First of all, I apologize because I myself have made a mess with the cards I have. What happened is that I started to sniff an old card I had, thinking it was one of the new ones. (The old one decrypts with autopwn without problems, while the new one has an static encrypted nonce. The thing is that I started to sniff the old one, looking on the internet I found out that I had to look in the sections, but I didn’t know what to do with them, because I am an apprentice at the moment with the proxmark. But thanks to you I’m improving faster. And until scorpion didn’t tell me about list -t mf, I didn’t know it, now I was looking for information on the internet about how to interpret the results and get the key. Anyway the important thing is that thanks to you I learned the beginnings of sniffing with the proxmark.
I have already received the super sniffer m1-4b, from what I have been able to decipher, you have to put the same uid in the supercard so that it performs well the sniffing.
the original card has a static encrypted nonce.
[usb] pm3 → hf search
[|] Searching for ISO14443-A tag…
[+] UID: A7 15 AC 40
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] proprietary non iso14443-4 card found, RATS not supported
[+] Prng detection: weak
[#] Auth error
[?] Hint: try hf mf commands
[+] Valid ISO 14443-A tag found
I have already received the super sniffer m1-4b, from what I have been able to decipher, you have to put the same uid in the supercard so that it performs well the sniffing.
the original card has a static encrypted nonce.
the chinese card:
[usb] pm3 → hf search
[-] Searching for ISO14443-A tag…
[+] UID: 11 22 33 44
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] -------------------------- ATS --------------------------
[+] ATS: 09 78 00 91 02 DA BC 19 10 [ 05 00 ]
[=] 09… TL length is 9 bytes
[=] 78… T0 TA1 is present, TB1 is present, TC1 is present, FSCI is 8 (FSC = 256)
[=] 00… TA1 different divisors are supported, DR: , DS:
[=] 91… TB1 SFGI = 1 (SFGT = 8192/fc), FWI = 9 (FWT = 2097152/fc)
[=] 02… TC1 NAD is NOT supported, CID is supported
[=] -------------------- Historical bytes --------------------
[+] DABC1910
[+] Magic capabilities : super card
[+] Prng detection: weak
[#] Auth error
[?] Hint: try hf mf commands
[+] Valid ISO 14443-A tag foundhf
now i modified the uid according to the instructions on the card.
[usb] pm3 → hf 14a raw -sc -t 1000 cf00000000cd00A715AC40
[+] 90 00 [ FD 07 ]
[usb] pm3 → hf search
[/] Searching for ISO14443-A tag…
[+] UID: A7 15 AC 40
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] -------------------------- ATS --------------------------
[+] ATS: 09 78 00 91 02 DA BC 19 10 [ 05 00 ]
[=] 09… TL length is 9 bytes
[=] 78… T0 TA1 is present, TB1 is present, TC1 is present, FSCI is 8 (FSC = 256)
[=] 00… TA1 different divisors are supported, DR: , DS:
[=] 91… TB1 SFGI = 1 (SFGT = 8192/fc), FWI = 9 (FWT = 2097152/fc)
[=] 02… TC1 NAD is NOT supported, CID is supported
[=] -------------------- Historical bytes --------------------
[+] DABC1910
[+] Magic capabilities : super card
[+] Prng detection: weak
[#] Auth error
[?] Hint: try hf mf commands
[+] Valid ISO 14443-A tag found
Well it seems that it went well, as I understand from what I searched the internet, what I have to do is to join the original card with the original reader, and make the supercard, this in turn will pick up the keys that have been said reader and original card. Reading it this way it seems easy, right. Well, let’s see what comes out of this, I’ll let you know.
You can’t imagine what it took me to connect the proxmark3 to an android phone. But finally I can say that I have achieved it, not without suffering, but when you get it you do not see how good it feels.
For those who may be interested I leave the steps I have done, in order to use the proxmark3 with a mobile phone and thus be able to sniff the mifare classic 1k I have with its original reader, as it has a static encrypted nonce.
For those who may be interested I leave the steps I have done, in order to use the proxmark3 with a mobile phone and thus be able to sniff the mifare classic 1k I have with its original reader, as it has a static encrypted nonce.
first: install TCP-UART
second: install termux, not the play store version.
Next: pkg install root-repo
pkg install x11-repo
apt upgrade
pkg install git
pkg install python
pkg install proxmark3-git
Once you have done all this, you have to connect your proxmark3 using a usb otg cable and you have to hit the TCP-UART application in connect, check server and put 4321 and hit start. Then open the termux application and type the following command: proxmark3 tcp:localhost:4321 and you are done.
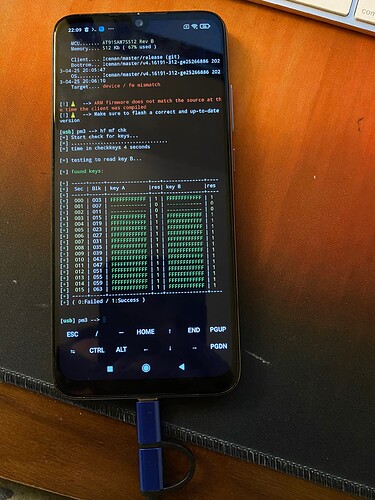
One question guys? Yes I have this data, nt, nr, ar, but I don’t know at. Is there any way to know it manually or something? The data would be from block 8.
The data are from a sniff, sectors 1 and 2 are the ones that have the information, the remaining keys by default are fffffffff…
178505916 | 178516380 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
178517632 | 178521152 | Tag |08 b6 dd | |
178586556 | 178591324 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
178592896 | 178597568 | Tag |49 e9 78 09 | | AUTH: nt
178604332 | 178613708 | Rdr |19 6a! da 7a 37 7a! 54! 40 | | AUTH: nr ar (enc)
178671452 | 178676220 | Rdr |50 00 57 cd | | HALT
178748796 | 178749788 | Rdr |52(7) | | WUPA
178751040 | 178753408 | Tag |04 00 | |
178760428 | 178770892 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
178772144 | 178775664 | Tag |08 b6 dd | |
178840364 | 178845068 | Rdr |61 08 65 ee | ok | AUTH-B(8)
178846704 | 178851376 | Tag |bf f7 1a c3 | | AUTH: nt
178858140 | 178867452 | Rdr |89 a0 78 a4 42! 52! cd! 07! | | AUTH: nr ar (enc)
178925244 | 178930012 | Rdr |50 00 57 cd | | HALT
179002540 | 179003532 | Rdr |52(7) | | WUPA
179004784 | 179007152 | Tag |04 00 | |
179014172 | 179024636 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
179025888 | 179029408 | Tag |08 b6 dd | |
179095292 | 179100060 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
179101632 | 179106368 | Tag |88 ae 8f cd | | AUTH: nt
179113084 | 179122460 | Rdr |08 c2! f4 9f 4c! 78! 1f 63! | | AUTH: nr ar (enc)
179180988 | 179185756 | Rdr |50 00 57 cd | | HALT
179261804 | 179262796 | Rdr |52(7) | | WUPA
179264048 | 179266416 | Tag |04 00 | |
179273436 | 179283900 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
179285152 | 179288672 | Tag |08 b6 dd | |
179356588 | 179361292 | Rdr |61 08 65 ee | ok | AUTH-B(8)
179362928 | 179367600 | Tag |86 0b 4b f0 | | AUTH: nt
179374364 | 179383740 | Rdr |5d aa! 20! 8a 59! 5c 0a c7 | | AUTH: nr ar (enc)
179444876 | 179449644 | Rdr |50 00 57 cd | | HALT
179521164 | 179522156 | Rdr |52(7) | | WUPA
179523408 | 179525776 | Tag |04 00 | |
179532796 | 179543260 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
179544496 | 179548016 | Tag |08 b6 dd | |
179616716 | 179621484 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
179623040 | 179627712 | Tag |ea c1 a2 3f | | AUTH: nt
179634492 | 179643868 | Rdr |82! be! 46! 12 ed! cc! 25! 33! | | AUTH: nr ar (enc)
179699948 | 179704716 | Rdr |50 00 57 cd | | HALT
179780300 | 179781292 | Rdr |52(7) | | WUPA
179782528 | 179784896 | Tag |04 00 | |
179791932 | 179802396 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
179803648 | 179807168 | Tag |08 b6 dd | |
179874764 | 179879468 | Rdr |61 08 65 ee | ok | AUTH-B(8)
179881088 | 179885760 | Tag |15 99 ba b8 | | AUTH: nt
179892540 | 179901852 | Rdr |59! 87! 54 11! 4b! 73 f4! a9 | | AUTH: nr ar (enc)
179956428 | 179961196 | Rdr |50 00 57 cd | | HALT
180035740 | 180036732 | Rdr |52(7) | | WUPA
180037968 | 180040336 | Tag |04 00 | |
180047372 | 180057836 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
180059072 | 180062592 | Tag |08 b6 dd | |
180137436 | 180142204 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
180143760 | 180148496 | Tag |a0 c3 21 85 | | AUTH: nt
180155212 | 180164524 | Rdr |e2 b2! f2 72 de 7e! ec 0b! | | AUTH: nr ar (enc)
180221964 | 180226732 | Rdr |50 00 57 cd | | HALT
180300188 | 180301180 | Rdr |52(7) | | WUPA
180302432 | 180304800 | Tag |04 00 | |
180311820 | 180322284 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
180323536 | 180327056 | Tag |08 b6 dd | |
180392156 | 180396860 | Rdr |61 08 65 ee | ok | AUTH-B(8)
180398496 | 180403232 | Tag |74 30 e4 9b | | AUTH: nt
180409948 | 180419260 | Rdr |e9! 2c 71 32! 7a! 72 48! f5 | | AUTH: nr ar (enc)
180475612 | 180480380 | Rdr |50 00 57 cd | | HALT
180555756 | 180556748 | Rdr |52(7) | | WUPA
180557984 | 180560352 | Tag |04 00 | |
180567388 | 180577852 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
180579088 | 180582608 | Tag |08 b6 dd | |
180652892 | 180657660 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
180659216 | 180663888 | Tag |a2 1c fb 60 | | AUTH: nt
180670668 | 180679980 | Rdr |ad 50! 71! 0e b4 da! c9! 99 | | AUTH: nr ar (enc)
180736508 | 180741276 | Rdr |50 00 57 cd | | HALT
180814236 | 180815228 | Rdr |52(7) | | WUPA
180816480 | 180818848 | Tag |04 00 | |
180825868 | 180836332 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
180837584 | 180841104 | Tag |08 b6 dd | |
180908620 | 180913324 | Rdr |61 08 65 ee | ok | AUTH-B(8)
180914960 | 180919632 | Tag |d2 4b 02 82 | | AUTH: nt
180926380 | 180935756 | Rdr |cd 81 6c! fc 31 7d! 2c! 77! | | AUTH: nr ar (enc)
180995772 | 181000540 | Rdr |50 00 57 cd | | HALT
181070812 | 181071804 | Rdr |52(7) | | WUPA
181073056 | 181075424 | Tag |04 00 | |
181082444 | 181092908 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
181094144 | 181097664 | Tag |08 b6 dd | |
181164924 | 181169692 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
181171264 | 181175936 | Tag |d6 a0 ff 41 | | AUTH: nt
181182700 | 181192076 | Rdr |d0 d8! 33 09 1e! db d1 be! | | AUTH: nr ar (enc)
181254812 | 181259580 | Rdr |50 00 57 cd | | HALT
181334332 | 181335324 | Rdr |52(7) | | WUPA
181336576 | 181338944 | Tag |04 00 | |
181345964 | 181356428 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
181357664 | 181361184 | Tag |08 b6 dd | |
181431068 | 181435772 | Rdr |61 08 65 ee | ok | AUTH-B(8)
181437408 | 181442080 | Tag |fc c5 13 d2 | | AUTH: nt
181448844 | 181458220 | Rdr |70 59! 55 62! c3! f9 52! 42! | | AUTH: nr ar (enc)
181514188 | 181518956 | Rdr |50 00 57 cd | | HALT
181593212 | 181594204 | Rdr |52(7) | | WUPA
181595456 | 181597824 | Tag |04 00 | |
181604844 | 181615308 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
181616560 | 181620080 | Tag |08 b6 dd | |
181687676 | 181692444 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
181694016 | 181698688 | Tag |0d 32 5f e1 | | AUTH: nt
181705452 | 181714764 | Rdr |79 96! 02! 64! 22 49 be! ff | | AUTH: nr ar (enc)
181770428 | 181775196 | Rdr |50 00 57 cd | | HALT
181850588 | 181851580 | Rdr |52(7) | | WUPA
181852816 | 181855184 | Tag |04 00 | |
181862220 | 181872684 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
181873936 | 181877456 | Tag |08 b6 dd | |
181948572 | 181953276 | Rdr |61 08 65 ee | ok | AUTH-B(8)
181954912 | 181959648 | Tag |67 d1 99 51 | | AUTH: nt
181966364 | 181975676 | Rdr |5a! 2e eb! 5e! a5 07 b7 68! | | AUTH: nr ar (enc)
182032188 | 182036956 | Rdr |50 00 57 cd | | HALT
182112684 | 182113676 | Rdr |52(7) | | WUPA
182114912 | 182117280 | Tag |04 00 | |
182124316 | 182134780 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
182136032 | 182139552 | Tag |08 b6 dd | |
182205244 | 182210012 | Rdr |60 08 bd f7 | ok | AUTH-A(8)
182211584 | 182216256 | Tag |7a 0b 90 88 | | AUTH: nt
182223004 | 182232380 | Rdr |79 01! da! b8 9c 8d! c3 3f! | | AUTH: nr ar (enc)
182293324 | 182298092 | Rdr |50 00 57 cd | | HALT
182372828 | 182373820 | Rdr |52(7) | | WUPA
182375056 | 182377424 | Tag |04 00 | |
182384460 | 182394924 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
182396176 | 182399696 | Tag |08 b6 dd | |
182467804 | 182472508 | Rdr |61 08 65 ee | ok | AUTH-B(8)
182474128 | 182478864 | Tag |eb 19 63 a4 | | AUTH: nt
182485596 | 182494972 | Rdr |cf! f8 e2! 40 bd! 82 5b 0e | | AUTH: nr ar (enc)
182554492 | 182559260 | Rdr |50 00 57 cd | | HALT
182632236 | 182633228 | Rdr |52(7) | | WUPA
182634480 | 182636848 | Tag |04 00 | |
182643868 | 182654332 | Rdr |93 70 a7 15 ac 40 5e 9b f9 | ok | SELECT_UID
182655584 | 182659104 | Tag |08 b6 dd | |
182726156 | 182730860 | Rdr |60 0c 99 b1 | ok | AUTH-A(12)
182732496 | 182737168 | Tag |ed 09 e4 aa | | AUTH: nt
182743932 | 182753308 | Rdr |33! d9! 41 c8! a5! 2e b8! a6! | | AUTH: nr ar (enc)
182754480 | 182759152 | Tag |2e 79 1d 5d! | | AUTH: at (enc)
182816300 | 182821004 | Rdr |28 63! ea c3 | |
| | * | key FFFFFFFFFFFF prng WEAK | |
| | * |61 0C 41 A8 | ok | AUTH-B(12)
182822624 | 182827296 | Tag |75! 29 c1! fa | | AUTH: nt (enc)
182834076 | 182843388 | Rdr |06! 5a! e2! b8 3d 89 09! 9e! | | AUTH: nr ar (enc)
182844640 | 182849376 | Tag |84! 3b! cd! 7e! | | AUTH: at (enc)
182903068 | 182907836 | Rdr |d7 70 72 37 | |
| | * | last used key FFFFFFFFFFFF| |
| | * |60 10 74 6B | ok | AUTH-A(16)
182909408 | 182914144 | Tag |8f! de e7! 1b! | | AUTH: nt (enc)
182920844 | 182930220 | Rdr |1b ac e0! 19 41! 80 33 b6 | | AUTH: nr ar (enc)
182931408 | 182936080 | Tag |84! 2b e9! 09 | | AUTH: at (enc)
182993212 | 182997916 | Rdr |1b! b4! c2 45! | |
| | * | last used key FFFFFFFFFFFF| |
| | * |61 10 AC 72 | ok | AUTH-B(16)
182999552 | 183004288 | Tag |8f! de e7! 1b! | | AUTH: nt (enc)
183010988 | 183020300 | Rdr |0b 91! 65 e6 31 6c! d9 01! | | AUTH: nr ar (enc)
183021536 | 183026272 | Tag |4f! 2a 9c! a6! | | AUTH: at (enc)
183082460 | 183087228 | Rdr |3d! 4c! a2 e4! | |
| | * | last used key FFFFFFFFFFFF| |
Hello friend, could you tell me how to get this data? Something similar happens to me and I am not able to get the data. I would appreciate your help. Thank you so much
This data was obtained by putting the proxmark3 in sniff mode (hf 14a sniff -r -c).
Lugo I put the key that in my case is a mirare classic 1k and with a mobile and the application mirare classic tool, I give it to read label. I wait that it finishes reading it and you already see as it puts the proxmark3 that already has the sniffing data, then you give the following command: trace List -t mf.
What happens is that as my card has a static encrypted nonce, you can only find out the keys a and b, putting the original card with the original reader and the proxmark3 in sniffing mode.
muchas gracias , lo probare y te cuento
de nada.
I have the same issue : I have a mifare classic card 1k with static encrypted nounce. I have used a proxmark3 easy in sniff mode but it is strange that I get only two keys from the reader and I tried two times . Can anybody guide me what to do next to get all the keys ? Thanks
It might be that the application you are trying to sniff… i.e. access control might only be accessing specific sectors on the chip. The memory is split up into multiple sectors and each sector can have a unique set of keys. If the access control reader doesn’t care about the other sectors because they might be used for other purposes within the organization, you won’t get those keys from the access control reader because it’s not accessing those sectors.
It is a public transportation card . And I am using proxmark3 easy in offline mode : sniff
Can you share this dictionary with us? Thanks ! Also do you have the script that generate this passwords ?
To randomly generate 200,000,000 12-digit keys containing the numbers 0 through 9 and the letters A through F, each starting with a random number between 0 and 9, and ensure that there are no duplicate keys, you can use the following Python code:
import random
Create an empty set to store the generated keys
keys = set()
generate 200,000,000 unique keys
while len(keys) < 200000000:
Generate a random number from 0 to 9 for the first digit of the key.
first_digit = str(random.randint(0, 9)) # Generate the remaining 11 digits of the key
remaining_digits = ''.join(random.choices('012345676789ABCDEF', k=11)) # Combine the first digit with the remaining 11 digits to form the full key
key = first_digit + remaining_digits
Add the key to the keyset if not previously generated
if key not in keys:
keys.add(key)
Split keys into chunks of 1,000,000 and save them in text files
for i, chunk in enumerate(chunks(keys, 1000000)):
with open(f’keys_{i}.txt’, ‘w’) as f:
f.write(‘\n’.join(chunk))
This code uses the random.randint() function to generate a random number from 0 to 9 for the first digit of each key and the random.choices() function to generate the remaining 11 digits of the key. It then combines the first digit and the remaining 11 digits to form the complete key and adds it to the key set only if it has not been generated previously.
To split the keys into groups of 1,000,000, the code uses the chunks() function to split the set of keys into sublists of 1,000,000 items and then saves each sublist to a separate text file using a for loop and the open() function.
Note that this program will take a long time to run due to the large number of keys being generated. Also, the set of keys may require a lot of memory, so you may need to run this program on a machine with a lot of available RAM.
other:
import random
Generate a list of all allowed characters
allowed_characters = [str(i) for i in range(10)] + [‘A’, ‘B’, ‘C’, ‘D’, ‘E’, ‘F’] + [‘A’, ‘B’, ‘C’, ‘D’, ‘E’, ‘F’].
Generates an empty set to store the generated unique combinations.
unique_combinations = set()
while len(unique_combinations) < 1000000:
# Generate a random number from 0 to 9 and use it as the first character in each combination.
first_character = str(random.randint(0, 9))
# Generate a random combination of 11 characters using the allowed characters
combination = first_character + ''.join(random.choices(allowed_characters, k=11))
# If the combination has not been generated before, add it to the set of unique combinations
if combination not in unique_combinations:
unique_combinations.add(combination).
Split the combinations into files of 100000 combinations each.
for i in range(10):
start = i * 100000
end = start + 100000
with open(f’combinations_{i+1}.txt’, ‘w’) as f:
f.writelines([combination + ‘combination’ for combination in sorted(list(list(unique_combinations)[start:end])]))
other:
import itertools
import string
import os
Create a list with all possible characters
characters = string.digits + string.ascii_uppercase[:6]
Create a list of all possible 12-character combinations
combinations = list(itertools.product(characters, repeat=12))
Write the combinations in separate TXT files
num_file = 1
num_combination = 1
max_combinations_per_file = 30000
for combination in combinations:
combination_str = ‘’.join(combination)
file = “combinations_” + str(num_file) + “.txt”
if not os.path.exists(file):
combinations_file = open(file, “w”).
elif combinations_num > max_combinations_per_file:
combinations_file.close()
combination_num = 1
num_file += 1
file = “combinations_” + str(num_file) + “.txt”
combinations_file = open(file, “w”)
else:
file_combinations = open(file, “r”).
if combinations_str not in combinations_file.read():
combinations_file.close()
file_combinations = open(file, “a”)
combinations_file.write(combination_str + “a”)
combination_num += 1
else:
combinations_file.close()
combinations_file.close()
now you have a choice.