Hello, I am trying to clone a card I have from plicards.com using my proxmark3 .
From my research of this forum, it looks like I need to sniff the reader interaction with the card.
[usb] pm3 --> hf mf chk
[+] loaded 56 keys from hardcoded default array
[=] Start check for keys...
[=] .................................
[=] time in checkkeys 7 seconds
[=] testing to read key B...
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 001 | 007 | 2A2C13CC242A | 1 | FFFFFFFFFFFF | 1
[+] 002 | 011 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 003 | 015 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 004 | 019 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 005 | 023 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 006 | 027 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 007 | 031 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 008 | 035 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 009 | 039 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 010 | 043 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 011 | 047 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 012 | 051 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 013 | 055 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 014 | 059 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 015 | 063 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] -----+-----+--------------+---+--------------+----
[+] ( 0:Failed / 1:Success )
[usb] pm3 --> hf mf nested --1k --blk 0 -b -k FFFFFFFFFFFF
[+] Testing known keys. Sector count 16
[=] ..
[=] Chunk 4.5s | found 18/32 keys (57)
[+] Time to check 56 known keys: 5 seconds
[+] enter nested key recovery
[-] ⛔ Tag isn't vulnerable to Nested Attack (PRNG is not predictable)
Now if I am correct I would use the following to sniff:
hf 14a sniff -r -rc
My question is what happens from here? I run the sniff command, put the proxmark3 between the card and the reader and try that a few times before pressing the button on the proxmark3 .
What happens from there? How do I use that to crack the remaining keys? Also, have two cards currently, one that is “active” in the entry system and one that is “expired”, is there any issue running my expired one or should I use my “active” one.
For further detail, this is for a ski condo I own and as an owner they will only give me so many cards. I am hoping to run the card on my Chameleon Ultra or write to a magic card to keep in different ski jackets.
Have you tried hf mf auto?
Also, I see you have a device/firmware mismatch with the PM3 client, this could cause you some trouble and is worth investigating
2 Likes
Yes:
[usb] pm3 --> hf mf auto
[!] ⚠️ no known key was supplied, key recovery might fail
[+] loaded 56 keys from hardcoded default array
[=] running strategy 1
[=] ..
[=] Chunk 4.4s | found 18/32 keys (56)
[=] running strategy 2
[=] ..
[=] Chunk 4.4s | found 18/32 keys (56)
[+] target sector 0 key type B -- found valid key [ FFFFFFFFFFFF ] (used for nested / hardnested attack)
[+] target sector 1 key type A -- found valid key [ 2A2C13CC242A ]
[+] target sector 1 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 2 key type A -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 2 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 3 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 4 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 5 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 6 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 7 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 8 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 9 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 10 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 11 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 12 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 13 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 14 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 15 key type B -- found valid key [ FFFFFFFFFFFF ]
[-] ⛔ Tag isn't vulnerable to Nested Attack (PRNG is probably not predictable).
[-] ⛔ Nested attack failed --> try hardnested
[=] Hardnested attack starting...
[=] ---------+---------+---------------------------------------------------------+-----------------+-------
[=] | | | Expected to brute force
[=] Time | #nonces | Activity | #states | time
[=] ---------+---------+---------------------------------------------------------+-----------------+-------
[=] 0 | 0 | Start using 10 threads and NEON SIMD core | |
[=] 0 | 0 | Brute force benchmark: 1915 million (2^30.8) keys/s | 140737488355328 | 20h
[=] 0 | 0 | Loaded 0 RAW / 351 LZ4 / 0 BZ2 in 395 ms | 140737488355328 | 20h
[=] 0 | 0 | Using 239 precalculated bitflip state tables | 140737488355328 | 20h
[!!] 🚨 Error: Static encrypted nonce detected. Aborted
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 001 | 007 | 2A2C13CC242A | D | FFFFFFFFFFFF | D
[+] 002 | 011 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 003 | 015 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 004 | 019 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 005 | 023 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 006 | 027 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 007 | 031 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 008 | 035 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 009 | 039 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 010 | 043 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 011 | 047 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 012 | 051 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 013 | 055 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 014 | 059 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 015 | 063 | ------------ | 0 | FFFFFFFFFFFF | D
[+] -----+-----+--------------+---+--------------+----
[=] ( D:Dictionary / S:darkSide / U:User / R:Reused / N:Nested / H:Hardnested / C:statiCnested / A:keyA )
I got “Static encrypted nonce detected” which made me think I need to go the sniffer route.
1 Like
XEMON
December 28, 2023, 2:06am
4
I had the same output on a MF card recently but haven’t gotten the time to dig into it, let me find it and we can share experiments
1 Like
amal
December 28, 2023, 2:54am
5
Always look for this
I would do a pull on the repo, make clean, make all, reflash the device. Also be sure you are compiling for the correct hardware platform as the default is the RDV4 version of hardware.
Whenever there is a client / firmware mismatch, behavior is unreliable. This has to be solved first before anything else.
2 Likes
I realized I used the wrong screenshot on my desktop when I uploaded that. The device/fw do match.
1 Like
Here is the full terminal log.
I believe that what I need to do next when I am with the reader is the following. Is this correct?
hf 14a sniff -r -rcSTART SNIFF
trace list -t mfTO DECODE SNIFF DATA
hf mfdes listLIST TRACE DATA
trace save -f FILENAMESAVE TRACE DATA
trace load -f FILENAMELOAD TRACE FILE TO EMULATE CARD
8888888b. 888b d888 .d8888b.
888 Y88b 8888b d8888 d88P Y88b
888 888 88888b.d88888 .d88P
888 d88P 888Y88888P888 8888"
8888888P" 888 Y888P 888 "Y8b.
888 888 Y8P 888 888 888
888 888 " 888 Y88b d88P
888 888 888 "Y8888P" [ ☕ ]
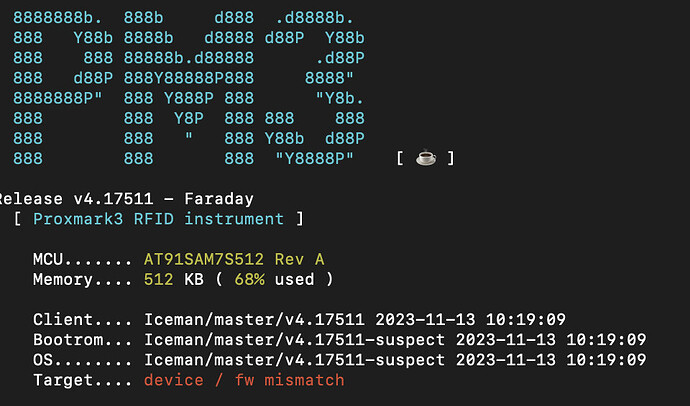
Release v4.17511 - Faraday
[ Proxmark3 RFID instrument ]
MCU....... AT91SAM7S512 Rev A
Memory.... 512 KB ( 61% used )
Client.... Iceman/master/v4.17511 2023-11-13 10:19:09
Bootrom... Iceman/master/v4.17511-suspect 2023-11-13 10:19:09
OS........ Iceman/master/v4.17511-suspect 2023-11-13 10:19:09
Target.... PM3 GENERIC
[usb] pm3 --> hf mf fchk
[+] loaded 56 keys from hardcoded default array
[=] Running strategy 1
[=] ..
[=] Chunk 4.4s | found 18/32 keys (56)
[=] Running strategy 2
[=] ..
[=] Chunk 4.4s | found 18/32 keys (56)
[=] time in checkkeys (fast) 8.9s
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 001 | 007 | 2A2C13CC242A | 1 | FFFFFFFFFFFF | 1
[+] 002 | 011 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 003 | 015 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 004 | 019 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 005 | 023 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 006 | 027 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 007 | 031 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 008 | 035 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 009 | 039 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 010 | 043 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 011 | 047 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 012 | 051 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 013 | 055 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 014 | 059 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 015 | 063 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] -----+-----+--------------+---+--------------+----
[+] ( 0:Failed / 1:Success )
[usb] pm3 --> hf mf nested --1k --blk 0 -b -k FFFFFFFFFFFF
[+] Testing known keys. Sector count 16
[=] ..
[=] Chunk 4.5s | found 18/32 keys (57)
[+] Time to check 56 known keys: 5 seconds
[+] enter nested key recovery
[-] ⛔ Tag isn't vulnerable to Nested Attack (PRNG is not predictable)
[usb] pm3 --> hf mf auto
[!] ⚠️ no known key was supplied, key recovery might fail
[+] loaded 56 keys from hardcoded default array
[=] running strategy 1
[=] ..
[=] Chunk 4.4s | found 18/32 keys (56)
[=] running strategy 2
[=] ..
[=] Chunk 4.4s | found 18/32 keys (56)
[+] target sector 0 key type B -- found valid key [ FFFFFFFFFFFF ] (used for nested / hardnested attack)
[+] target sector 1 key type A -- found valid key [ 2A2C13CC242A ]
[+] target sector 1 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 2 key type A -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 2 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 3 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 4 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 5 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 6 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 7 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 8 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 9 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 10 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 11 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 12 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 13 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 14 key type B -- found valid key [ FFFFFFFFFFFF ]
[+] target sector 15 key type B -- found valid key [ FFFFFFFFFFFF ]
[-] ⛔ Tag isn't vulnerable to Nested Attack (PRNG is probably not predictable).
[-] ⛔ Nested attack failed --> try hardnested
[=] Hardnested attack starting...
[=] ---------+---------+---------------------------------------------------------+-----------------+-------
[=] | | | Expected to brute force
[=] Time | #nonces | Activity | #states | time
[=] ---------+---------+---------------------------------------------------------+-----------------+-------
[=] 0 | 0 | Start using 10 threads and NEON SIMD core | |
[=] 0 | 0 | Brute force benchmark: 1827 million (2^30.8) keys/s | 140737488355328 | 21h
[=] 0 | 0 | Loaded 0 RAW / 351 LZ4 / 0 BZ2 in 381 ms | 140737488355328 | 21h
[=] 0 | 0 | Using 239 precalculated bitflip state tables | 140737488355328 | 21h
[!!] 🚨 Error: Static encrypted nonce detected. Aborted
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 001 | 007 | 2A2C13CC242A | D | FFFFFFFFFFFF | D
[+] 002 | 011 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 003 | 015 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 004 | 019 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 005 | 023 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 006 | 027 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 007 | 031 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 008 | 035 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 009 | 039 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 010 | 043 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 011 | 047 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 012 | 051 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 013 | 055 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 014 | 059 | ------------ | 0 | FFFFFFFFFFFF | D
[+] 015 | 063 | ------------ | 0 | FFFFFFFFFFFF | D
[+] -----+-----+--------------+---+--------------+----
[=] ( D:Dictionary / S:darkSide / U:User / R:Reused / N:Nested / H:Hardnested / C:statiCnested / A:keyA )
I was able to sniff the door a few times but loading the sniff lead to a failed authorization at the reader. What is the process for cracking this?
I attached my two trace files. This is a different key:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 001 | 007 | 2A2C13CC242A | 1 | FFFFFFFFFFFF | 1
[+] 002 | 011 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 003 | 015 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 004 | 019 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 005 | 023 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 006 | 027 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 007 | 031 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 008 | 035 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 009 | 039 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 010 | 043 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 011 | 047 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 012 | 051 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 013 | 055 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 014 | 059 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] 015 | 063 | ------------ | 0 | FFFFFFFFFFFF | 1
[+] -----+-----+--------------+---+--------------+----
Archive.zip (6.7 KB)
1 Like
Jirvin
December 30, 2023, 9:03pm
10
Since you are using a PM3 Easy, there is no performance gain using fchk but, conversely, there is no performance impact.
The main thing you are missing is specifying the dictionary of keys to use when running the key keys command. This is limiting the number of keys the PM3 will check the card with to 56 keys compared to the >1000 keys in the bundled dictionary file.hf mf chk -h to find how to specify the bundled MFC dictionary.
I havent taken a look at the sniffs as you should be able to recover the keys without them. The sniffs are mainly beneficial for understanding read to tag comms but can be used to recover keys.
Given you already have a known key A and key B, you can use these to recover the not found keys. You attempted to perform key recovery using the nested attack but its unclear what PRNG the card has to comment on what method should be used. Please issue hf 14 info to the card and post the output (the UID can be removed/hidden if needed)
Once you have all the keys and a dump of the card, what is your next step? Eg clone to implant/card/fob, emulate using PM3 /other device, edit card details, reverse engineer card contents etc.
Looks like it was my fault. I was using one of my expired cards so the reader wouldn’t give me access to the door. I was able to successfully clone the card over to my Chameleon Utlra.
How can I share the found keys to the Proxmark3 dictionary so others can use them in the future when trying to clone similar cards?
I went to clone some key tags my friend had on hand, but I am no longer near the reader to test. Are the first two failed blocks an issue?
[usb] pm3 --> hf mf csetuid -u B7EC7744 --atqa 0004 --sak 08
[+] old block 0... EC39D63C3F0804006263646566676869
[+] new block 0... B7EC7744680804006263646566676869
[+] Old UID... EC 39 D6 3C
[+] New UID... B7 EC 77 44 ( verified )
[usb] pm3 --> hf mf restore --1k -u B7EC7744 -k hf-mf-B7EC7744-key.bin
[=] Using key file `hf-mf-B7EC7744-key.bin`
[+] loaded 1024 bytes from binary file `hf-mf-B7EC7744-dump.bin`
[=] blk | data | status
[=] -----+-------------------------------------------------+----------------
[=] 0 | B7 EC 77 44 68 08 04 00 62 63 64 65 66 67 68 69 | ( fail ) key B
[=] 0 | B7 EC 77 44 68 08 04 00 62 63 64 65 66 67 68 69 | ( fail ) key A
[=] 1 | E9 63 F0 69 20 36 64 AE BF 51 49 87 44 8A 71 DE | ( ok )
[=] 2 | 8A 00 04 00 01 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 3 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 4 | 53 00 48 00 00 00 00 00 00 00 00 C1 00 00 00 25 | ( ok )
[=] 5 | 53 00 48 00 00 00 00 00 00 00 00 C1 00 00 00 25 | ( ok )
[=] 6 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 7 | 2A 2C 13 CC 24 2A FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 8 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 9 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 10 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 11 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 12 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 13 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 14 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 15 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 16 | AB 4C 43 3A 21 0B 00 A0 AB 4C 43 51 21 07 00 B3 | ( ok )
[=] 17 | AB 4C 43 4F 21 0B 00 B5 AB 4C 4A C4 20 20 00 45 | ( ok )
[=] 18 | AB 4C 54 36 20 20 00 C1 AB 4C 5B 28 20 20 00 BA | ( ok )
[=] 19 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 20 | AB 4C 5B 24 21 07 00 9E AB 4C 62 7A 20 20 00 13 | ( ok )
[=] 21 | AB 4C 63 60 21 07 00 E2 AB 4C 63 5E 21 0B 00 E4 | ( ok )
[=] 22 | AB 4C 6A A0 20 20 00 41 AB 4C 74 99 20 20 00 44 | ( ok )
[=] 23 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 24 | AB 4C 74 95 21 07 00 28 AB 4C 7A FA 20 20 00 AB | ( ok )
[=] 25 | AB 4C 7C 4A 20 20 00 FD AB 4C 82 9F 20 20 00 58 | ( ok )
[=] 26 | AB 4C 9B 2F 20 20 00 01 AB 4C 9B 2D 21 07 00 E7 | ( ok )
[=] 27 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 28 | AB 4C 9B 61 20 E2 00 F5 AB 4C A3 5D 20 20 00 37 | ( ok )
[=] 29 | AB 4C A4 82 20 20 00 5D AB 4C A4 7B 21 07 00 3E | ( ok )
[=] 30 | AB 4C AA 1C 20 20 00 FD AB 4C AA 21 21 07 00 EA | ( ok )
[=] 31 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 32 | AB 4C AA CE 20 E2 00 71 AB 4C BB 40 20 20 00 32 | ( ok )
[=] 33 | AB 4C C2 E7 20 20 00 E0 AB 4C C2 E9 21 07 00 CA | ( ok )
[=] 34 | 2B 4C C3 68 20 A2 74 D8 AB 4C CB 22 20 20 00 24 | ( ok )
[=] 35 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 36 | AB 4C D4 DC 20 20 00 E7 AB 4C D4 D9 21 07 00 CC | ( ok )
[=] 37 | AB 4C DA EE 20 20 00 FF AB 4C E2 B3 20 20 00 CC | ( ok )
[=] 38 | AB 4C F2 F2 21 07 00 03 AB 4C F2 F2 21 07 00 03 | ( ok )
[=] 39 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 40 | AB 4C F2 F3 21 07 00 04 AB 4C F2 F4 21 07 00 05 | ( ok )
[=] 41 | AB 4C F2 F6 21 07 00 07 AB 4B BA 9B 20 20 00 8B | ( ok )
[=] 42 | AB 4B BB 73 20 20 00 64 AB 4B C2 EF 20 20 00 E7 | ( ok )
[=] 43 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 44 | AB 4B C2 EE 21 07 00 CE AB 4B CA F6 20 20 00 F6 | ( ok )
[=] 45 | AB 4B CA F2 21 07 00 DA AB 4B D4 DE 20 20 00 E8 | ( ok )
[=] 46 | AB 4B D4 DA 21 07 00 CC AB 4B D4 D9 21 0B 00 CF | ( ok )
[=] 47 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 48 | AB 4B DB 66 20 20 00 77 AB 4B DB 62 21 07 00 5B | ( ok )
[=] 49 | AB 4B DB DE 20 20 00 EF AB 4B DC F1 20 20 00 03 | ( ok )
[=] 50 | AB 4B DC EC 21 07 00 E6 AB 4B EB 96 20 20 00 B7 | ( ok )
[=] 51 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 52 | AB 4B EB 92 21 07 00 9B AB 4B F2 99 20 20 00 C1 | ( ok )
[=] 53 | AB 4B F2 98 21 07 00 A8 AB 4C 0B 2B 20 20 00 6D | ( ok )
[=] 54 | AB 4C 0B 29 21 07 00 53 AB 4C 12 DA 20 20 00 23 | ( ok )
[=] 55 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 56 | AB 4C 13 E2 20 20 00 2C AB 4C 13 DE 21 0B 00 14 | ( ok )
[=] 57 | AB 4C 22 8E 20 20 00 E7 AB 4C 22 8E 21 07 00 CF | ( ok )
[=] 58 | AB 4C 22 C8 21 07 00 09 AB 4C 2A DD 20 20 00 3E | ( ok )
[=] 59 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 60 | AB 4C 2A DB 21 07 00 24 AB 4C 2B 13 21 07 00 5D | ( ok )
[=] 61 | AB 4C 2C 34 20 20 00 97 AB 4C 3B 95 20 20 00 07 | ( ok )
[=] 62 | AB 4C 3B 92 21 07 00 EC AB 4C 42 B0 20 20 00 29 | ( ok )
[=] 63 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] -----+-------------------------------------------------+----------------
[=] Done!
[usb] pm3 --> hf mf csetuid -u B7EC7744 --atqa 0004 --sak 08
[+] old block 0... BA55D63C050804006263646566676869
[+] new block 0... B7EC7744680804006263646566676869
[+] Old UID... BA 55 D6 3C
[+] New UID... B7 EC 77 44 ( verified )
[usb] pm3 --> hf mf restore --1k -u B7EC7744 -k hf-mf-B7EC7744-key.bin
[=] Using key file `hf-mf-B7EC7744-key.bin`
[+] loaded 1024 bytes from binary file `hf-mf-B7EC7744-dump.bin`
[=] blk | data | status
[=] -----+-------------------------------------------------+----------------
[=] 0 | B7 EC 77 44 68 08 04 00 62 63 64 65 66 67 68 69 | ( fail ) key B
[=] 0 | B7 EC 77 44 68 08 04 00 62 63 64 65 66 67 68 69 | ( fail ) key A
[=] 1 | E9 63 F0 69 20 36 64 AE BF 51 49 87 44 8A 71 DE | ( ok )
[=] 2 | 8A 00 04 00 01 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 3 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 4 | 53 00 48 00 00 00 00 00 00 00 00 C1 00 00 00 25 | ( ok )
[=] 5 | 53 00 48 00 00 00 00 00 00 00 00 C1 00 00 00 25 | ( ok )
[=] 6 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 7 | 2A 2C 13 CC 24 2A FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 8 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 9 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 10 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 11 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 12 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 13 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 14 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ( ok )
[=] 15 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 16 | AB 4C 43 3A 21 0B 00 A0 AB 4C 43 51 21 07 00 B3 | ( ok )
[=] 17 | AB 4C 43 4F 21 0B 00 B5 AB 4C 4A C4 20 20 00 45 | ( ok )
[=] 18 | AB 4C 54 36 20 20 00 C1 AB 4C 5B 28 20 20 00 BA | ( ok )
[=] 19 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 20 | AB 4C 5B 24 21 07 00 9E AB 4C 62 7A 20 20 00 13 | ( ok )
[=] 21 | AB 4C 63 60 21 07 00 E2 AB 4C 63 5E 21 0B 00 E4 | ( ok )
[=] 22 | AB 4C 6A A0 20 20 00 41 AB 4C 74 99 20 20 00 44 | ( ok )
[=] 23 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 24 | AB 4C 74 95 21 07 00 28 AB 4C 7A FA 20 20 00 AB | ( ok )
[=] 25 | AB 4C 7C 4A 20 20 00 FD AB 4C 82 9F 20 20 00 58 | ( ok )
[=] 26 | AB 4C 9B 2F 20 20 00 01 AB 4C 9B 2D 21 07 00 E7 | ( ok )
[=] 27 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 28 | AB 4C 9B 61 20 E2 00 F5 AB 4C A3 5D 20 20 00 37 | ( ok )
[=] 29 | AB 4C A4 82 20 20 00 5D AB 4C A4 7B 21 07 00 3E | ( ok )
[=] 30 | AB 4C AA 1C 20 20 00 FD AB 4C AA 21 21 07 00 EA | ( ok )
[=] 31 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 32 | AB 4C AA CE 20 E2 00 71 AB 4C BB 40 20 20 00 32 | ( ok )
[=] 33 | AB 4C C2 E7 20 20 00 E0 AB 4C C2 E9 21 07 00 CA | ( ok )
[=] 34 | 2B 4C C3 68 20 A2 74 D8 AB 4C CB 22 20 20 00 24 | ( ok )
[=] 35 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 36 | AB 4C D4 DC 20 20 00 E7 AB 4C D4 D9 21 07 00 CC | ( ok )
[=] 37 | AB 4C DA EE 20 20 00 FF AB 4C E2 B3 20 20 00 CC | ( ok )
[=] 38 | AB 4C F2 F2 21 07 00 03 AB 4C F2 F2 21 07 00 03 | ( ok )
[=] 39 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 40 | AB 4C F2 F3 21 07 00 04 AB 4C F2 F4 21 07 00 05 | ( ok )
[=] 41 | AB 4C F2 F6 21 07 00 07 AB 4B BA 9B 20 20 00 8B | ( ok )
[=] 42 | AB 4B BB 73 20 20 00 64 AB 4B C2 EF 20 20 00 E7 | ( ok )
[=] 43 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 44 | AB 4B C2 EE 21 07 00 CE AB 4B CA F6 20 20 00 F6 | ( ok )
[=] 45 | AB 4B CA F2 21 07 00 DA AB 4B D4 DE 20 20 00 E8 | ( ok )
[=] 46 | AB 4B D4 DA 21 07 00 CC AB 4B D4 D9 21 0B 00 CF | ( ok )
[=] 47 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 48 | AB 4B DB 66 20 20 00 77 AB 4B DB 62 21 07 00 5B | ( ok )
[=] 49 | AB 4B DB DE 20 20 00 EF AB 4B DC F1 20 20 00 03 | ( ok )
[=] 50 | AB 4B DC EC 21 07 00 E6 AB 4B EB 96 20 20 00 B7 | ( ok )
[=] 51 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 52 | AB 4B EB 92 21 07 00 9B AB 4B F2 99 20 20 00 C1 | ( ok )
[=] 53 | AB 4B F2 98 21 07 00 A8 AB 4C 0B 2B 20 20 00 6D | ( ok )
[=] 54 | AB 4C 0B 29 21 07 00 53 AB 4C 12 DA 20 20 00 23 | ( ok )
[=] 55 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 56 | AB 4C 13 E2 20 20 00 2C AB 4C 13 DE 21 0B 00 14 | ( ok )
[=] 57 | AB 4C 22 8E 20 20 00 E7 AB 4C 22 8E 21 07 00 CF | ( ok )
[=] 58 | AB 4C 22 C8 21 07 00 09 AB 4C 2A DD 20 20 00 3E | ( ok )
[=] 59 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] 60 | AB 4C 2A DB 21 07 00 24 AB 4C 2B 13 21 07 00 5D | ( ok )
[=] 61 | AB 4C 2C 34 20 20 00 97 AB 4C 3B 95 20 20 00 07 | ( ok )
[=] 62 | AB 4C 3B 92 21 07 00 EC AB 4C 42 B0 20 20 00 29 | ( ok )
[=] 63 | A1 FB 44 84 70 AF FF 07 80 69 FF FF FF FF FF FF | ( ok )
[=] -----+-------------------------------------------------+----------------
[=] Done!