Hello. I’m a bit new here. But been following and learning. I have since copied many key fobs. Now I tried my access key and the info is completely different out of nowhere. I didn’t change or write, only read. Did I completely ruin my access key? PLEASE HELP!! I’m using iceman with the pm3 easy
Depends on the commands that you’ve run on the work badge. What guide did you follow, and what commands did you run?
Also, make sure that you have good coupling between the badge and the Poxmark3.
Also did your client or firmware change? Are they mismatched?
do lf t55 detect before running any lf t55 commands that involve memory operations.
everything was from your instructions when i received the pm3 and put iceman on it. I made quite a few duplicates of these hid prox cards. all of a sudden, all of the duplicates stopped working 2 days ago for my building. and the duplicates i made for the same type for a sister building are working sometimes but mostly not. once they are verified with the pm3, everything was the same that i could tell. i must be missing something.
Yes, that brings up the help menu
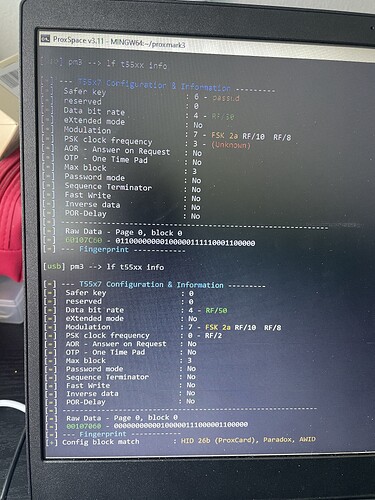
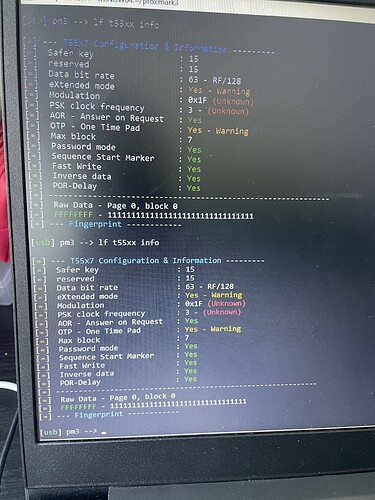
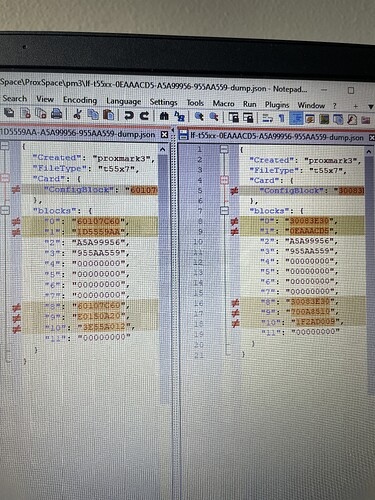
Now with lf t55 detect i get different block 0 values
With lf hid reader, everything is the same
So you tested the cards on an HID reader an you are getting reliable results with it? But the proxmark is hit or miss?
This is all only with the pm3 easy and using iceman. It’s all I have. But it seems like the cards I cloned, all from original, are slightly different now. Perhaps that’s why they are no longer working after a few weeks of no issues. Is it possible the reader is able to modify the keys after usage? Or maybe they just were temporary somehow?
This is what’s installed here.
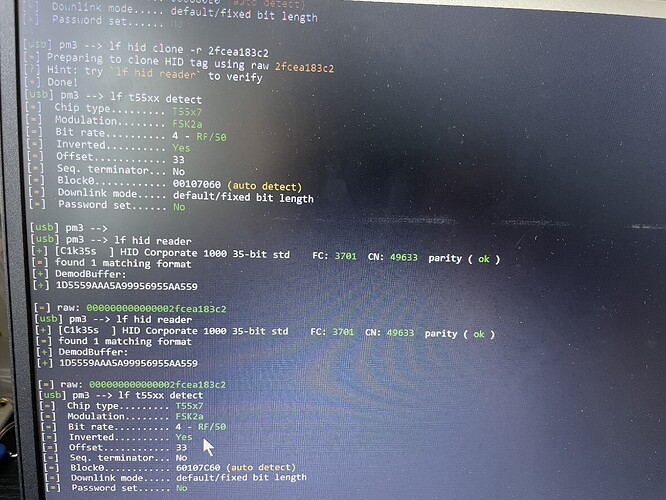
And this is what seems to be mismatched after cloning the original card every time. The offset is 33-34 but usually 34 on the original fob. And the block0 for the original is always 60107C60 and it’s 00107060 for the clones. That is the only inconsistency I can see.
Is there a way to edit the clone or customize the writing?
I need a little more clarification. Is the original fob using a t5577 chip? Do an LF search and then lf t5 detect
If your original fob is using a t5577 then do not use the hid stuff. Simply dump the t5577 memory from the original fob and restore it to your target t5577 chip. Doing it this way is like… oh God I’m about to date myself… doing it this way is like ripping the digital music file off of a CD, while doing it using hid commands is similar to recording the audio as it comes out of the sound card.
Woah ![]() . I will try this. Just need some time. Thank you
. I will try this. Just need some time. Thank you
Man. I appreciate that explanation. I totally get it. I was able to perform the dump and restore with minimal issues. But nothing seems to work. When everything is done and exactly the same, I’m still left with an offset of 33 on the duplicates. Where as the original is 34. And some restores turned up completely different. With all that said, nothing still works but the original.
Am I supposed to be restoring from the .bin file or the .json file?
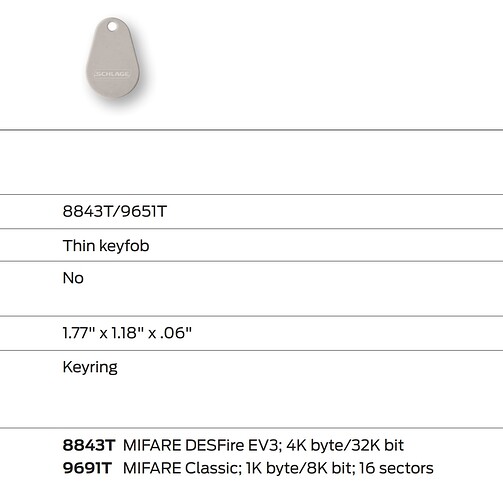
The system for the building is using Schlage 8843T fobs which seem to be hard to get unless you’re a security company. Is anyone familiar with these fobs? They seem newer than most.
I was wiping the new cards then lf search.
That turned up T55xx.
Then lf t55xx detect
Then lf t55xx restore -f <“file”>
I am really confused because I had plenty of fobs working for weeks flawlessly then poof. Dunsky. Is it possible that the system is hip to this? Or is there some sort of security that’s not apparent on the card itself?
You can pretty much use them interchangeably
Those might be HF fobs.
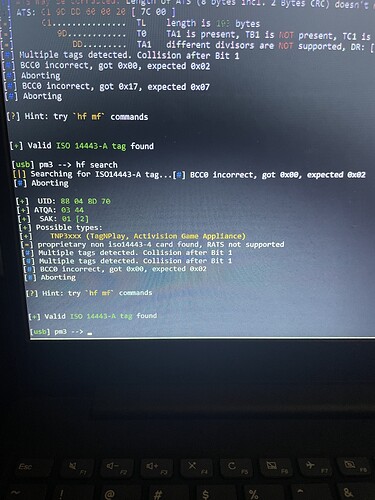
Can you scan one of the fobs with taginfo or run an hf search command with the Proxmark?
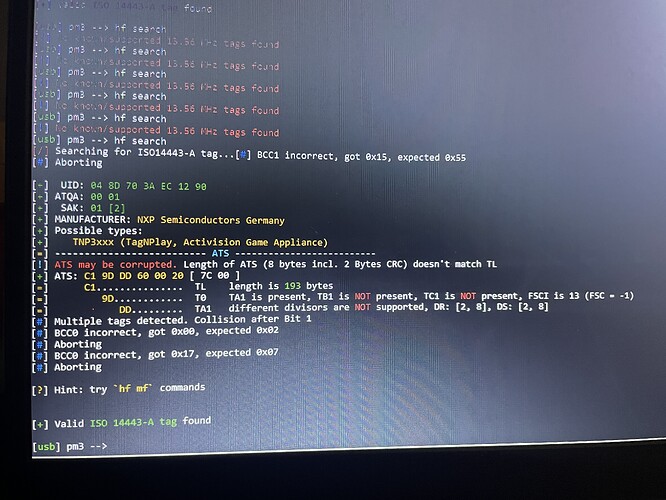
The 8843T has nothing from hf searching. That was one of the first things I tried when I received the pm3. Strange because it’s clearly a dual card in every description I have seen online. The other cards are all 125khz t5577 chips and all return nothing with hf search and placed on the hf antenna. I do have hf cards but those are set aside.
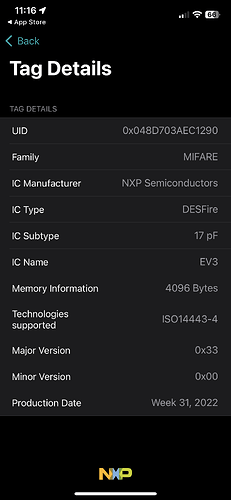
With the tag info app on iOS I get this from the Schlage fob
Ok… are you continuing to use the og fob? Do this …
Do a dump of the og fob.
Use the fob a few days.
Dump it again and compare.
Are the dumps different?
I see what you’re saying. I think they may have switched from the lf to hf for the readers. Or possibly a combination of them. Everything I cloned was just the lf. I couldn’t get the pm3 to recognize a hf chip on the original until I found an exact placement on the pm3. I got a partial reading. Then repositioned slightly and was able to get more info with the hf. Should I still focus on the lf with waiting and seeing if there are any changes? I attempted to dump the hf but it is far more in depth and complicated than I care to dive into without more research. And it seems like the hf in these is also near impossible to duplicate.