I guess I was underestimating storage requirements
I was thinking 50 or so… website user password
I guess I’ll have to consider cloud stuff
But doesn’t that add a point of vulnerability? Like didn’t keepass or someone get hacked recently?
I guess I was underestimating storage requirements
I was thinking 50 or so… website user password
I guess I’ll have to consider cloud stuff
But doesn’t that add a point of vulnerability? Like didn’t keepass or someone get hacked recently?
if implemented correctly and used with a strong master key, the vault file itself can be public.
The Apex can provide strong keys in a secure way.
But you’d still need an app on your phone to interact with the apex to log into the cloud manager?
I liked the idea of not needed anything on the phone, being able to just use a random phone if needed
Not a deal breaker, just need to reevaluate… I was hoping for something lower friction for my non programmer brain
kinda? but also not really… so AES is typically what’s used to secure large amounts of data because public key crypto is notoriously slow. sometimes PKI can be used to encrypt an AES key and then that key is used to decrypt the larger data volume… but anyway, if you have an encrypted database of passwords you can, in theory, make it public… put it on 20 websites… sync it across dropbox, google drive, and several computers… and as long as the encryption algo isn’t compromised, it’s fine…
so often “hacked” means some other aspect of implementation has been compromised, not the actual encryption… so like, someone gets remote access to your computer, then you decrypt your password database to use it, and they take a copy of the decrypted database… that’s a possibility… but if your computer is already compromised you’re already in a bad spot because even if your passwords were on your apex, they could just collect them as you used them.
this would not be really possible unless you wanted to just read raw text data from an NDEF record and then pick through it to find your passwords… if it’s even possible… i mean if you want to require no apps at all on the phone then the phone OS is left to do whatever it feels appropriate to display the text record on screen… and it might not even display the entire text record… or it might not allow text selection and copying to clipboard… and the whole password database would be clear text on your implant for anyone to read and make a copy of.
it’s just not pragmatic… it’s kind of like people who demand their password database must be usable offline… when 99.9999% of the passwords stored in the database are all for online cloud services… the requirement of needing to access it with a phone that has no apps on it seems kind of obtuse… know what i mean?
Keepass is offline though, and you can use a key file + your implant for extra extra security if you wanted.
I think keepassXC even supports syncing offline over USB so you could sync your db between phone and pc, without it going online
You wouldn’t be able to do anything more than plaintext NDEF on a phone without app.
In theory, there is Web-NFC, but that’s only supported on some browsers on some android phones. And Limited to NDEF. So for something that deserves the name “password manager”, you need a native app if you want to do it correctly
To be clear, none of this was a criticism or me being obtuse… I’m just trying to make heads or tails of it
A solid point, I just like local storage when possible, prevents weirdness like not being able to access something due to a ddos, or a server is down… also harder to steal something if it’s not on the net in general
Not a deal breaker, I just misunderstood some stuff… and am still trying to learn
The required app thing was just me thinking, if I lost or forgot my phone… I could use a friends to retrieve a password if I needed… , but I don’t think I’m willing to go plain text to achieve that lol
no problem… happy to hash it out with you ![]()
yeah… my thought here is that if you have a solution that relies on an app and that app is made available via the normal published app stores, and maybe as a apk sideload via any of the alternative app stores out there… then it’s not too big a hurdle to borrow a phone and ask to install the app there so you can access your stuff… but honestly in today’s world, old phones are a common junk drawer denizen… I have two old phones on my desk right now… each of them has the fidesmo app on it… for example. Access to a phone so you can use your implant and log into online services isn’t all that difficult to come by for most people… but not all people.
I use a self hosted bitwarden install that uses my vivokey key U2F for 2 factor validation. It works well. And feels less cloud when it’s self hosted.
Is this vaultwarden?
It is! And works great. I have my whole family on my install.
Will have to do some testing and compare to 1Password. Thanks for the recc.
Is KeePassXC available on Google play for Android devices? I see a couple apps related to keepass but with different names by different developers. Wasn’t sure if this was a side loaded app or was available somewhere else.
I’m just trying to figure out the best password manager to use with Apex.
Great thank you for the response! So will this app work with the HMAC-SHA1 Apex app out of the box? Or is there something else I need to do to get them working together?
You’ll have to manually push a secret to your hmac-sha1 applet through CLI or wait until the vivokey companion app is released. Thankfully @StarGate01 documented how to do this here!
The jist of it is, you’ll need to get yktool.jar from here
Then, with your hmac sha1 applet installed and your implant on your reader, you can run the command “java -jar yktool.jar list” and it should show your implant listed as shown here:
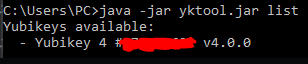
then, to program a secret to it you run the command:
and replace the word secret with a 40 character hex string (make sure to back this up somewhere safe)
If successful you should receive this ![]()
![]()
Fantastic thank you for reiterating these detailed instructions!
Has anyone successfully gotten the Apex to work with Lastpass? or is it possible?