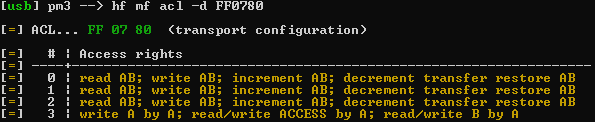
This would be expected behavior based on your access bits. I’ll deconstruct it a bit here for you. Based on documentation for the Mifare Classic 1k.
The full sector trailer for Sec0 is in Blk3 which is A0A1A2A3A4A5787788C10D258FE90296
Key A Access Bits Key B
A0A1A2A3A4A5 787788C1 0D258FE90296
We first convert this hex string to binary bits:
787788C1 = 01111000011101111000100011000001
To make it a little more human readable:
Sec0
C2i C1i
3210 3210
---- ----
0111 1000
C1 C3i
3210 3210
---- ----
0111 0111
C3 C2
3210 3210
---- ----
1000 1000
User Data
3210 3210
---- ----
1100 0001
(i at the end means inverse, i.e. C2 = 1000, so inverse would be 0111, which happens to be C2i)
According to the documentation this set of Access Bits means:
Blk0
Access bits = C1(0) C2(0) C3(0) = 100
Read by A|B
Write by B
So you can read Sector 0 with both keys, but only write to it with Key B, which is the behavior you see with you PM3. We can change these rules by changing the Access Bits, if they are able to be written themselves.
SecTrailer
Access bits = C1(3) C2(3) C3(3) = 001
Read/Write Access Bits by Key A.
Good! This means we can still change access bits with Key A.
We want Blk0 to be Read/Write by Key A|B, so C1(0) C2(0) C3(0) Needs to be 000 (unless you want it to be more restrictive.) 000 gives us full read/write/inc/dec/etc access by A|B.
So the new Access Bits would be:
Sec0
C2i C1i
3210 3210
---- ----
0111 1001
C1 C3i
3210 3210
---- ----
0110 0111
C3 C2
3210 3210
---- ----
1000 1000
User Data
3210 3210
---- ----
1100 0001
Which translates to 01111001011001111000100011000001 = 796788C1
So the command to write this would be:
hf mf wrbl 3 A A0A1A2A3A4A5 A0A1A2A3A4A5796788C10D258FE90296
I claim no responsibility if this bricks your device, as I have not tested this command on a card myself, but I believe it should work. Do your own due diligence and don’t trust everything everyone tells you on the internet. 
Also, be careful when playing around with Access Bits on a gen2 chip. If you set them in a way that there is no access to write the Access Bits for the block anymore, there is no backdoor to save you. The block will be stuck forever.
Hope this helps you understand! Let me know if you have more questions.