Table breakdown of IC name vs what it means & memory size:
| IC Name | Human Readable Name | Memory Size |
|---|---|---|
| MF1ICS50 | Weak/Old MFC | 1 Kilobytes |
| MF1ICS70 | Weak/Old MFC | 4 Kilobytes |
| MF1S50 | ‘hardened’/New/EV1 MFC | 1 Kilobytes |
| MF1S70 | ‘hardened’/New/EV1 MFC | 4 Kilobytes |
A brief history of Mifare Classic
For many years the original Mifare ‘MF1ICS50’ chip was used for all kinds of applications as a “secure chip” for everything from access control to stored value cards and used for making localized payments within closed systems like public transit and laundry services. However, it uses a security mechanism called “crypto1” (aka Crapto1) which is a simple, proprietary encryption mechanism that hardly has anything to do with modern cryptography. It has been broken for many years now, but due to its unprecedented popularity, there are still hundreds of thousands of systems out there that still make use of it. Meaning that the Mifare Classic will continue to be used by legacy systems around the world for years to come.
However, the ability to break crypto1 and get at the normally protected data does not necessarily help you if you want to copy that data to another Mifare card, fob, or tag. That’s because real Mifare chips do not allow you to change the data in block 0 (B0), which is where special manufacturing information is held as well as the 4-byte non-unique ID (NUID) or serial number of the chip. You could copy all the data from the user sectors to a new card, but basically any machine reading the cloned card will know that the serial number doesn’t match or is not registered with the system thus will likely ignore the card or even alert security to a possible attempt at something malicious/a counterfeit card is present.
NXP were made aware of the fatal flaw originally uncovered by Karsten Nohl and Henryk Plötz from Radboud University, Nijmegen and released a security statement acknowledging their research. In said statement, it was recommended that MFC should not be used in a security conscientious system. In hopes to rectify the issues with the previous design and implementation of the MFC ICs, NXP discontinued the MF1IC line of chips and instead replaced them with the MF1S line. The newer chips integrated a better (but still flawed) Pseudorandom Number Generator (PRNG) in hopes to revive the Mifare Classic family of cards but failed thanks to the research of Carlo Meijer & Roel Verdult both from Radboud University . In addition to the ‘hardened’ PRNG, NXP made it possible for 7 byte UIDs on the cards but still kept support for the 4 byte (N)UID.
Magic Mifare Chips
A magic Mifare chip is a special grey-market chip made in China that can emulate the memory structure and functionality of real Mifare chips, but also have additional features on top of this. Most magic chips will allow the data within block 0 (b0) to be overwritten just like any other user block. The significant advantage this allows is the ability to change the UID and manufacturer data on the card thus cloning pertinent information from a genuine MFC card.
Gen1a vs Gen2 | Advantages vs Disadvatages
To put simply, gen1a chips are safer because you can always recover mistakes but require special hardware or software to change block 0 (where the UID is located) or recover from locked sectors. On the other hand, gen2 chips allow you the ability to use an NFC smartphone to write to block 0 using an app, but if you accidentally lock a sector, you cannot recover it (just like a genuine Mifare Classic).
For more technical information on the differences, please read these notes by Doegox.
gen1a
The magic gen1a chips have a special command (aka backdoor commands) set that bypasses the need for authentication on the card thus it can perform read/write operations without the need for the keys. It also has the ability to overwrite block 0 like most magic cards. The luxury allowed by this special command set is it that it can easily recover from badly configured cards which would not be possible with a genuine card and would be considered bricked on a genuine card.
However, this special command set comes at a cost of hardware that can issue these commands thus there is a barrier of entry to use these chips. Smartphones are not amongst the group that can issue these commands; a proxmark3 or ACR122U would be needed.
Some manufacturers have become privy to this knowledge and have developed countermeasures into their readers that aim to detect the use of gen1a chips. This generally works by issuing the card with a magic ‘wake up’ command, which if the card understands, the read will stop further communication as it has detected a gen1a chip. Some readers take this a step further and overwrite the chip’s contents in a bid to eradicate the clone all together. The monitoring software that comes with the readers (especially for enterprise implementations) will show a critical alert to the security staff that a counterfeit card has been detected and at what reader. These countermeasures are still quite rare to find in the wild but are growing in popularity especially in Asia.
gen2
The gen2 chips have one additional feature over a genuine card and that is the ability to overwrite block 0. The downside to this is that there is no way to recover from a badly configured card (like writing bad access bits to a sector) so some caution should be used when writing. These chips do not come with a special command set which have the advantage of being able to be used with a smartphone. Given that there is no special command set, readers have no real way to detect if gen2 is being presented to a reader or if the card is genuine.
Since these cards are similar to their genuine counterparts, a bricked chip is not unheard of and a gen2 will have no sympathy. The common modus operandi is to do all of the testing and development on a gen1a card, try it on a reader and if it works continue to use it. If a genuine card has been exactly cloned to a gen1a but a reader is not accepting the card, most likely detecting it using a backdoor command itself, then use a gen2 as the reader cannot detect it.
Changing the UID of a magic Mifare chip
Writing to block 0 of a magic chip in order to change its UID depends on which version you have.
gen1a
As mentioned above, special hardware is needed to change the UID of a gen1a chip.
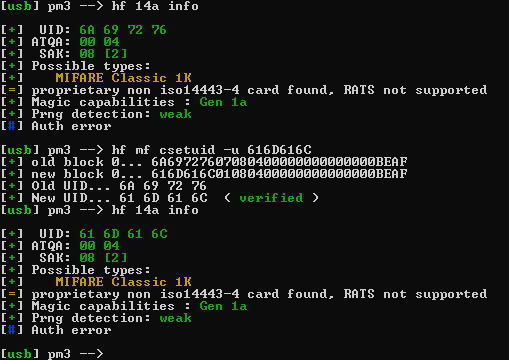
This can be done very simply on a proxmark3 using the RRG repo. The command to achieve this on a proxmark is hf mf csetuid. In order to change the UID to something user specified the parameter -u is needed followed by the UID. In full this should take the resemblance of: hf mf csetuid -u 01020304. Where 01020304 is the new UID that is going to be set for the card.
gen2
You can write to sector 0 of a magic gen2 chip like any other sector on a Mifare classic chips. That means you can even use an NFC smartphone and an app to do it.
Out of the box, a gen 2 card should be using default keys which is simply 12 'F’s. Using a proxmark this can be leveraged easily with the command hf mf wrbl, supplying it with the key and the whole new block 0 to write (not just the UID).
WIP
Cloning card data to a magic chip
Before embarking on the process to clone a genuine card, some prerequisite knowledge about the source/genuine card is vital.
- What keys are being used?
- What type of PRNG is being used (weak/hard/static)?
- What memory size is it (1k or 4k)?
Depending on the answers to the above questions will alter the process of gaining the data from the source card before it can be copied/cloned to a magic card.
gen1a
By far the most powerful tool to use is the Proxmark3 - an RFID diagnostics and security research tool that is open source, so it comes in many flavours, shapes, and sizes. It’s flexibility and ability to update the firmware to support the latest security tactics and tools means it’s a great investment for anyone wanting to experiment with RFID. While we do not offer a guide for how to use the Proxmark3 to clone Mifare cards to a “magic” chip, there are plenty of other guides already written that detail how it’s done.
If you dont have a proxmark then an ACR122U can be used however the proxmark is the more common and better documented tool overall.
gen2
If you have a gen2 chip and want to clone some data to it, you can use an Android smartphone app called MCT.
WIP
Footnote
This is to serve as an addition to Amal’s originally created post on this topic. I have taken said post as a base, reworded some parts and added my own information.
Many thanks to Amal for the original post and inspiration.