We are finally offering the Disney MagicBand puck conversion service to the general public.
Never been to a Disney park but I so wanna do this if I ever can xD
Are there any side uses to this? Could you also enroll it in a different system or do the keys lock you out of any use other than Disney’s?
it’s a desfire ev1 chip with 7 byte UID so maybe?
Is it using the new wedge format or the older copper format?
that depends… i have lots of copper coil wires for the wedge design, but i should be able to work out a new straight flex with the new antennas as well.
hmmm…
ah so no technical changes… that’s good ![]()
I bet we could also convert the “key to the world” cards too … anyone have one of those I could check out?
I imaging the switch to a smartphone app will also facilitate contact tracing.
Not that I care… but anyone want to take bets on Disney sending a cease and desist? Seems their style
I’m pretty sure I have a stash. Let me find them and I’ll scan one with the proxmark and send it your way if you want.
As a Disney shareholder, I agree with you and the protection of my IP 100%. ![]()
So, if Disney wants to stop this they tell DT to remove the service.
And DT has to decline all custom flex work with MagicBands.
But I could just extract the chip myself in about 0.1 milliseconds and send it to DT.
DT wouldn’t even know it’s Disney, so in effect, Disney implants exist now and will never be stopped.
Unless they deliberately change to make removing the chip impossible or make them active or uhf.
they added a sticker saying no implants
Absolutely destroyed. 10/10, the mouse knows all.
Problem with changing now is they’d have to replace the readers at every fastpass ride, every park turnstile, and every hotel room door. They’ve already said they’re not recouping the cost of the initial install as much as they’d hoped.
Also @amal, my wife cleaned up my “clutter” so I’m still looking for that card. When I find it I’ll pm you for an address.
Ok, so some good news / bad news.
Bad news: It seems that all my old Key to the Kingdom cards have been thrown out.
Good news: I have active tickets that are on cards.
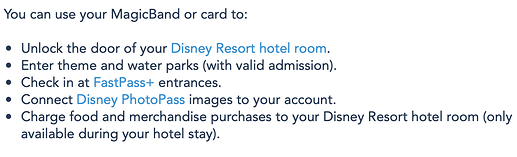
So Disney is pushing for all digital tickets sold through their website/app but you can still buy card tickets from some other outlets. These come on a card with a mag stripe, NFC, and a QR code on them. They also offer the Key to the Kingdom cards to anyone who has bought a ticket digitally online but doesn’t want to pay for a magicband. I bet these cards are the same. Looking at their website it seems the ticket cards have the same capabilities as the magicbands in key areas:
Here is a picture of the new Key to the Kingdom cards:
And here is a picture of the ticket cards:
And the back side with the QR code, serial #, and my name blanked out (this is still valid admission):
I did some candling to find the chip and it looks like other transit cards that @amal has done with a chip and obvious antenna lines attached and looping around the cards perimeter:
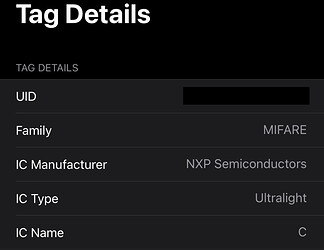
In fact I scanned it with NXP TagInfo and found it not to be a DESfire but a MiFare Ultralight:
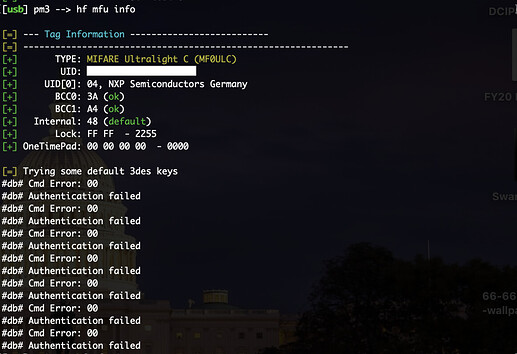
So I plopped it on the proxmark and found this:
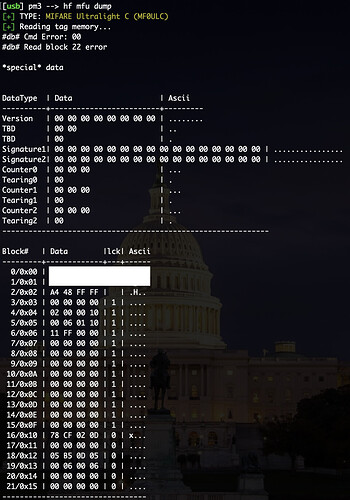
Also tried to dump the contents but it failed after block 21. Is this a possible encryption issue?
So unfortunately I can’t come through with sending you the card because I still need it until the fall. I can however do any more scans that would be of use. Also, is it possible that it is only looking at the UID and this could be cloned by the flexMN?? I might get a magic card and bring it with me on my next trip just to see if it will let me in my room.
i have seen some of their cards use an actual Ultralight C which has an “admin feature” which is under NDA to even learn about… but as I gather the ultralight feature progression went Ultralight > Ultralight C with “admin” feature > NTAG with “password” feature… so I’m pretty sure the “admin” feature of the Ultralight C is just the precursor to the password feature of the NTAG. Perhaps blocks beyond 21 are protected with the “admin” feature and accessible once successful authentication has been performed.
The interesting thing here though is that like the NTAG password feature, I’m pretty sure it is not “encryption”, just a standard password sent in the clear to the card which unlocks those memory blocks… in theory you could sniff the convo and get the password easy peasy.