I have seen several people in the forums with the same issue I have. An iClass DY badge for work or school that doesn’t seem to read as any card type. I was finally able to clone mine to the xEM in my NeXT implant today and wanted to share my steps for others to recreate.
For starters I’ve seen some confusion over whether iClass DY is low or high frequency since it doesn’t read with Taginfo on android. I can confirm it is high frequency but is only able to be read with HID iClass or Multiclass readers (plus the proxmark 3 RDV4).
The method I used only works if the access control system in question uses multi class readers and standard Wiegand card format (My university uses HID corporate 1000 35 bit)
I used an ESP-KEY and an RP40 multiclass reader to extract the raw Wiegand data from my badge
I took the raw hex data from it and used
lf hid clone -r
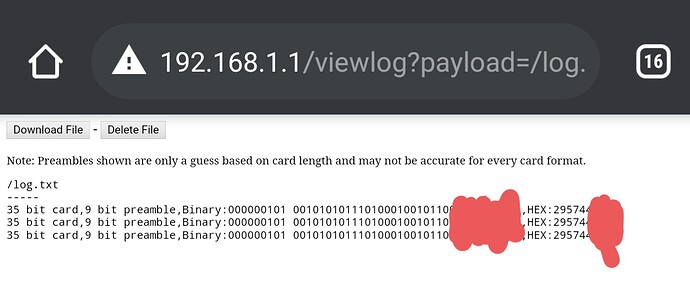
on my proxmark to clone to a blank t55x7 fob I had handy. Once I confirmed its raw data was the same as my badge I repeated the command on my implant. In this picture you can see my official badge, test fob, and implant all showing the exact same raw data.
Long story short it is possible to clone a high frequency iClass DY credential to a low frequency t55xx chip but in my case the card data is so much longer now it is almost impossible to line up on a reader to get a solid read. I have already ordered a flexEM to use instead and will update if it works better.