Well okay, I may have overstated it a bit  But let me explain:
But let me explain:
Firstly, re your question: indeed the credentials are on the PC. If you compromise the PC, it doesn’t matter what scheme you use: it’s defeated by definition. This holds true of any symmetric cryptography system (which is what OTPs are) since both the authenticator and the authenticated device must hold the same key.
But here I was talking about something else:
With TOTP authentication, the challenge (that is, the big-ass number you present to the hash algorithm to calculate a hash from using the shared secret) is the current time in chunks of 30 seconds. Meaning, for 30 seconds, the challenge remains unchanged. Guess the right code within 30 seconds and you’re in. And since TOTP codes are between 6 and 10 digits, there are “only” 1 million to 10 billion choices of code to choose from
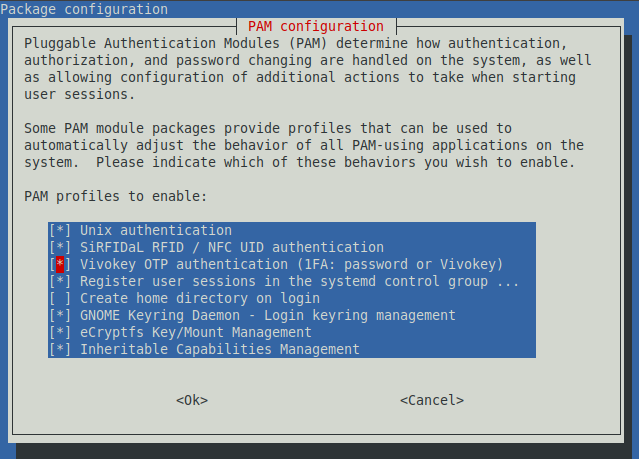
What the new Vivokey PAM does now is, instead of using the time divided by 30 seconds as a challenge, it uses a completely random number each time it runs. So the resulting hash is only valid once. And instead of using a very small subset of the hash (the 6- to 10- decimal digit number) as a code, it uses the entire hash, which would have you guess 1 code out of an unfathomably large number of possible codes.
The size of the keyspace makes it slightly safer - only slightly because, practically speaking, even with 6-digit codes, it’s almost impossible to guess one code out of one million within 30 seconds - particularly since PAM throttles the number of tries per minute quite dramatically.
What truly makes it safer is that, if a bad guy was to sniff the traffic between your implant and the reader (with a Proxmark3 for instance, but also possibly with a compromised USB hub) and get the code, they can’t use it in a replay attack anymore.
The reason I overstated it is because the aforementioned hypothetical replay attack would have to happen within 30 seconds, and more importantly, some shady dude would probably be crowding your space with suspicious NFC or USB hardware, and you’d have to be blind drunk not to notice.
But hey, in theory, no more replay attack and a huge keyspace is much more secure