I recently got the xEM RFID and am having no luck with it. It is NOT implated and all tests have been done with it physically sitting on my ProxMark (iceman firmware). when I “lf search” it locates it and says it found an EM device with a chip type of t55xx. I try to wipe it - and no luck - it still appears to ProxMark and my Flipper Zero as an EM device. I tried to clone an ioProx to it and even though it says it did clone - I check it again and it still appears as an EM. I have tried cloning several different devices to it (EM, ioProx, HID, etc) - all with NO luck. At this point I question if this thing is even writable. Am I missing a step?
It’s not implanted? As in, still in the injector? I ask because the metal needle will prevent coupling.
It is not implanted nor is it in the injector - I took it out of that it set it on the coil of the ProxMark (at 90 degrees to the coil). I’ve moved it all around the coil and tried over 100 orientations with no luck. When I wipe and then re-read it still stays it is a EM device. I tried to clone an ioProx to it and get this:
[=] Preparing to clone ioProx to T55x7 with Version: 2 FC: 164 (0xad) CN: 53227
[+] Blk | Data
[+] ----±-----------
[+] 00 | 00147040
[+] 01 | 00786B60
[+] 02 | 5F6FDDBF
[+] Done
[?] Hint: try lf io reader to verify
then I do “lf io reader” and get nothing. I “if Search” again and it still says its a EM device. :-/
Interesting. I haven’t worked with ioProx before. Can you try emulating the tag with your Proxmark, read and save it with the Flipper then try writing it with that device? I find my Flipper couples nore readily with my NExT than my Proxmark.
Also, this thread talks about issues arriving cloning these tags.
It can emulate it. I read the original with my Flipper and tried to write to the xEM and it doesn’t work. I then used the saved image on the flipper to write to a t5577 card I have laying around - and that worked fine.
Have you tried writing a different EM4100 Id to it using your Flipper?
I read it using Flipper then went in “Edit” and changed the last byte from 3E to 3F - then tried to write back to it and it fails.
Hmmm, I haven’t seen one read but not write before. But you can walk through this. After you’re sure you’re nailing the orientation, checkout step 2.
Yeah - I went through that once before with no luck but I went ahead and tried it again. It detects it but writing the blocks fails and trying to clone an EM also fails. It’s seeming more and more like I just wasted $60…
On the DT homepage click on the “help” button and reply with your order # and a link to this thread and we’ll get you sorted.
Ok I received your ticket but let’s continue diagnostic here. Can you confirm the proxmark3 identifies the chipset as a T5577? When you do lf search what is the complete output?
Can I suggest you read through this step by step for an ioProx!?
Also, how are you planning on “cleaning” your xEM before you install?
Oh also try recovering…
I went through every step of that. Still no luck with it.
As far as “cleaning” it - the purpose of it was not to be implanted. I got this one for a “proof of concept” to see if it meets my needs.
[usb] pm3 → lf search
[=] Note: False Positives ARE possible
[=]
[=] Checking for known tags…
[=]
[+] EM 410x ID 01A8FB613E
[+] EM410x ( RF/64 )
[=] -------- Possible de-scramble patterns ---------
[+] Unique TAG ID : 8015DF867C
[=] HoneyWell IdentKey
[+] DEZ 8 : 16474430
[+] DEZ 10 : 2835046718
[+] DEZ 5.5 : 43259.24894
[+] DEZ 3.5A : 001.24894
[+] DEZ 3.5B : 168.24894
[+] DEZ 3.5C : 251.24894
[+] DEZ 14/IK2 : 00007130014014
[+] DEZ 15/IK3 : 000550122784380
[+] DEZ 20/ZK : 08000105131508060712
[=]
[+] Other : 24894_251_16474430
[+] Pattern Paxton : 34578238 [0x20F9F3E]
[+] Pattern 1 : 16686138 [0xFE9C3A]
[+] Pattern Sebury : 24894 123 8085822 [0x613E 0x7B 0x7B613E]
[+] VD / ID : 001 / 2835046718
[=] ------------------------------------------------
[+] Valid EM410x ID found!
[+] Chipset detection: T55xx
[?] Hint: try lf t55xx commands
[usb] pm3 → lf t55 detect
[=] Chip type… T55x7
[=] Modulation… ASK
[=] Bit rate… 5 - RF/64
[=] Inverted… No
[=] Offset… 33
[=] Seq. terminator… Yes
[=] Block0… 60148040 (auto detect)
[=] Downlink mode… default/fixed bit length
[=] Password set… No
Can you change the EM ID using
lf em 410x clone --id 0102030405
You might need to double check that command syntax… I’m mobile at the moment
You were bang on!
![]()
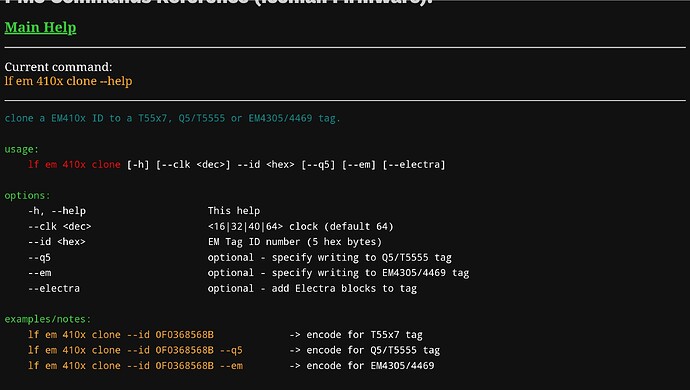
For others not as clever as Amal, and when you are away from your proxmark
https://siliconbased.us/pm3/ref/
SUCH a great fucken tool
lf em 410x clone --id 0F0368568B
This is the exact issue I have with my xEM that I bought and had implanted about 2 months ago. It has the same exact block 0 config too. The 6 makes it impossible to use in test mode
Can you see if you can write to block 3, 4, 5, and 6?
lf t5 write -b 3 -d 00110011 --verify
This is the same problem I am having with mine that I posted about last week. It has the same block 0 config which I never set:
[usb|script] pm3 --> lf t55 detect
[=] Chip type......... T55x7
[=] Modulation........ ASK
[=] Bit rate.......... 5 - RF/64
[=] Inverted.......... No
[=] Offset............ 33
[=] Seq. terminator... Yes
[=] Block0............ 60148040 (auto detect)
[=] Downlink mode..... default/fixed bit length
[=] Password set...... No
Can you check your stock and see if they have the same block 0, and if so if you can write to blocks 3 -6 but not block 0-2?