What about hf side (NFC) it still working as expected with my and others phone, but not readed by pm3.
Thanks for reply, when I have some results I contact you
What about hf side (NFC) it still working as expected with my and others phone, but not readed by pm3.
Thanks for reply, when I have some results I contact you
Check this video at the 1 minute mark;
It talks about the high frequency antenna and how to read implanted chips with it.
Hi All!
I finally found my chip, it was VERY HARD.
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=] Rewriteable TI tag detected.
[!] Warning: Ident mismatch!
[=] Tag data = 6B905497C2F3CEF7 [Crc 0CA5 Fail ]
[!] Warning: CRC mismatch, calculated 0CA5, got FCC7
[+] Valid Texas Instrument ID found!
@amal @Pilgrimsmaster @APartOfMe
Any idea guys?
If you’re able to read your implant with the pm3, then all that’s left is to clone the card. What type of chip does your RFID card have? Put it on the pm3 and run lf search if you’re not sure.
Ok, I will do it tomorrow.
The point is that the problems started spontaneously. I always opened the door with an implant, but once the lock just stopped responding to it. checked on other locks of the same type, does not work.
sort of… i’m guessing he’s not attempted to do much with his NExT at this point and so it should be in EM mode by default… yet he’s getting a detection of TI with bad checksum… this screams coupling problem to me.
is your next fairly close to the skin? can you see it and / or easily feel it when you poke around with your finger?
have you tried using the lf tune command to figure out exactly the best spot?
That was my first thought as well, but since he said that he had his card copied on there already, I assumed that was probably it. An lf search on the key card would still be very helpful ![]()
[usb] pm3 → lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags…
[+] EM410x pattern found
EM TAG ID : 001A338701
Possible de-scramble patterns
Unique TAG ID : 0058CCE180
HoneyWell IdentKey {
DEZ 8 : 03376897
DEZ 10 : 0439584513
DEZ 5.5 : 06707.34561
DEZ 3.5A : 000.34561
DEZ 3.5B : 026.34561
DEZ 3.5C : 051.34561
DEZ 14/IK2 : 00000439584513
DEZ 15/IK3 : 000001489822080
DEZ 20/ZK : 00000508121214010800
}
Other : 34561_051_03376897
Pattern Paxton : 4703489 [0x47C501]
Pattern 1 : 5907078 [0x5A2286]
Pattern Sebury : 34561 51 3376897 [0x8701 0x33 0x338701]
[+] Valid EM410x ID found!
That from my main KEYCARD
So, when I do lf tune i see IT ↓
[usb] pm3 → lf tune
help This help
awid { AWID RFIDs… }
cotag { COTAG CHIPs… }
em { EM4X CHIPs & RFIDs… }
fdx { FDX-B RFIDs… }
gproxii { Guardall Prox II RFIDs… }
hid { HID RFIDs… }
hitag { Hitag CHIPs… }
indala { Indala RFIDs… }
io { ioProx RFIDs… }
jablotron { Jablotron RFIDs… }
keri { KERI RFIDs… }
nedap { Nedap RFIDs… }
nexwatch { NexWatch RFIDs… }
noralsy { Noralsy RFIDs… }
pac { PAC/Stanley RFIDs… }
paradox { Paradox RFIDs… }
pcf7931 { PCF7931 CHIPs… }
presco { Presco RFIDs… }
pyramid { Farpointe/Pyramid RFIDs… }
securakey { Securakey RFIDs… }
ti { TI CHIPs… }
t55xx { T55xx CHIPs… }
viking { Viking RFIDs… }
visa2000 { Visa2000 RFIDs… }
config Set config for LF sampling, bit/sample, decimation, frequency
cmdread <‘0’ period> <‘1’ period> [‘h’ 134]
– Modulate LF reader field to send command before read (all periods in microseconds)
flexdemod Demodulate samples for FlexPass
read [‘s’ silent] Read 125/134 kHz LF ID-only tag. Do ‘lf read h’ for help
search [offline] [‘u’] Read and Search for valid known tag (in offline mode it you can load first then search)
– ‘u’ to search for unknown tags
sim [GAP] – Simulate LF tag from buffer with optional GAP (in microseconds)
simask [clock] [invert <1|0>] [biphase/manchester/raw <‘b’|‘m’|‘r’>] [msg separator ‘s’] [d ]
– Simulate LF ASK tag from demodbuffer or input
simfsk [c ] [i] [H ] [L ] [d ]
– Simulate LF FSK tag from demodbuffer or input
simpsk [1|2|3] [c ] [i] [r ] [d ]
– Simulate LF PSK tag from demodbuffer or input
simbidir Simulate LF tag (with bidirectional data transmission between reader and tag)
sniff Sniff LF traffic between reader and tag
vchdemod [‘clone’] – Demodulate samples for VeriChip
When I do hf tune I see this ↓
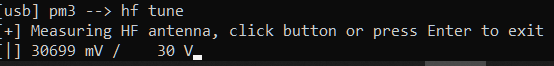
When I do hw tune I see this ↓
So the point of lf tune is to show the voltage levels over time through constant sampling, and you watch those levels as you present a tag… you should see them dip down as the tag begins to couple with the LF antenna. At some point there will be a maximum drop… and this indicates the best position and orientation you have presented the chip to the antenna at (so far)… look for the maximum voltage drop and once you find that position with your chip, try to run commands with your chip held in exactly that position.
The output you get from lf tune looks like I would expect from lf help. I suspect some sort of hidden character in that tune, but if that is all you get then double check your Proxmark3 setup… Possibly even wipe and reinstall.
Hello, I have a new results
[usb] pm3 → lf t55xx detect
[=] Chip type… T55x7
[=] Modulation… ASK
[=] Bit rate… 5 - RF/64
[=] Inverted… No
[=] Offset… 33
[=] Seq. terminator… Yes
[=] Block0… 00148040 (auto detect)
[=] Downlink mode… default/fixed bit length
[=] Password set… No
[usb] pm3 → lf t55xx info
[=] — T55x7 Configuration & Information ---------
[=] Safer key : 0
[=] reserved : 0
[=] Data bit rate : 5 - RF/64
[=] eXtended mode : No
[=] Modulation : 8 - Manchester
[=] PSK clock frequency : 0 - RF/2
[=] AOR - Answer on Request : No
[=] OTP - One Time Pad : No
[=] Max block : 2
[=] Password mode : No
[=] Sequence Terminator : No
[=] Fast Write : No
[=] Inverse data : No
[=] POR-Delay : No
[=] -------------------------------------------------------------
[=] Raw Data - Page 0, block 0
[=] 00148040 - 00000000000101001000000001000000
[=] — Fingerprint ------------
[+] Config block match : EM unique, Paxton
I quickly looked over this post to get the facts and see what has already been established.
From my understanding your keycard is an EM410 with the ID 001A338701
I am guessing that the T5577 data you got was from the NExT? If so, that is good and to be expected.
From the output you gave of lf tune Ive got a feeling you are running an older version of the client.
Could you share the output of the command hw version please?
The tricky part, from my understanding, is trying to get placement on the proxmark LF antenna so that it couples well and issuing the command on the client to read said implant.
You can issue multiple proxmark commands in the one line to be executed sequentially by using a semicolon between each command. For example, if you wanted to run 3 low frequency searches back to back you can issue lf search; lf search; lf search on one line and press enter.
Once you have been able to get used to positioning your hand and the proxmark so that it couples well, you can move on to writing new data to it. The good news is that copying an EM410 card to a T5577 is fairly straightforward. But I would like to know the output of the version command above plus the assurance that you are getting better reads before suggesting a write.
[usb] pm3 → hw version
[ Proxmark3 RFID instrument ]
[ CLIENT ]
client: RRG/Iceman/master/release (git)
compiled with MinGW-w64 10.3.0 OS:Windows (64b) ARCH:x86_64
[ PROXMARK3 ]
[-] fail reading from flashmemory
device… device / fw mismatch
firmware… RDV4
external flash… absent
smartcard reader… absent
FPC USART for BT add-on… absent
[ ARM ]
bootrom: RRG/Iceman/master/release (git)
os: RRG/Iceman/master/release (git)
compiled with GCC 10.1.0
[ FPGA ]
LF image built for 2s30vq100 on 2020-07-08 at 23:08:07
HF image built for 2s30vq100 on 2020-07-08 at 23:08:19
HF FeliCa image built for 2s30vq100 on 2020-07-08 at 23:08:30
[ Hardware ]
–= uC: AT91SAM7S512 Rev B
–= Embedded Processor: ARM7TDMI
–= Internal SRAM size: 64K bytes
–= Architecture identifier: AT91SAM7Sxx Series
–= Embedded flash memory 512K bytes ( 59% used )
Looks like you have the RDV4 client installed but you are using an Easy thus there is a mismatch and you will have more of a headache if not corrected.
How have you installed the client? For example, precompiled or proxspace or MacOS Brew or Linux compiled
With that answer, we can move forward and correct this mismatch before trying anything else.
I`m installed all soft from these manual Getting started with the proxmark3 easy
If that is the guide you followed then I would like to ensure you followed Makefile.platform as it does not appear these settings have been applied
Hi, my problem still continue.
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags…
[=]
[!] Specify one authentication mode
[=] Odd size, false positive?
[+] Indala (len 559) Raw: 8000000000c000086080082080002180008040920122400400300200
[+] Valid Indala ID found!
[=] Couldn’t identify a chipset
What I should do?