thanks for your input, there is no urgency and our time zones are opposites ( im in Adelaide Australia )
I will try with the " hf mf csetuid XX XX XX XX w" comand when im in front of my computer next.
Haha, not really opposite.
I’m in NZ ![]()
For some reason I thought you were in the UK it must’ve been your accent.
![]()
hmmm, im still having no luck. I dont know what im doing wrong, I know the hex for the "master " key. and following what I know but its not writing , ive tried various destination card types to no avail.
[usb] pm3 → hf search
![]() Searching for ISO14443-A tag…
Searching for ISO14443-A tag…
[+] UID: ## ## ## ## ## ## ##
[+] ATQA: 00 44
[+] SAK: 00 [2]
[+] MANUFACTURER: NXP Semiconductors Germany
[+] Possible types:
[+] MIFARE Ultralight
[+] MIFARE Ultralight C
[+] MIFARE Ultralight EV1
[+] MIFARE Ultralight Nano
[+] MIFARE Hospitality
[+] NTAG 2xx
[=] proprietary non iso14443-4 card found, RATS not supported
[?] Hint: try hf mfu info
[+] Valid ISO14443-A tag found
then
hf mf csetuid 04 92 7A EA A0 65 81 w
and I get this.
Set UID, ATQA, and SAK for magic Chinese card. Only works with magic cards
Usage: hf mf csetuid [h] <UID 8 hex symbols> [ATQA 4 hex symbols] [SAK 2 hex symbols] [w]
Options:
h this help
w wipe card before writing
UID 8 hex symbols
ATQA 4 hex symbols
SAK 2 hex symbols
Examples:
hf mf csetuid 01020304
hf mf csetuid 01020304 0004 08 w
[usb] pm3 →
I’ve also tried with out spaces.
[ usb ] pm3 → hf mf csetuid ############## w
STUMPED ! ? ![]()
Sorry, I obviously haven’t explained myself very well.
Try this and post results
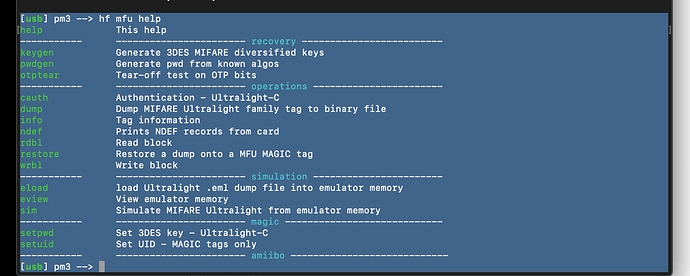
hf mfu info
and / or
hf mfu help
It’s not you , it’s me.
[usb] pm3 → hf mfu help
help This help
----------- ----------------------- recovery -------------------------
keygen Generate 3DES MIFARE diversified keys
pwdgen Generate pwd from known algos
otptear Tear-off test on OTP bits
----------- ----------------------- operations -----------------------
cauth Authentication - Ultralight-C
dump Dump MIFARE Ultralight family tag to binary file
info Tag information
ndef Prints NDEF records from card
rdbl Read block
restore Restore a dump onto a MFU MAGIC tag
wrbl Write block
----------- ----------------------- simulation -----------------------
eload load Ultralight .eml dump file into emulator memory
eview View emulator memory
sim Simulate MIFARE Ultralight from emulator memory
----------- ----------------------- magic ----------------------------
setpwd Set 3DES key - Ultralight-C
setuid Set UID - MAGIC tags only
----------- ----------------------- amiibo ----------------------------
[usb] pm3 →
The PM3 is a powerful and capable tool, it is just not particularly user-friendly…
Anybody else playing along at home and see any errors or have any suggestions, please jump in and contribute.
I would feel more comfortable doing this on something that I own than somebody elses.
I don’t have an ultralight to test this on, so please only try this on a test card and not on an implant until you are sure it works.
What I am thinking you will need to do is this:-
Test that you can write a new UID to your TEST CARD
TEST CARD
hf mfu setuid 04 92 7A EA A0 65 81 w
Followed by a quick
hf search
to see if it has taken the new UID
ORIGINAL
hf mfu dump
TEST CARD
hf mfu restore
Then test your “Test Card” on the system.
Let us know if it works.
yeah. Def not doing this on an implant. the reason I’m event bothering with this Proxmark crap is so I can get my head around the visibility of copying hid externally with, BEFORE I embark on an implant. if I can not successfully clone a card ill give it all up as a bad joke.
I’ve still unsure of what I need to do, when I run HF MFU DUMP ( on the " master card " ) I get this.
[usb] pm3 → hf mfu dump
[+] TYPE: NTAG 213 144bytes (NT2H1311G0DU)
[+] Reading tag memory…
[!] ![]() Authentication Failed UL-EV1/NTAG
Authentication Failed UL-EV1/NTAG
[=] MFU dump file information
[=] -------------------------------------------------------------
[=] Version | 00 04 04 02 01 00 0F 03
[=] TBD 0 | 00 00
[=] TBD 1 | 00
[=] Signature | DF C1 1F 11 A3 C1 B2 34 97 F8 41 D9 4E 71 C6 6F A7 D1 86 31 17 3B 9D F9 09 4F 20 8D 1E 37 A7 FC
[=] Counter 0 | 00 00 00
[=] Tearing 0 | 00
[=] Counter 1 | 00 00 00
[=] Tearing 1 | 00
[=] Counter 2 | 00 00 00
[=] Tearing 2 | BD
[=] Max data page | 43 (176 bytes)
[=] Header size | 56
[=] -------------------------------------------------------------
[=] block# | data |lck| ascii
[=] ---------±------------±–±-----
[=] 0/0x00 | 04 81 7C 71 | | …|q
[=] 1/0x01 | EA A0 65 81 | | …e.
[=] 2/0x02 | AE 48 00 00 | | .H…
[=] 3/0x03 | E1 10 12 00 | 0 | …
[=] 4/0x04 | 0D 72 2D 99 | 0 | .r-.
[=] 5/0x05 | AB 69 B9 C0 | 0 | .i…
[=] 6/0x06 | AC 13 3D 54 | 0 | …=T
[=] 7/0x07 | BA 8A DF 3E | 0 | …>
[=] 8/0x08 | 8A 00 00 00 | 0 | …
[=] 9/0x09 | 00 00 00 00 | 0 | …
[=] 10/0x0A | 00 00 00 00 | 0 | …
[=] 11/0x0B | 00 00 00 00 | 0 | …
[=] 12/0x0C | 00 00 00 00 | 0 | …
[=] 13/0x0D | 00 00 00 00 | 0 | …
[=] 14/0x0E | 00 00 00 00 | 0 | …
[=] 15/0x0F | 00 00 00 00 | 0 | …
[=] 16/0x10 | 00 00 00 00 | 0 | …
[=] 17/0x11 | 00 00 00 00 | 0 | …
[=] 18/0x12 | 00 00 00 00 | 0 | …
[=] 19/0x13 | 00 00 00 00 | 0 | …
[=] 20/0x14 | 00 00 00 00 | 0 | …
[=] 21/0x15 | 00 00 00 00 | 0 | …
[=] 22/0x16 | 00 00 00 00 | 0 | …
[=] 23/0x17 | 00 00 00 00 | 0 | …
[=] 24/0x18 | 00 00 00 00 | 0 | …
[=] 25/0x19 | 00 00 00 00 | 0 | …
[=] 26/0x1A | 00 00 00 00 | 0 | …
[=] 27/0x1B | 00 00 00 00 | 0 | …
[=] 28/0x1C | 00 00 00 00 | 0 | …
[=] 29/0x1D | 00 00 00 00 | 0 | …
[=] 30/0x1E | 00 00 00 00 | 0 | …
[=] 31/0x1F | 00 00 00 00 | 0 | …
[=] 32/0x20 | 00 00 00 00 | 0 | …
[=] 33/0x21 | 00 00 00 00 | 0 | …
[=] 34/0x22 | 00 00 00 00 | 0 | …
[=] 35/0x23 | 00 00 00 00 | 0 | …
[=] 36/0x24 | 00 00 00 00 | 0 | …
[=] 37/0x25 | 00 00 00 00 | 0 | …
[=] 38/0x26 | 00 00 00 00 | 0 | …
[=] 39/0x27 | 00 00 00 00 | 0 | …
[=] 40/0x28 | 00 00 00 BD | 0 | …
[=] 41/0x29 | 04 00 00 FF | 0 | …
[=] 42/0x2A | 00 05 00 00 | 0 | …
[=] 43/0x2B | 00 00 00 00 | 0 | …
[=] 44/0x2C | 00 00 00 00 | 0 | …
[=] ---------------------------------
[=] Using UID as filename
[+] saved 236 bytes to binary file hf-mfu-04817CEAA06581-dump-2.bin
[+] saved to json file hf-mfu-04817CEAA06581-dump-2.json
[usb] pm3 →
and then with hf mfu restore. I get this –
[usb] pm3 → hf mfu restore
Restore dumpfile onto card.
usage:
hf mfu restore [-hlserv] -f [-k ]
options:
-h, --help This help
-f, --file specify a filename to restore
-k, --key key for authentication (UL-C 16 bytes, EV1/NTAG 4 bytes)
-l swap entered key’s endianness
-s enable special write UID -MAGIC TAG ONLY-
-e enable special write version/signature -MAGIC NTAG 21* ONLY-
-r use the password found in dumpfile to configure tag. requires ‘-e’ parameter to work
-v, --verbose verbose
examples/notes:
hf mfu restore -f myfile -s → user specified filename and special write
hf mfu restore -f myfile -k AABBCCDD -s → user specified filename, special write and use key
hf mfu restore -f myfile -k AABBCCDD -ser → user specified filename, special write, use key, …
[usb] pm3 → hf mfu restore -r
[!] hf mfu restore: missing option -f|–file
[!] ![]() Try ‘hf mfu restore --help’ for more information.
Try ‘hf mfu restore --help’ for more information.
![]()
Can you do a scan of your “test card” you are trying to write to?
this __
[usb] pm3 → hf search
![]() Searching for ISO14443-A tag…
Searching for ISO14443-A tag…
[+] UID: FA 9D DD 1D
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] proprietary non iso14443-4 card found, RATS not supported
[+] Prng detection: weak
[#] Auth error
[?] Hint: try hf mf commands
[+] Valid ISO14443-A tag found
[usb] pm3 →
Hmmm, that’s what I suspected.
You have a Mifare Ultralight and you are trying to write to a Mifare Classic.
Unfortunately, that is not going to work.
So you have two options.
The Magic chips are more expensive compared to most cards
To do what you want, you would need one or both.
CARD
To write to a test card you will need a Magic NTAG card
IMPLANT
The implant equivalent is the FlexMN
ohh. cool. so cant cross populate. im happy that im learning all this now.
i have other cards / tags / fobs, ive now identified what cards/ fobs/ tags are what. so when I “hf search”. on an nfc tag. i get
[usb] pm3 → hf search
![]() Searching for ISO14443-A tag…
Searching for ISO14443-A tag…
[+] UID: 04 E5 D6 EA F4 6B 80
[+] ATQA: 00 44
[+] SAK: 00 [2]
[+] MANUFACTURER: NXP Semiconductors Germany
[+] Possible types:
[+] MIFARE Ultralight
[+] MIFARE Ultralight C
[+] MIFARE Ultralight EV1
[+] MIFARE Ultralight Nano
[+] MIFARE Hospitality
[+] NTAG 2xx
[=] proprietary non iso14443-4 card found, RATS not supported
[?] Hint: try hf mfu info
[+] Valid ISO14443-A tag found
[usb] pm3 →
my master card/ ( working nfc ring ) is ultralight. and the NFC Tag is also a Ultralight.
so " simply" running the folowing comands would work. unless there there is another variable im about to learn,
hf mfu dump
then
hf mfu restore
- then this should work right ? ??
Not quite… You probably want to dump it to a file and then restore it from that file.
hf mfu restore requires a file parameter.
So
hf mfu dump -f afilename
hf mfu restore -f afilename
Should be what you want.
BTW, I am British (but living in the US). ![]()
Thanks zwak.
I’m so close. I can almost smell it.
Standby while in run this a
there is a Sting song about you. - https://www.youtube.com/watch?v=d27gTrPPAyk
I’m still not having any luck. ( im such a nube )
here is what im getting .
here is HF search of master key ( working NFC ring from dangerous things.
[usb] pm3 → hf search
![]() Searching for ISO14443-A tag…
Searching for ISO14443-A tag…
[+] UID: 04 D7 E4 FA AC 65 80
[+] ATQA: 00 44
[+] SAK: 00 [2]
[+] MANUFACTURER: NXP Semiconductors Germany
[+] Possible types:
[+] MIFARE Ultralight
[+] MIFARE Ultralight C
[+] MIFARE Ultralight EV1
[+] MIFARE Ultralight Nano
[+] MIFARE Hospitality
[+] NTAG 2xx
[=] proprietary non iso14443-4 card found, RATS not supported
[?] Hint: try hf mfu info
[+] Valid ISO14443-A tag found
[usb] pm3 →
Here is the Destination ( nfc tag )
- [usb] pm3 → hf search
 Searching for ISO14443-A tag…
Searching for ISO14443-A tag…
[+] UID: 04 E5 D6 EA F4 6B 80
[+] ATQA: 00 44
[+] SAK: 00 [2]
[+] MANUFACTURER: NXP Semiconductors Germany
[+] Possible types:
[+] MIFARE Ultralight
[+] MIFARE Ultralight C
[+] MIFARE Ultralight EV1
[+] MIFARE Ultralight Nano
[+] MIFARE Hospitality
[+] NTAG 2xx
[=] proprietary non iso14443-4 card found, RATS not supported
[?] Hint: tryhf mfu info
[+] Valid ISO14443-A tag found
[usb] pm3 →
now ill Dump from master. ( 2nd attempt )
[ usb ] pm3 → hf mfu dump -f doorring
[+] TYPE: NTAG 216 888bytes (NT2H1611G0DU)
[+] Reading tag memory…
[!] ![]() Authentication Failed UL-EV1/NTAG
Authentication Failed UL-EV1/NTAG
[=] MFU dump file information
[=] -------------------------------------------------------------
[=] Version | 00 04 04 02 01 00 13 03
[=] TBD 0 | 00 00
[=] TBD 1 | 00
[=] Signature | 1F B9 5B A9 77 D8 73 F5 64 DE 19 64 46 2A 4A 92 D2 57 7C C0 9A 6E 25 1B 98 C0 EF E1 01 AE 01 11
[=] Counter 0 | 00 00 00
[=] Tearing 0 | 00
[=] Counter 1 | 00 00 00
[=] Tearing 1 | 00
[=] Counter 2 | 00 00 00
[=] Tearing 2 | BD
[=] Max data page | 229 (920 bytes)
[=] Header size | 56
[=] -------------------------------------------------------------
[=] block# | data |lck| ascii
[=] ---------±------------±–±-----
[=] 0/0x00 | 04 D7 E4 BF | | …
[=] 1/0x01 | FA AC 65 80 | | …e.
[=] 2/0x02 | B3 48 0F 00 | | .H…
[=] 3/0x03 | E1 10 6D 00 | 1 | …m.
[=] 4/0x04 | 0D 72 54 99 | 0 | .rT.
[=] 5/0x05 | AB 69 B9 C0 | 0 | .i…
[=] 6/0x06 | AC FF 13 54 | 0 | …T
[=] 7/0x07 | BA 8A DF 3E | 0 | …>
[=] 8/0x08 | 8A 00 00 00 | 0 | …
[=] 9/0x09 | 42 45 47 49 | 0 | BEGI
[=] 10/0x0A | 4E 3A 56 43 | 0 | N:VC
[=] 11/0x0B | 41 52 44 0D | 0 | ARD.
[=] 12/0x0C | 0A 56 45 52 | 0 | .VER
[=] 13/0x0D | 53 49 4F 4E | 0 | SION
[=] 14/0x0E | 3A 33 2E 30 | 0 | :3.0
[=] 15/0x0F | 0D 0A 50 52 | 0 | …PR
[=] 16/0x10 | 4F 44 49 44 | 0 | ODID
[=] 17/0x11 | 3A 2D 2F 2F | 0 | :-//
[=] 18/0x12 | 41 70 70 6C | 0 | Appl
[=] 19/0x13 | 65 20 49 6E | 0 | e In
[=] 20/0x14 | 63 2E 2F 2F | 0 | c.//
[=] 21/0x15 | 69 50 68 6F | 0 | iPho
[=] 22/0x16 | 6E 65 20 4F | 0 | ne O
[=] 23/0x17 | 53 20 31 34 | 0 | S 14
[=] 24/0x18 | 2E 34 2F 2F | 0 | .4//
[=] 25/0x19 | 45 4E 0D 0A | 0 | EN…
[=] 26/0x1A | 4E 3A 42 61 | 0 | N:Ba
[=] 27/0x1B | 72 74 65 72 | 0 | rter
[=] 28/0x1C | 3B 50 65 74 | 0 | ;Pet
[=] 29/0x1D | 65 3B 3B 3B | 0 | e;;;
[=] 30/0x1E | 0D 0A 46 4E | 0 | …FN
[=] 31/0x1F | 3A 50 65 74 | 0 | :Pet
[=] 32/0x20 | 65 20 42 61 | 0 | e Ba
[=] 33/0x21 | 72 74 65 72 | 0 | rter
[=] 34/0x22 | 0D 0A 4E 49 | 0 | …NI
[=] 35/0x23 | 43 4B 4E 41 | 0 | CKNA
[=] 36/0x24 | 4D 45 3A 50 | 0 | ME:P
[=] 37/0x25 | 65 74 65 0D | 0 | ete.
[=] 38/0x26 | 0A 4F 52 47 | 0 | .ORG
[=] 39/0x27 | 3A 53 41 4D | 0 | :SAM
[=] 40/0x28 | 69 69 3B 0D | 0 | ii;.
[=] 41/0x29 | 0A 54 49 54 | 0 | .TIT
[=] 42/0x2A | 4C 45 3A 46 | 0 | LE:F
[=] 43/0x2B | 6F 75 6E 64 | 0 | ound
[=] 44/0x2C | 65 72 20 2F | 0 | er /
[=] 45/0x2D | 20 44 69 72 | 0 | Dir
[=] 46/0x2E | 65 63 74 6F | 0 | ecto
[=] 47/0x2F | 72 0D 0A 45 | 0 | r…E
[=] 48/0x30 | 4D 41 49 4C | 0 | MAIL
[=] 49/0x31 | 3B 74 79 70 | 0 | ;typ
[=] 50/0x32 | 65 3D 49 4E | 0 | e=IN
[=] 51/0x33 | 54 45 52 4E | 0 | TERN
[=] 52/0x34 | 45 54 3B 74 | 0 | ET;t
[=] 53/0x35 | 79 70 65 3D | 0 | ype=
[=] 54/0x36 | 57 4F 52 4B | 0 | WORK
[=] 55/0x37 | 3B 74 79 70 | 0 | ;typ
[=] 56/0x38 | 65 3D 70 72 | 0 | e=pr
[=] 57/0x39 | 65 66 3A 70 | 0 | ef:p
[=] 58/0x3A | 65 74 65 62 | 0 | eteb
[=] 59/0x3B | 61 72 74 65 | 0 | arte
[=] 60/0x3C | 72 65 74 69 | 0 | reti
[=] 61/0x3D | 40 67 6D 61 | 0 | @gma
[=] 62/0x3E | 69 6C 2E 63 | 0 | il.c
[=] 63/0x3F | 6F 6D 0D 0A | 0 | om…
[=] 64/0x40 | 54 45 4C 3B | 0 | TEL;
[=] 65/0x41 | 74 79 70 65 | 0 | type
[=] 66/0x42 | 3D 43 45 4C | 0 | =CEL
[=] 67/0x43 | 4C 3B 74 79 | 0 | L;ty
[=] 68/0x44 | 70 65 3D 56 | 0 | pe=V
[=] 69/0x45 | 4F 49 43 45 | 0 | OICE
[=] 70/0x46 | 3B 74 79 70 | 0 | ;typ
[=] 71/0x47 | 65 3D 70 72 | 0 | e=pr
[=] 72/0x48 | 65 66 3A 30 | 0 | ef:0
[=] 73/0x49 | 34 30 31 20 | 0 | 401
[=] 74/0x4A | 34 37 36 20 | 0 | 476
[=] 75/0x4B | 37 39 36 0D | 0 | 796.
[=] 76/0x4C | 0A 54 45 4C | 0 | .TEL
[=] 77/0x4D | 3B 74 79 70 | 0 | ;typ
[=] 78/0x4E | 65 3D 57 4F | 0 | e=WO
[=] 79/0x4F | 52 4B 3B 74 | 0 | RK;t
[=] 80/0x50 | 79 70 65 3D | 0 | ype=
[=] 81/0x51 | 56 4F 49 43 | 0 | VOIC
[=] 82/0x52 | 45 3A 31 33 | 0 | E:13
[=] 83/0x53 | 30 30 20 33 | 0 | 00 3
[=] 84/0x54 | 38 34 20 35 | 0 | 84 5
[=] 85/0x55 | 38 33 0D 0A | 0 | 83…
[=] 86/0x56 | 41 44 52 3B | 0 | ADR;
[=] 87/0x57 | 74 79 70 65 | 0 | type
[=] 88/0x58 | 3D 48 4F 4D | 0 | =HOM
[=] 89/0x59 | 45 3B 74 79 | 0 | E;ty
[=] 90/0x5A | 70 65 3D 70 | 0 | pe=p
[=] 91/0x5B | 72 65 66 3A | 0 | ref:
[=] 92/0x5C | 3B 3B 33 33 | 0 | ;;33
[=] 93/0x5D | 20 57 61 72 | 0 | War
[=] 94/0x5E | 77 69 63 6B | 0 | wick
[=] 95/0x5F | 20 61 76 5C | 0 | av\
[=] 96/0x60 | 6E 3B 57 61 | 0 | n;Wa
[=] 97/0x61 | 6C 6B 65 72 | 0 | lker
[=] 98/0x62 | 76 69 6C 6C | 0 | vill
[=] 99/0x63 | 3B 53 61 3B | 0 | ;Sa;
[=] 100/0x64 | 35 30 38 31 | 0 | 5081
[=] 101/0x65 | 3B 41 75 73 | 0 | ;Aus
[=] 102/0x66 | 74 72 61 6C | 0 | tral
[=] 103/0x67 | 69 61 0D 0A | 0 | ia…
[=] 104/0x68 | 69 74 65 6D | 0 | item
[=] 105/0x69 | 31 2E 55 52 | 0 | 1.UR
[=] 106/0x6A | 4C 3B 74 79 | 0 | L;ty
[=] 107/0x6B | 70 65 3D 70 | 0 | pe=p
[=] 108/0x6C | 72 65 66 3A | 0 | ref:
[=] 109/0x6D | 50 65 74 65 | 0 | Pete
[=] 110/0x6E | 62 61 72 74 | 0 | bart
[=] 111/0x6F | 65 72 2E 63 | 0 | er.c
[=] 112/0x70 | 6F 6D 0D 0A | 0 | om…
[=] 113/0x71 | 69 74 65 6D | 0 | item
[=] 114/0x72 | 31 2E 58 2D | 0 | 1.X-
[=] 115/0x73 | 41 42 4C 61 | 0 | ABLa
[=] 116/0x74 | 62 65 6C 3A | 0 | bel:
[=] 117/0x75 | 5F 24 21 3C | 0 | _$!<
[=] 118/0x76 | 48 6F 6D 65 | 0 | Home
[=] 119/0x77 | 50 61 67 65 | 0 | Page
[=] 120/0x78 | 3E 21 24 5F | 0 | >!$_
[=] 121/0x79 | 0D 0A 42 44 | 0 | …BD
[=] 122/0x7A | 41 59 3A 31 | 0 | AY:1
[=] 123/0x7B | 39 38 30 2D | 0 | 980-
[=] 124/0x7C | 30 39 2D 30 | 0 | 09-0
[=] 125/0x7D | 39 0D 0A 45 | 0 | 9…E
[=] 126/0x7E | 4E 44 3A 56 | 0 | ND:V
[=] 127/0x7F | 43 41 52 44 | 0 | CARD
[=] 128/0x80 | 0D 0A FE 00 | 0 | …
[=] 129/0x81 | 00 00 00 00 | 0 | …
[=] 130/0x82 | 00 00 00 00 | 0 | …
[=] 131/0x83 | 00 00 00 00 | 0 | …
[=] 132/0x84 | 00 00 00 00 | 0 | …
[=] 133/0x85 | 00 00 00 00 | 0 | …
[=] 134/0x86 | 00 00 00 00 | 0 | …
[=] 135/0x87 | 00 00 00 00 | 0 | …
[=] 136/0x88 | 00 00 00 00 | 0 | …
[=] 137/0x89 | 00 00 00 00 | 0 | …
[=] 138/0x8A | 00 00 00 00 | 0 | …
[=] 139/0x8B | 00 00 00 00 | 0 | …
[=] 140/0x8C | 00 00 00 00 | 0 | …
[=] 141/0x8D | 00 00 00 00 | 0 | …
[=] 142/0x8E | 00 00 00 00 | 0 | …
[=] 143/0x8F | 00 00 00 00 | 0 | …
[=] 144/0x90 | 00 00 00 00 | 0 | …
[=] 145/0x91 | 00 00 00 00 | 0 | …
[=] 146/0x92 | 00 00 00 00 | 0 | …
[=] 147/0x93 | 00 00 00 00 | 0 | …
[=] 148/0x94 | 00 00 00 00 | 0 | …
[=] 149/0x95 | 00 00 00 00 | 0 | …
[=] 150/0x96 | 00 00 00 00 | 0 | …
[=] 151/0x97 | 00 00 00 00 | 0 | …
[=] 152/0x98 | 00 00 00 00 | 0 | …
[=] 153/0x99 | 00 00 00 00 | 0 | …
[=] 154/0x9A | 00 00 00 00 | 0 | …
[=] 155/0x9B | 00 00 00 00 | 0 | …
[=] 156/0x9C | 00 00 00 00 | 0 | …
[=] 157/0x9D | 00 00 00 00 | 0 | …
[=] 158/0x9E | 00 00 00 00 | 0 | …
[=] 159/0x9F | 00 00 00 00 | 0 | …
[=] 160/0xA0 | 00 00 00 00 | 0 | …
[=] 161/0xA1 | 00 00 00 00 | 0 | …
[=] 162/0xA2 | 00 00 00 00 | 0 | …
[=] 163/0xA3 | 00 00 00 00 | 0 | …
[=] 164/0xA4 | 00 00 00 00 | 0 | …
[=] 165/0xA5 | 00 00 00 00 | 0 | …
[=] 166/0xA6 | 00 00 00 00 | 0 | …
[=] 167/0xA7 | 00 00 00 00 | 0 | …
[=] 168/0xA8 | 00 00 00 00 | 0 | …
[=] 169/0xA9 | 00 00 00 00 | 0 | …
[=] 170/0xAA | 00 00 00 00 | 0 | …
[=] 171/0xAB | 00 00 00 00 | 0 | …
[=] 172/0xAC | 00 00 00 00 | 0 | …
[=] 173/0xAD | 00 00 00 00 | 0 | …
[=] 174/0xAE | 00 00 00 00 | 0 | …
[=] 175/0xAF | 00 00 00 00 | 0 | …
[=] 176/0xB0 | 00 00 00 00 | 0 | …
[=] 177/0xB1 | 00 00 00 00 | 0 | …
[=] 178/0xB2 | 00 00 00 00 | 0 | …
[=] 179/0xB3 | 00 00 00 00 | 0 | …
[=] 180/0xB4 | 00 00 00 00 | 0 | …
[=] 181/0xB5 | 00 00 00 00 | 0 | …
[=] 182/0xB6 | 00 00 00 00 | 0 | …
[=] 183/0xB7 | 00 00 00 00 | 0 | …
[=] 184/0xB8 | 00 00 00 00 | 0 | …
[=] 185/0xB9 | 00 00 00 00 | 0 | …
[=] 186/0xBA | 00 00 00 00 | 0 | …
[=] 187/0xBB | 00 00 00 00 | 0 | …
[=] 188/0xBC | 00 00 00 00 | 0 | …
[=] 189/0xBD | 00 00 00 00 | 0 | …
[=] 190/0xBE | 00 00 00 00 | 0 | …
[=] 191/0xBF | 00 00 00 00 | 0 | …
[=] 192/0xC0 | 00 00 00 00 | 0 | …
[=] 193/0xC1 | 00 00 00 00 | 0 | …
[=] 194/0xC2 | 00 00 00 00 | 0 | …
[=] 195/0xC3 | 00 00 00 00 | 0 | …
[=] 196/0xC4 | 00 00 00 00 | 0 | …
[=] 197/0xC5 | 00 00 00 00 | 0 | …
[=] 198/0xC6 | 00 00 00 00 | 0 | …
[=] 199/0xC7 | 00 00 00 00 | 0 | …
[=] 200/0xC8 | 00 00 00 00 | 0 | …
[=] 201/0xC9 | 00 00 00 00 | 0 | …
[=] 202/0xCA | 00 00 00 00 | 0 | …
[=] 203/0xCB | 00 00 00 00 | 0 | …
[=] 204/0xCC | 00 00 00 00 | 0 | …
[=] 205/0xCD | 00 00 00 00 | 0 | …
[=] 206/0xCE | 00 00 00 00 | 0 | …
[=] 207/0xCF | 00 00 00 00 | 0 | …
[=] 208/0xD0 | 00 00 00 00 | 0 | …
[=] 209/0xD1 | 00 00 00 00 | 0 | …
[=] 210/0xD2 | 00 00 00 00 | 0 | …
[=] 211/0xD3 | 00 00 00 00 | 0 | …
[=] 212/0xD4 | 00 00 00 00 | 0 | …
[=] 213/0xD5 | 00 00 00 00 | 0 | …
[=] 214/0xD6 | 00 00 00 00 | 0 | …
[=] 215/0xD7 | 00 00 00 00 | 0 | …
[=] 216/0xD8 | 00 00 00 00 | 0 | …
[=] 217/0xD9 | 00 00 00 00 | 0 | …
[=] 218/0xDA | 00 00 00 00 | 0 | …
[=] 219/0xDB | 00 00 00 00 | 0 | …
[=] 220/0xDC | 00 00 00 00 | 0 | …
[=] 221/0xDD | 00 00 00 00 | 0 | …
[=] 222/0xDE | 00 00 00 00 | 0 | …
[=] 223/0xDF | 00 00 00 00 | 0 | …
[=] 224/0xE0 | 00 00 00 00 | 0 | …
[=] 225/0xE1 | 4E 45 78 54 | 0 | NExT
[=] 226/0xE2 | 00 00 7F BD | 0 | …
[=] 227/0xE3 | 04 00 00 E3 | 0 | …
[=] 228/0xE4 | 00 05 00 00 | 0 | …
[=] 229/0xE5 | 00 00 00 00 | 0 | …
[=] 230/0xE6 | 00 00 00 00 | 0 | …
[=] ---------------------------------
[+] saved 980 bytes to binary file doorring-2.bin
[+] saved to json file doorring-2.json
[ usb ] pm3 →
now I’ll run the Restore to Tag.
[ usb ] pm3 → hf mfu restore -f doorring-2.json
[+] loaded 5619 bytes from binary file doorring-2.json
[-] ![]() Failed convert on load to new Ultralight/NTAG format
Failed convert on load to new Ultralight/NTAG format
[ usb ] pm3 →
now with the .bin file.
–
[ usb ] pm3 → hf mfu restore -f doorring-2.bin
[+] loaded 980 bytes from binary file doorring-2.bin
[=] Restoring doorring-2.bin to card
[=] MFU dump file information
[=] -------------------------------------------------------------
[=] Version | 00 04 04 02 01 00 13 03
[=] TBD 0 | 00 00
[=] TBD 1 | 00
[=] Signature | 1F B9 5B A9 77 D8 73 F5 64 DE 19 64 46 2A 4A 92 D2 57 7C C0 9A 6E 25 1B 98 C0 EF E1 01 AE 01 11
[=] Counter 0 | 00 00 00
[=] Tearing 0 | 00
[=] Counter 1 | 00 00 00
[=] Tearing 1 | 00
[=] Counter 2 | 00 00 00
[=] Tearing 2 | BD
[=] Max data page | 229 (920 bytes)
[=] Header size | 56
[=] -------------------------------------------------------------
[=] block# | data |lck| ascii
[=] ---------±------------±–±-----
[=] 0/0x00 | 04 D7 E4 BF | | …
[=] 1/0x01 | FA AC 65 80 | | …e.
[=] 2/0x02 | B3 48 0F 00 | | .H…
[=] 3/0x03 | E1 10 6D 00 | 1 | …m.
[=] 4/0x04 | 0D 72 54 99 | 0 | .rT.
[=] 5/0x05 | AB 69 B9 C0 | 0 | .i…
[=] 6/0x06 | AC FF 13 54 | 0 | …T
[=] 7/0x07 | BA 8A DF 3E | 0 | …>
[=] 8/0x08 | 8A 00 00 00 | 0 | …
[=] 9/0x09 | 42 45 47 49 | 0 | BEGI
[=] 10/0x0A | 4E 3A 56 43 | 0 | N:VC
[=] 11/0x0B | 41 52 44 0D | 0 | ARD.
[=] 12/0x0C | 0A 56 45 52 | 0 | .VER
[=] 13/0x0D | 53 49 4F 4E | 0 | SION
[=] 14/0x0E | 3A 33 2E 30 | 0 | :3.0
[=] 15/0x0F | 0D 0A 50 52 | 0 | …PR
[=] 16/0x10 | 4F 44 49 44 | 0 | ODID
[=] 17/0x11 | 3A 2D 2F 2F | 0 | :-//
[=] 18/0x12 | 41 70 70 6C | 0 | Appl
[=] 19/0x13 | 65 20 49 6E | 0 | e In
[=] 20/0x14 | 63 2E 2F 2F | 0 | c.//
[=] 21/0x15 | 69 50 68 6F | 0 | iPho
[=] 22/0x16 | 6E 65 20 4F | 0 | ne O
[=] 23/0x17 | 53 20 31 34 | 0 | S 14
[=] 24/0x18 | 2E 34 2F 2F | 0 | .4//
[=] 25/0x19 | 45 4E 0D 0A | 0 | EN…
[=] 26/0x1A | 4E 3A 42 61 | 0 | N:Ba
[=] 27/0x1B | 72 74 65 72 | 0 | rter
[=] 28/0x1C | 3B 50 65 74 | 0 | ;Pet
[=] 29/0x1D | 65 3B 3B 3B | 0 | e;;;
[=] 30/0x1E | 0D 0A 46 4E | 0 | …FN
[=] 31/0x1F | 3A 50 65 74 | 0 | :Pet
[=] 32/0x20 | 65 20 42 61 | 0 | e Ba
[=] 33/0x21 | 72 74 65 72 | 0 | rter
[=] 34/0x22 | 0D 0A 4E 49 | 0 | …NI
[=] 35/0x23 | 43 4B 4E 41 | 0 | CKNA
[=] 36/0x24 | 4D 45 3A 50 | 0 | ME:P
[=] 37/0x25 | 65 74 65 0D | 0 | ete.
[=] 38/0x26 | 0A 4F 52 47 | 0 | .ORG
[=] 39/0x27 | 3A 53 41 4D | 0 | :SAM
[=] 40/0x28 | 69 69 3B 0D | 0 | ii;.
[=] 41/0x29 | 0A 54 49 54 | 0 | .TIT
[=] 42/0x2A | 4C 45 3A 46 | 0 | LE:F
[=] 43/0x2B | 6F 75 6E 64 | 0 | ound
[=] 44/0x2C | 65 72 20 2F | 0 | er /
[=] 45/0x2D | 20 44 69 72 | 0 | Dir
[=] 46/0x2E | 65 63 74 6F | 0 | ecto
[=] 47/0x2F | 72 0D 0A 45 | 0 | r…E
[=] 48/0x30 | 4D 41 49 4C | 0 | MAIL
[=] 49/0x31 | 3B 74 79 70 | 0 | ;typ
[=] 50/0x32 | 65 3D 49 4E | 0 | e=IN
[=] 51/0x33 | 54 45 52 4E | 0 | TERN
[=] 52/0x34 | 45 54 3B 74 | 0 | ET;t
[=] 53/0x35 | 79 70 65 3D | 0 | ype=
[=] 54/0x36 | 57 4F 52 4B | 0 | WORK
[=] 55/0x37 | 3B 74 79 70 | 0 | ;typ
[=] 56/0x38 | 65 3D 70 72 | 0 | e=pr
[=] 57/0x39 | 65 66 3A 70 | 0 | ef:p
[=] 58/0x3A | 65 74 65 62 | 0 | eteb
[=] 59/0x3B | 61 72 74 65 | 0 | arte
[=] 60/0x3C | 72 65 74 69 | 0 | reti
[=] 61/0x3D | 40 67 6D 61 | 0 | @gma
[=] 62/0x3E | 69 6C 2E 63 | 0 | il.c
[=] 63/0x3F | 6F 6D 0D 0A | 0 | om…
[=] 64/0x40 | 54 45 4C 3B | 0 | TEL;
[=] 65/0x41 | 74 79 70 65 | 0 | type
[=] 66/0x42 | 3D 43 45 4C | 0 | =CEL
[=] 67/0x43 | 4C 3B 74 79 | 0 | L;ty
[=] 68/0x44 | 70 65 3D 56 | 0 | pe=V
[=] 69/0x45 | 4F 49 43 45 | 0 | OICE
[=] 70/0x46 | 3B 74 79 70 | 0 | ;typ
[=] 71/0x47 | 65 3D 70 72 | 0 | e=pr
[=] 72/0x48 | 65 66 3A 30 | 0 | ef:0
[=] 73/0x49 | 34 30 31 20 | 0 | 401
[=] 74/0x4A | 34 37 36 20 | 0 | 476
[=] 75/0x4B | 37 39 36 0D | 0 | 796.
[=] 76/0x4C | 0A 54 45 4C | 0 | .TEL
[=] 77/0x4D | 3B 74 79 70 | 0 | ;typ
[=] 78/0x4E | 65 3D 57 4F | 0 | e=WO
[=] 79/0x4F | 52 4B 3B 74 | 0 | RK;t
[=] 80/0x50 | 79 70 65 3D | 0 | ype=
[=] 81/0x51 | 56 4F 49 43 | 0 | VOIC
[=] 82/0x52 | 45 3A 31 33 | 0 | E:13
[=] 83/0x53 | 30 30 20 33 | 0 | 00 3
[=] 84/0x54 | 38 34 20 35 | 0 | 84 5
[=] 85/0x55 | 38 33 0D 0A | 0 | 83…
[=] 86/0x56 | 41 44 52 3B | 0 | ADR;
[=] 87/0x57 | 74 79 70 65 | 0 | type
[=] 88/0x58 | 3D 48 4F 4D | 0 | =HOM
[=] 89/0x59 | 45 3B 74 79 | 0 | E;ty
[=] 90/0x5A | 70 65 3D 70 | 0 | pe=p
[=] 91/0x5B | 72 65 66 3A | 0 | ref:
[=] 92/0x5C | 3B 3B 33 33 | 0 | ;;33
[=] 93/0x5D | 20 57 61 72 | 0 | War
[=] 94/0x5E | 77 69 63 6B | 0 | wick
[=] 95/0x5F | 20 61 76 5C | 0 | av\
[=] 96/0x60 | 6E 3B 57 61 | 0 | n;Wa
[=] 97/0x61 | 6C 6B 65 72 | 0 | lker
[=] 98/0x62 | 76 69 6C 6C | 0 | vill
[=] 99/0x63 | 3B 53 61 3B | 0 | ;Sa;
[=] 100/0x64 | 35 30 38 31 | 0 | 5081
[=] 101/0x65 | 3B 41 75 73 | 0 | ;Aus
[=] 102/0x66 | 74 72 61 6C | 0 | tral
[=] 103/0x67 | 69 61 0D 0A | 0 | ia…
[=] 104/0x68 | 69 74 65 6D | 0 | item
[=] 105/0x69 | 31 2E 55 52 | 0 | 1.UR
[=] 106/0x6A | 4C 3B 74 79 | 0 | L;ty
[=] 107/0x6B | 70 65 3D 70 | 0 | pe=p
[=] 108/0x6C | 72 65 66 3A | 0 | ref:
[=] 109/0x6D | 50 65 74 65 | 0 | Pete
[=] 110/0x6E | 62 61 72 74 | 0 | bart
[=] 111/0x6F | 65 72 2E 63 | 0 | er.c
[=] 112/0x70 | 6F 6D 0D 0A | 0 | om…
[=] 113/0x71 | 69 74 65 6D | 0 | item
[=] 114/0x72 | 31 2E 58 2D | 0 | 1.X-
[=] 115/0x73 | 41 42 4C 61 | 0 | ABLa
[=] 116/0x74 | 62 65 6C 3A | 0 | bel:
[=] 117/0x75 | 5F 24 21 3C | 0 | _$!<
[=] 118/0x76 | 48 6F 6D 65 | 0 | Home
[=] 119/0x77 | 50 61 67 65 | 0 | Page
[=] 120/0x78 | 3E 21 24 5F | 0 | >!$_
[=] 121/0x79 | 0D 0A 42 44 | 0 | …BD
[=] 122/0x7A | 41 59 3A 31 | 0 | AY:1
[=] 123/0x7B | 39 38 30 2D | 0 | 980-
[=] 124/0x7C | 30 39 2D 30 | 0 | 09-0
[=] 125/0x7D | 39 0D 0A 45 | 0 | 9…E
[=] 126/0x7E | 4E 44 3A 56 | 0 | ND:V
[=] 127/0x7F | 43 41 52 44 | 0 | CARD
[=] 128/0x80 | 0D 0A FE 00 | 0 | …
[=] 129/0x81 | 00 00 00 00 | 0 | …
[=] 130/0x82 | 00 00 00 00 | 0 | …
[=] 131/0x83 | 00 00 00 00 | 0 | …
[=] 132/0x84 | 00 00 00 00 | 0 | …
[=] 133/0x85 | 00 00 00 00 | 0 | …
[=] 134/0x86 | 00 00 00 00 | 0 | …
[=] 135/0x87 | 00 00 00 00 | 0 | …
[=] 136/0x88 | 00 00 00 00 | 0 | …
[=] 137/0x89 | 00 00 00 00 | 0 | …
[=] 138/0x8A | 00 00 00 00 | 0 | …
[=] 139/0x8B | 00 00 00 00 | 0 | …
[=] 140/0x8C | 00 00 00 00 | 0 | …
[=] 141/0x8D | 00 00 00 00 | 0 | …
[=] 142/0x8E | 00 00 00 00 | 0 | …
[=] 143/0x8F | 00 00 00 00 | 0 | …
[=] 144/0x90 | 00 00 00 00 | 0 | …
[=] 145/0x91 | 00 00 00 00 | 0 | …
[=] 146/0x92 | 00 00 00 00 | 0 | …
[=] 147/0x93 | 00 00 00 00 | 0 | …
[=] 148/0x94 | 00 00 00 00 | 0 | …
[=] 149/0x95 | 00 00 00 00 | 0 | …
[=] 150/0x96 | 00 00 00 00 | 0 | …
[=] 151/0x97 | 00 00 00 00 | 0 | …
[=] 152/0x98 | 00 00 00 00 | 0 | …
[=] 153/0x99 | 00 00 00 00 | 0 | …
[=] 154/0x9A | 00 00 00 00 | 0 | …
[=] 155/0x9B | 00 00 00 00 | 0 | …
[=] 156/0x9C | 00 00 00 00 | 0 | …
[=] 157/0x9D | 00 00 00 00 | 0 | …
[=] 158/0x9E | 00 00 00 00 | 0 | …
[=] 159/0x9F | 00 00 00 00 | 0 | …
[=] 160/0xA0 | 00 00 00 00 | 0 | …
[=] 161/0xA1 | 00 00 00 00 | 0 | …
[=] 162/0xA2 | 00 00 00 00 | 0 | …
[=] 163/0xA3 | 00 00 00 00 | 0 | …
[=] 164/0xA4 | 00 00 00 00 | 0 | …
[=] 165/0xA5 | 00 00 00 00 | 0 | …
[=] 166/0xA6 | 00 00 00 00 | 0 | …
[=] 167/0xA7 | 00 00 00 00 | 0 | …
[=] 168/0xA8 | 00 00 00 00 | 0 | …
[=] 169/0xA9 | 00 00 00 00 | 0 | …
[=] 170/0xAA | 00 00 00 00 | 0 | …
[=] 171/0xAB | 00 00 00 00 | 0 | …
[=] 172/0xAC | 00 00 00 00 | 0 | …
[=] 173/0xAD | 00 00 00 00 | 0 | …
[=] 174/0xAE | 00 00 00 00 | 0 | …
[=] 175/0xAF | 00 00 00 00 | 0 | …
[=] 176/0xB0 | 00 00 00 00 | 0 | …
[=] 177/0xB1 | 00 00 00 00 | 0 | …
[=] 178/0xB2 | 00 00 00 00 | 0 | …
[=] 179/0xB3 | 00 00 00 00 | 0 | …
[=] 180/0xB4 | 00 00 00 00 | 0 | …
[=] 181/0xB5 | 00 00 00 00 | 0 | …
[=] 182/0xB6 | 00 00 00 00 | 0 | …
[=] 183/0xB7 | 00 00 00 00 | 0 | …
[=] 184/0xB8 | 00 00 00 00 | 0 | …
[=] 185/0xB9 | 00 00 00 00 | 0 | …
[=] 186/0xBA | 00 00 00 00 | 0 | …
[=] 187/0xBB | 00 00 00 00 | 0 | …
[=] 188/0xBC | 00 00 00 00 | 0 | …
[=] 189/0xBD | 00 00 00 00 | 0 | …
[=] 190/0xBE | 00 00 00 00 | 0 | …
[=] 191/0xBF | 00 00 00 00 | 0 | …
[=] 192/0xC0 | 00 00 00 00 | 0 | …
[=] 193/0xC1 | 00 00 00 00 | 0 | …
[=] 194/0xC2 | 00 00 00 00 | 0 | …
[=] 195/0xC3 | 00 00 00 00 | 0 | …
[=] 196/0xC4 | 00 00 00 00 | 0 | …
[=] 197/0xC5 | 00 00 00 00 | 0 | …
[=] 198/0xC6 | 00 00 00 00 | 0 | …
[=] 199/0xC7 | 00 00 00 00 | 0 | …
[=] 200/0xC8 | 00 00 00 00 | 0 | …
[=] 201/0xC9 | 00 00 00 00 | 0 | …
[=] 202/0xCA | 00 00 00 00 | 0 | …
[=] 203/0xCB | 00 00 00 00 | 0 | …
[=] 204/0xCC | 00 00 00 00 | 0 | …
[=] 205/0xCD | 00 00 00 00 | 0 | …
[=] 206/0xCE | 00 00 00 00 | 0 | …
[=] 207/0xCF | 00 00 00 00 | 0 | …
[=] 208/0xD0 | 00 00 00 00 | 0 | …
[=] 209/0xD1 | 00 00 00 00 | 0 | …
[=] 210/0xD2 | 00 00 00 00 | 0 | …
[=] 211/0xD3 | 00 00 00 00 | 0 | …
[=] 212/0xD4 | 00 00 00 00 | 0 | …
[=] 213/0xD5 | 00 00 00 00 | 0 | …
[=] 214/0xD6 | 00 00 00 00 | 0 | …
[=] 215/0xD7 | 00 00 00 00 | 0 | …
[=] 216/0xD8 | 00 00 00 00 | 0 | …
[=] 217/0xD9 | 00 00 00 00 | 0 | …
[=] 218/0xDA | 00 00 00 00 | 0 | …
[=] 219/0xDB | 00 00 00 00 | 0 | …
[=] 220/0xDC | 00 00 00 00 | 0 | …
[=] 221/0xDD | 00 00 00 00 | 0 | …
[=] 222/0xDE | 00 00 00 00 | 0 | …
[=] 223/0xDF | 00 00 00 00 | 0 | …
[=] 224/0xE0 | 00 00 00 00 | 0 | …
[=] 225/0xE1 | 4E 45 78 54 | 0 | NExT
[=] 226/0xE2 | 00 00 7F BD | 0 | …
[=] 227/0xE3 | 04 00 00 E3 | 0 | …
[=] 228/0xE4 | 00 05 00 00 | 0 | …
[=] 229/0xE5 | 00 00 00 00 | 0 | …
[=] 230/0xE6 | 00 00 00 00 | 0 | …
[=] ---------------------------------
[=] Restoring data blocks.
[=] …[#] Cmd Send Error: 00 1
[#] Write block error
( truncated )
[#] Write block error
[!] ![]() failed to write block 223
failed to write block 223
.[#] Cmd Send Error: 00 1
[#] Write block error
[!] ![]() failed to write block 224
failed to write block 224
.[#] Cmd Send Error: 00 1
[#] Write block error
[!] ![]() failed to write block 225
failed to write block 225
.
[=] Restore finished
[ usb ] pm3 →
WINNER . ![]()
Im documenting all these moves so in the unlikley event that someone as nube as me needs the info they can push through anntil they get a expected result.
For my next trick. Mifare classic to Mifare classic
yo yo, figured it out .
Mifare classic 1k
Run -
hf mf autopwn * 1 f mfc_default_keys
[+] Generating binary key file
[+] Found keys have been dumped to hf-mf-83C16184-key.bin
[=] FYI! → 0xFFFFFFFFFFFF ← has been inserted for unknown keys where res is 0
[+] transferring keys to simulator memory (Cmd Error: 04 can occur)
[=] downloading the card content from emulator memory
[+] saved 1024 bytes to binary file hf-mf-83C16184-dump.bin
[+] saved 64 blocks to text file hf-mf-83C16184-dump.eml
[+] saved to json file hf-mf-########-dump.json
[=] autopwn execution time: 11 seconds
Then -
hf mf restore 1 u ########
I’m Scottish (and on the West Coast) so… No. ![]()
I’m glad that you got it working.