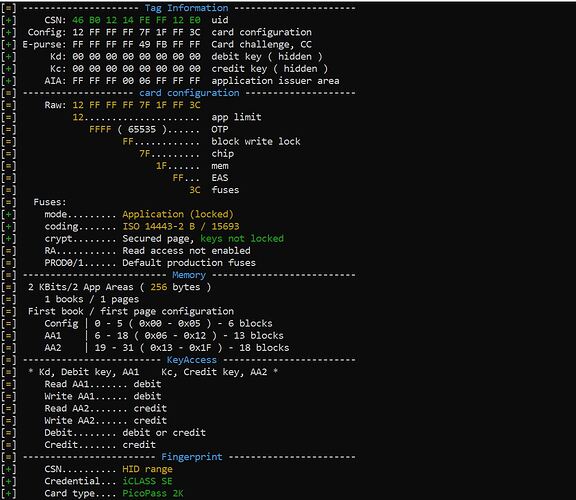
This is the tag information for the tag I am trying to clone. I cannot read the block information for some reason…maybe because its an SE tag?
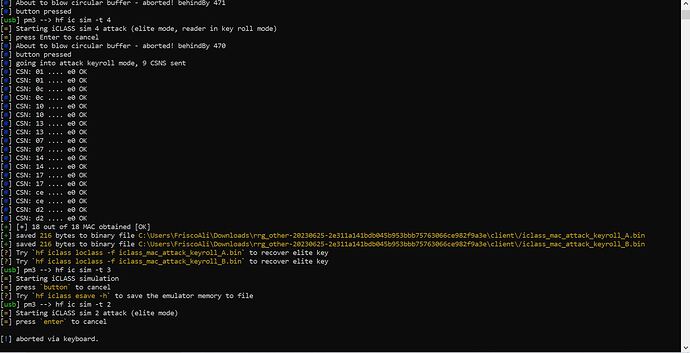
So I used the command “hf iclass sim -t 4” for a reader attack and it actually did something. This is what I got when I placed the proxmark3 next to the reader while the oriignal fob communicated with the reader. Any ideas what I can do with this information?
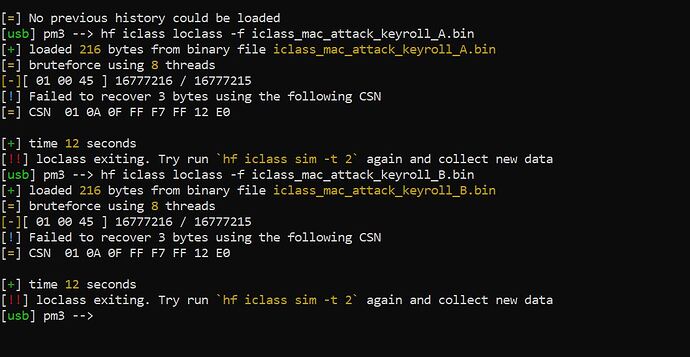
It said to do this to recover the “elite key” from the bin file, as you can see from the pic below. It says it used CSN 01 0A 0F FF F7 FF 12 E0 for the attack? but the CSN of the original fob is actually something different. I have no idea what I’m looking at though, just trying out different methods. Any ideas what I could do with this info?
@NinjuhhNutz @philidelphiaChickens
iClass SE can’t be cloned in this manner
I have no clue about SE. I’ve had so much going on lately, I’ve been MIA on the forum in general. Sorry, wish I could help.
pm3 → hf iclass dump -k 34573C1798D0269B --elite
elite key - 34573C1798D0269B
So, fill me in on this. How is the elite key calculated? Is it UID dependent? Is it data block 6-9 dependent? Did the iClass gods shake their angered fists and hex bits fall out? ![]()
The key for Elite cards is set by the manufacturer. You won’t be able to copy the Elite card without knowing the key. I entered my Elite card manufacturer key.
That much makes sense, but there’s got to be some way that the elite key is generated. Surely it’s not a master key, so it’s obfuscated somehow. I’m interested to see how that’s done once it’s cracked.