I was trying to clone my work badge to my newly installed xMagic but I’ve run into a few snags, just goes to show that the Proxmark3 is an awesome tool that should be used before ordering and installing implants, story time.
So I had a thought of cloning the access badge for work out of convenience and cool to have, since I got my flipper a while ago I’ve been diving more and more into a lot of things, anyhow, either I’m missing something or the flipper isn’t as capable yet in the ways of NFC reading as one could want it to be, Proxmark3 reigns supreme.
So neither with the flipper or MCT app could I read that my “clearly” work badge was anything else than a mifare classic 1k 14443-A tag, 1024 byte and 16 (0-15) sectors.
We got the 0-15 sectors and everything looks great, the xMagic was perfect with it’s capabilities and T5577 for emulating the RFID part as well, hence I ordered and have now installed it with help of a professional.
Everything is healing well and feels ok, no issues there.
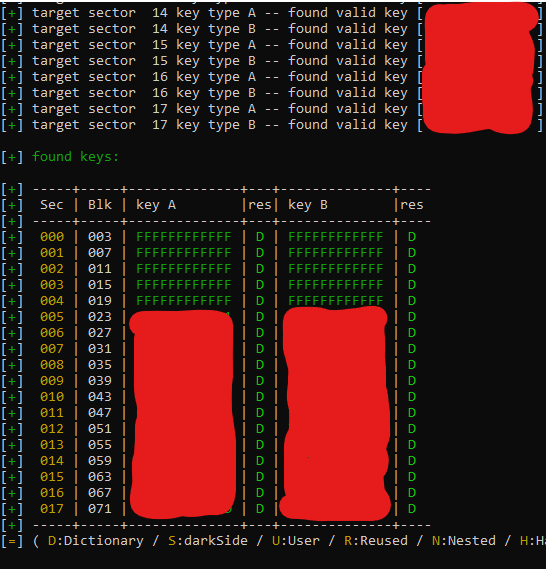
That’s untill I tried cloning the badge onto my xMagic, when writing the cloned work badge, I saw that it was missing 2 sectors from my dump of the existing badge, 16 and 17 (18 in total).
Running “hf mf info” generated this output:
[=] — ISO14443-a Information ---------------------
[+] UID: XX XX XX XX [detected but hidden by me]
[+] ATQA: 00 04
[+] SAK: 08 [2]
[=]
[=] — Tag Signature
[=] IC signature public key name: NXP MIFARE Classic MFC1C14_x
[=] IC signature public key value: [got it but hidden by me]
[=] Elliptic curve parameters: NID_secp128r1
[=] TAG IC Signature: XX XX XX XX XX XX XX XX XX XX XX XX XX XX XX XX [got it but hidden by me]
[+] Signature verification: successful
[=] — Keys Information
[=] [0] key FF FF FF FF FF FF
[+] loaded 1 keys supplied by user
[+] loaded 61 keys from hardcoded default array
[+] Sector 0 key A… FFFFFFFFFFFF
[+] Sector 0 key B… FFFFFFFFFFFF
[+] Sector 1 key A… FFFFFFFFFFFF
[+] Block 0… [got it but hidden by me]
[=] — Magic Tag Information
[=] <N/A>
[=] — PRNG Information
[+] Prng… hard
So when I did clone it with the “hf mf autopwn” I at first didnt react to the two extra sectors for key A and B until I wrote it to my xMagic, did a clone of my implant and compared the two results out of habit.
A little googling led me to the github thread: Tag RFID 1K with 16 & 17 sectors · Issue #1010 · Proxmark/proxmark3 · GitHub
Where they had a similar issue and tried “hf mfp info” to see that they had a SL1 card on their hands, so I tried it my self and got this output:
[=] — Tag Information ---------------------------
[!!] No card response
[+] UID: XX XX XX XX [detected but hidden by me]
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] proprietary non iso14443-4 card found, RATS not supported
[+] Prng detection… hard
[=]
[=] — Tag Signature
[=] IC signature public key name: NXP MIFARE Classic MFC1C14_x
[=] IC signature public key value: [detected but hidden by me]
[=] Elliptic curve parameters: NID_secp128r1
[=] TAG IC Signature: [detected but hidden by me]
[+] Signature verification: successful
[?] Hint: try hf mf commands
[!!] No card response
[=] — Fingerprint
[=] Size… 2K (4 UID)
[=] SAK… 2K 7b UID
[=] — Security Level (SL)
[+] SL mode… SL1
[=] SL 1: backwards functional compatibility mode (with MIFARE Classic 1K / 4K) with an optional AES authentication
They suspect that in their case it’s a “Mifare Plus EV1 Desfire 2k” tag in reality, but acting like a mifare classic 1k.
I went back to both my flipper and MCT on my phone, verified that they did not see this at all but the 1024 byte data and 16 sectors.
Have I stumbled upon something similar here?
Any comment is appreciated so I can understand what I’m working with here, and it’s ok to call out something completley obvious since I’m still learning my ways around this.