Ah, in that case you’re also going about pulling keys from a sniff wrong. Can you list all the commands you’re running in order?
execute the following:
hf 14a sniff -r -c,
then use the mifare classic tool application and use the default keys and have it read all the sectors. Then press the pm3 button.
then trace list -t 14a
and lastly hf mf decrypt
I have seen that the answer [+] decrypted data… 61 08 65 EE
is a few lines higher on my sniff
Ah, okay. Few issues. MCT doesn’t know any keys other than default ones. Sniffing relies on the reader interacting with the card knowing the keys you want. hf 14a sniff -r -c is right. Instead of trace list -t 14a you want trace list -t mf since that is what handles the crypto1 stream. Decrypt is not needed here.
I mean, what I have is worthless? The original card has the keys, but I don’t have the original reader and it is on the street. I ordered a 4th generation supercard, so that I could sneak in the card into the reader and see if I could copy anything. When I get it I will try it, well first I will have to see how it works.
If the pm3 dictionary couldn’t pull all the keys, the reader is the only thing that holds what you seek. I don’t think that normal gen4 cards can do that, but there are special sniffer cards out there.
the one I ordered is a super sniffer m1-4b.
Ah good. That may do the trick.
I hope it works.
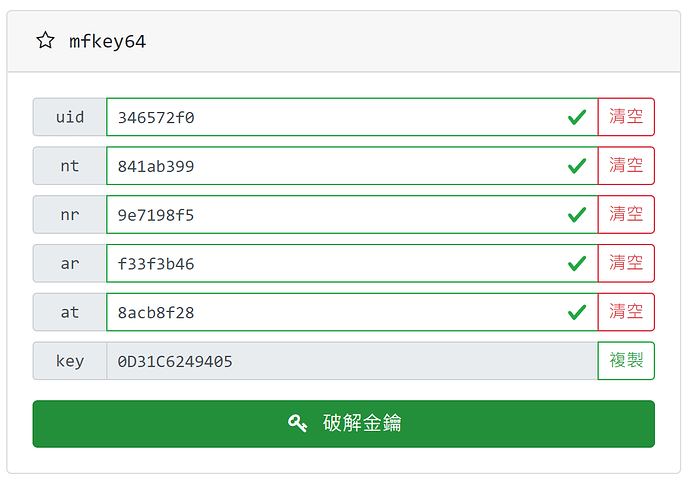
someone answered me by email, the thing is I don’t know who he is and he tells me the key (A) to 0D31C6249405. Fuck it works, how the fuck does that guy know that?
I’m freaking out…
Anyway, thank you whoever you are.
and thanks also to scorpion for helping me to solve my problems.
I was very upset about yesterday, I tried to look at the email of the person who sent it but it’s as if it didn’t exist, I don’t know. ![]() Because according to iceman and you at the moment there is no solution for a static encrypted nonce card. Reviewing all the information that I was discovering what was clear to me is that the only solution is to sniff the interaction of the card with the original reader of the machine and to be able to record that conversation so to speak (that will be the hard part for me). Or create a dictionary and get lucky with the keys after several days, this if I can say that it works half way, I got it because I intuited from other cards that usually start with a number and that’s what I did. If I had started with a letter, what I did would not work. Well I will wait for the super sniffer m1-4b to arrive and see how I do it in a little suspicious way.
Because according to iceman and you at the moment there is no solution for a static encrypted nonce card. Reviewing all the information that I was discovering what was clear to me is that the only solution is to sniff the interaction of the card with the original reader of the machine and to be able to record that conversation so to speak (that will be the hard part for me). Or create a dictionary and get lucky with the keys after several days, this if I can say that it works half way, I got it because I intuited from other cards that usually start with a number and that’s what I did. If I had started with a letter, what I did would not work. Well I will wait for the super sniffer m1-4b to arrive and see how I do it in a little suspicious way. ![]()
I spent a hell of a long time looking at a lot of web pages and when I was almost given up I found this and it does work.
website: mfkey
Mfkey is what the pm3 does automatically with trace list -t mf (as far as I know)
this ^ (but easier)
you could have done hf sim --1k --uid 346572f0
(or eload ur current file)
tap against the door, wait for visual response, withdraw pm3 and press the button then do hf mf list
thanks for the information, I did not know it, I will put it into practice.
I didn’t know that, but now I do. Thank you.
thanks for the information, I did not know it, I will put it into practice.