24 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 25 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 26 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 27 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 7 | 28 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 29 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 30 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 31 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 8 | 32 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 33 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 34 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 35 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 9 | 36 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 37 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 38 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 39 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 10 | 40 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 41 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 42 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 43 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 11 | 44 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 45 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 46 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 47 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 12 | 48 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 49 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 50 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 51 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 13 | 52 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 53 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 54 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 55 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 14 | 56 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 57 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 58 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 59 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 15 | 60 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 61 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 62 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 63 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] -----±----±------------------------------------------------±----------------
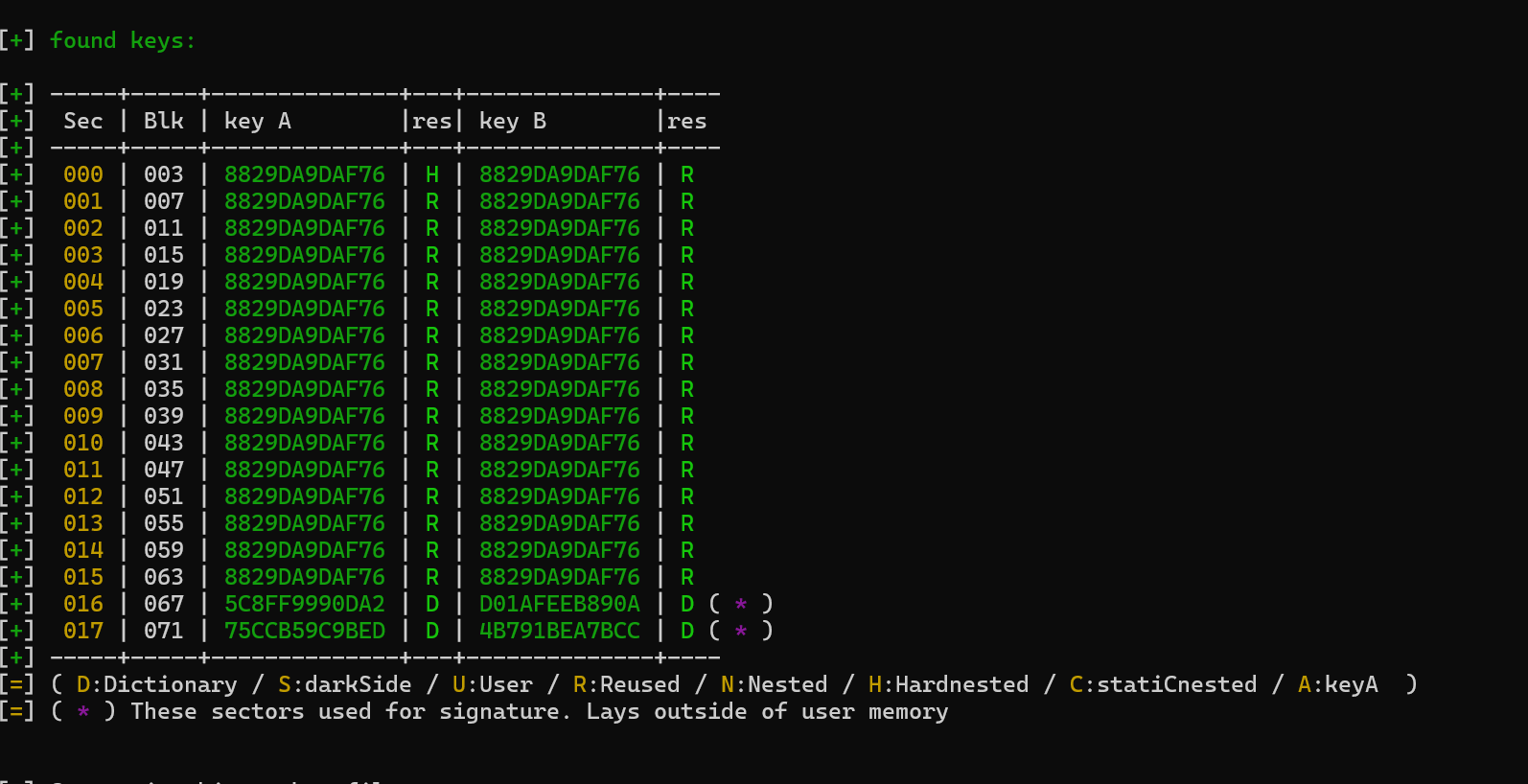
orig –
Sec | Blk | key A |res| key B |res
[+] -----±----±-------------±–±-------------±—
[+] 000 | 003 | 8829DA9DAF76 | H | 8829DA9DAF76 | R
[+] 001 | 007 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 002 | 011 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 003 | 015 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 004 | 019 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 005 | 023 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 006 | 027 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 007 | 031 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 008 | 035 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 009 | 039 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 010 | 043 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 011 | 047 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 012 | 051 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 013 | 055 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 014 | 059 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 015 | 063 | 8829DA9DAF76 | R | 8829DA9DAF76 | R
[+] 016 | 067 | 5C8FF9990DA2 | D | D01AFEEB890A | D ( * )
[+] 017 | 071 | 75CCB59C9BED | D | 4B791BEA7BCC | D ( * )
[+] -----±----±-------------±–±-------------±—
That dump looks weird to me, I would probably try the cload command again, and possibly an hf mf cwipe first
The copied card appears to only have 15 sectors, whereas the original has 17.
I tried wiping and loading again, same result.
I tried to read sector 16 on new card - got this -
pm3 → hf mf cgetsc -s 16
[=] # | sector 16 / 0x10 | ascii
[=] ----±------------------------------------------------±----------------
[#] read block send command error
[!!] Can’t read block. 64 error=-1
Also tried this -
pm3 → hf mf csetblk --blk 67 -d 5C8FF9990DA2D01AFEEB890A
[-] target block number out-of-range, got 67
and this -
pm3 → hf mf cgetblk --blk 16 -v
[=] # | sector 04 / 0x04 | ascii
[=] ----±------------------------------------------------±----------------
[=] 16 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[usb] pm3 →
ok heres a screenshot of original card, showing the sectors 16 and 17, that don’t appear on the new card. The dump files I’ve been using don’t seem to carry the signature sectors… how do I include these to the new card ?
I have sifted for hours now looking through videos and tutorials and cannot find any information at all on these signature sectors… hopefully someone here can help. Let me know if this is something unknown too, so I know that you guys don’t know and I’ll stop asking ! haha
You can pretty safely ignore those extra blocks, their only purpose is holding the tag signature, and while I’m sure they exist, I don’t recall ever hearing of a system which actually uses the signature…
If that does end up being the case, then I think a Gen4 can do signature spoofing?
The two big issues I’m seeing with that dump are:
Block 0 is malformed: FF FF FF FF FF 00 00 00 00 00 00 00 00 00 00 00, which is pretty much definitely an issue; and the rest of the sectors being blank, which isn’t necessarily an issue, but it is kind of odd and might also point to a failed write
heres a screenshot of original card,
These are just the keys, can you post the full dump? It’s the rest of the data we’re interested in at the moment
You can use the hf mf view command to load and view a dumpfile
[usb] pm3 → hf mf view -f C:\ProxSpace\pm3/hf-mf-831FE1BA-dump-003.bin
[+] Loaded 1152 bytes from binary file C:\ProxSpace\pm3/hf-mf-831FE1BA-dump-003.bin
[=] -----±----±------------------------------------------------±----------------
[=] sec | blk | data | ascii
[=] -----±----±------------------------------------------------±----------------
[=] 0 | 0 | 83 1F E1 BA C7 88 04 00 C8 06 00 20 00 00 00 16 | … …
[=] | 1 | 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 2 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 3 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 1 | 4 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 5 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 6 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 7 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 2 | 8 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 9 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 10 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 11 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 3 | 12 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 13 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 14 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 15 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 4 | 16 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 17 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 18 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 19 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 5 | 20 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 21 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 22 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 23 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 6 | 24 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 25 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 26 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 27 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 7 | 28 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 29 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 30 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 31 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 8 | 32 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 33 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 34 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 35 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 9 | 36 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 37 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 38 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 39 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 10 | 40 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 41 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 42 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 43 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 11 | 44 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 45 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 46 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 47 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 12 | 48 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 49 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 50 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 51 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 13 | 52 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 53 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 54 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 55 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 14 | 56 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 57 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 58 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 59 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 15 | 60 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 61 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 62 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 63 | 88 29 DA 9D AF 76 7F 07 88 00 88 29 DA 9D AF 76 | .)…v…)…v
[=] 16 | 64 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 65 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 66 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | …
[=] | 67 | 5C 8F F9 99 0D A2 70 F0 F8 69 D0 1A FE EB 89 0A | .…p…i…
[=] 17 | 68 | 48 4B 54 31 30 35 0B 06 16 7F 70 00 00 00 00 00 | HKT105…p…
[=] | 69 | F2 45 9D 33 3C 41 09 F2 09 4B 2D A9 FC CF 3A CE | .E.3<A…K-…:.
[=] | 70 | 54 08 58 A2 7C E5 42 9D C9 E9 93 76 94 CA CD FC | T.X.|.B…v…
[=] | 71 | 75 CC B5 9C 9B ED 70 F0 F8 69 4B 79 1B EA 7B CC | u…p…iKy…{.
[=] -----±----±------------------------------------------------±----------------
[usb] pm3 →