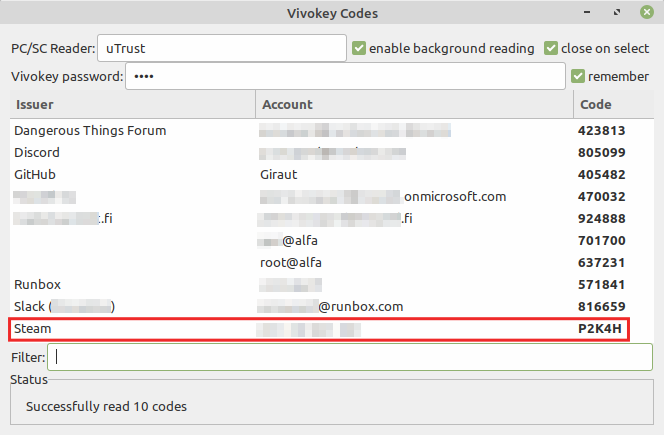
Nope. In this case, Steam codes are better: they have 5 alphanumerical characters picked from a 26-character set, meaning each code is 1 possibility out of 265 = 11,881,376. Ordinary TOTP codes of similar compacity have 6 digits, meaning each code is 1 possibility out of only 106 = 1,000,000.
Of course, normal TOTP can be up to 10 digits long (1 out of 10bn) and would be safer, but they’re nowhere as compact. Even 6-digit TOTP codes are longer than 5-character Steam codes.
I lifted it from the Yubikey Authenticator  It’s had that capability for years, and so have the Vivokey OTP applet and Vivokey Authenticator, since they’re straight forks of the Yubico stuff.
It’s had that capability for years, and so have the Vivokey OTP applet and Vivokey Authenticator, since they’re straight forks of the Yubico stuff.
I was rummaging inside the code earlier today to find a way to get the OTP applet to calculate longer codes, to use it to generate encryption keys I could use with cryptsetup to encrypt partitions (it can by the way, that’s my next project) and I stumbled upon those “Steam code” things that are calculated differently than ordinary codes.
2 minutes of Googling revealed what they were (I don’t have a Steam account so I didn’t know they existed), 2 more minutes revealed that other TOTP authenticators already support them, and another minute to create a fake Steam account on my Apex showed me that the Vivokey Authenticator and vkman do indeed spew out Steam codes out of the box.
I figured it would be a desirable functionality for Apex-wearing gamers, so I added it.
In short, the code is the documentation. Read the code Luke  Look in mine for an easier “tutorial” than Yubico’s code: it’s still code, but it’s nowhere near as convoluted as Yubico’s. The gist of it is, the regular code is calculated by converting the 31-bit truncated code returned by the token to a 6- to 10-digit base-10 decimal number, while the Steam code is calculated by converting it to a 5-digit base 26 number with the digits encoded with a special alphanumerical character set. The relevant lines in
Look in mine for an easier “tutorial” than Yubico’s code: it’s still code, but it’s nowhere near as convoluted as Yubico’s. The gist of it is, the regular code is calculated by converting the 31-bit truncated code returned by the token to a 6- to 10-digit base-10 decimal number, while the Steam code is calculated by converting it to a 5-digit base 26 number with the digits encoded with a special alphanumerical character set. The relevant lines in vivokey_codes.py are from line 1204 to 1214.
![]()