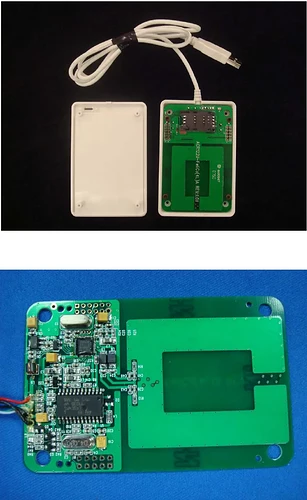
I finished a new project recently that lets me unlock my computer using my blinky XSIID implant. The script also passes data scanned to a website if needed, so I can also badge into custom websites I build. I’m using a few basic python packages, as well as systemd, i3lock, and the MIRKOE2540 NFC USB dongle. This seems to be the only USB device I’ve been able to find that will scan my implant.
To use this, install Python and i3lock. Replace tokens and text_tokens with the ID and text written to the implant or NFC card. Install this script with a virtual environment in an encrypted home directory, and add the below daemons to systemd. Install the MIKROE2540 linux example in /etc/nxp. (use the product page, or this link: https://www.nxp.com/doc/SW4335)
tokens = ['00 00 00 00 00 00 00']
text_tokens = ['<randomly generated text on the implant here>']
lock_at_seconds = 60 * 60
for token in tokens:
token = token.replace(':', ' ')
token = 'NFCID = ' + token
for token in text_tokens:
token = token.replace(':', ' ')
token = 'Text record: ' + token
import logging
from websocket_server import WebsocketServer
server = WebsocketServer(host='localhost', port=13254, loglevel=logging.INFO) #, key="key.pem", cert="cert.pem")
def run():
global server
server.run_forever()
import os, subprocess, time, threading, multiprocessing
thread = threading.Thread(target=run)
thread.start()
from datetime import datetime
def count_to_lock():
while True:
seconds = (datetime.now() - (datetime.now().replace(minute=0))).total_seconds()
lock_at_seconds = 60 * 60
while seconds < lock_at_seconds:
time.sleep(1)
seconds += 1
subprocess.Popen(['/usr/bin/i3lock'], stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
seconds = 0
def run_process(client):
ls = None
op = None
lock_at_seconds = 60 * 60
seconds = (datetime.now() - (datetime.now().replace(minute=0))).total_seconds()
while not op or 'No such' in op:
ls = subprocess.Popen(['/usr/bin/ls', '/dev/hidraw2'], stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
op = str(ls.stdout.readline().rstrip(), encoding='utf-8')
print('NFC Daemon Active')
seconds += 1
if not seconds < lock_at_seconds:
subprocess.Popen(['/usr/bin/i3lock'], stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
seconds = 0
time.sleep(1)
subprocess.Popen(['/usr/bin/sudo', 'chmod', 'a+rw', '/dev/hidraw2'], stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
import asyncio
async def main():
primary_index = -1
secondary_index = -2
proc = await asyncio.create_subprocess_exec(
'stdbuf', '-o0', "/etc/nxp",
stdout=asyncio.subprocess.PIPE,
)
process = multiprocessing.Process(target=count_to_lock)
process.start()
line = await proc.stdout.readline()
while line:
print(line.decode())
line = await proc.stdout.readline()
decoded = line.decode()
for token in tokens:
if token in decoded:
primary_index = tokens.index(token)
for token in text_tokens:
if token in decoded:
secondary_index = text_tokens.index(token)
if primary_index == secondary_index:
subprocess.Popen(['/usr/bin/killall', 'i3lock'], stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
primary_index = -1
secondary_index = -2
client.send_message_to_all(decoded)
process.terminate()
asyncio.run(main())
while True:
seconds = (datetime.now() - (datetime.now().replace(minute=0))).total_seconds()
lock_at_seconds = 60 * 60
while seconds < lock_at_seconds:
run_process(server)
time.sleep(3)
seconds += 3
subprocess.Popen(['/usr/bin/i3lock'], stdout=subprocess.PIPE, stderr=subprocess.STDOUT)
seconds = 0
This configuration runs the NFC python file at boot.
/etc/systemd/system/nfc.service
[Unit]
Description=nfc daemon for auth
After=network.target
[Service]
User=root
Group=users
WorkingDirectory=/home/daisy/Documents/nfc
ExecStart=/home/daisy/Documents/nfc/venv/bin/python /home/daisy/Documents/nfc/nfc.py
# Not sure if should use 'on-failure' or 'always'.
Restart=on-failure
[Install]
WantedBy=default.target
This simple configuration locks the computer when it goes to sleep, replace display with the name of your display (get this with “echo $DISPLAY”)
/etc/systemd/system/wake_sleep.service
[Install]
WantedBy=sleep.target
[Unit]
After=systemd-suspend.service systemd-hybrid-sleep.service systemd-hibernate.service
[Service]
Type=forking
ExecStart=/bin/bash -c 'i3lock'
User=daisy
Environment=DISPLAY=:0.0
Make sure to enable and start both services
sudo systemctl enable nfc
sudo systemctl enable wake_sleep
sudo systemctl start nfc
sudo systemctl start wake_sleep
I also happened to need a cron job to start the service once logged in or in the event of a crash, but this should be possible with .profile too, so add a “sudo systemctl sttart nfc” in .profile and crontab if necessary.
Other than this, you will need to enable automatic login and disable the password prompt for login (we replaced it with I3lock, which can now be killed simply by plugging in an NFC dongle scanning an implant).
I hope this is useful to you. I wish you the best of luck in all your experiments and endeavours using these awesome MIFARE 1K/2K cards for authentication. Have a great day, and happy new year!
Update: I changed WantedBy= from multi-user.target to default.target in order to run the daemon on login instead of at boot, this should make sure everything works properly in an encrypted home directory (which I recommend)
(below) A photo of my setup, unlocking my computer like this.