So, I have seen many different post giving hints, recommendations, asking questions, and so on, for how to clone an HID iCLASS DY card. It seems to be the typical choice for a varieties of universities out there. After some months, and much silliness, I have gotten a reliable system down, so I have decided to write a guide. Millage may vary. Also, I am not an expert. This is my first RFID project ever, but I did get it to work, and hope you will too!
First step, buy a Proxmark 3 Easy, found here from Dangerous Things:
So so worth it, so so cool.
Once it has arrived, follow this guide to a tee (I recommend watching the video and following along):
It will get you setup with the latest, greatest software/firmware, all that jazz, on your Proxmark and corresponding personal computer. I did all mine on Windows 10.
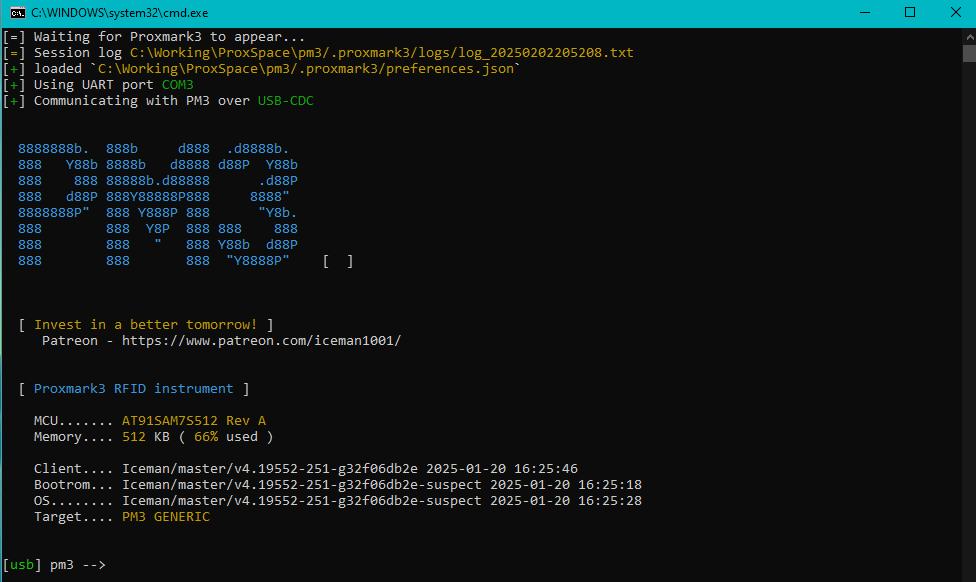
Okay great. After all that, you should end up with the following in your command prompt:
Put the card you want to clone on top of the proxmark, then type into the command prompt:
hf iclass info
It will spit out a bunch of info, but basically you’re looking for this, the fingerprint section, at the very end of the page:
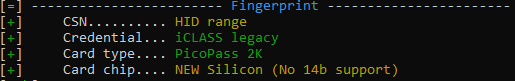
If it says that, all is good. You can then proceed to find the encryption key. I did this by entering:
hf iclass chk -f iclass_elite_keys.dic --elite
This checks the list of default elite keys using the elite computations encryption method. It should spit out a key. Save that key. I put it in a separate .txt file, but it should be somewhere in your sessions logs. Next step, run this:
hf iclass dump -k FFFFFFFFFFFFFFFF --elite
Except, instead of the 16 "F"s, put in the key you just saved somewhere, no spaces, exactly as it was given to you. If you omit the “–elite” at the end, it will not work, at least not for me. If this spits out a tag memory, fabulous. You are in a great place. It should have the headers:
block# | data | ascii |lck| info
I really just paid attention to the block# and data sections. If you have gotten to this point, you need to buy some blank cards. These are what I got:
Or, just anything that says “Brand New HID 2000PGGMN iCLASS PVC Card, iCLASS 13.56 MHz contactless read/write” or something along those lines. You want a readable, writable, blank card that matches that fingerprint from earlier.
Once you have your blank card, you need to copy it over. There may be a more efficient way to do this, but I did it manually. From here on out, it should only be the new, blank card sitting on top of the proxmark. First, find the encryption key for your card. The ones I bought did not use elite computations, so I got the key using this similar command:
hf iclass chk -f iclass_default_keys.dic
That will hopefully spit out the encryption key. Now, you must save that key, like the one you got before. Here comes the tedium. You must copy over all of the blocks from 5 onwards. I don’t know too much about what blocks are necessary, and some seem unused, but I just copied them all, and it worked. Use this command:
hf iclass wrbl --blk 5 -d FFFFFFFFFFFFFFFF -k FFFFFFFFFFFFFFFF
Again, replace the "F"s with the given key/data. The data comes directly after the “-d”, and is what was found after using the dump command from earlier. They key is the one you most recently found, in the previous step, for the new, blank cards, and goes after the “-k”. The block number comes after the “–blk”, and is listed on the table from the dump command from earlier, right next to the data you will write to “-d”. Make sure blocks and data align, i.e., for “–blk” 18, you write the 16 characters that were in the same row from the original card’s dump. I did this manually for every block from 5 to 18. Do not do this for any blocks before 5, yet. Also, block 5 was the same on both cards, as were many, so may not need to be copied over, but I figured I might as well. Now now you must change the key from the one that came with the blank card to that of your original card. It is done through these commands:
hf iclass calcnewkey --old FFFFFFFFFFFFFFFF --new FFFFFFFFFFFFFFFF --elite
Where the “–old” key is the one from your new, blank card, and “–new” is the key from the card you are trying to copy. This will spit out the CSN, epurse, old div key, new div key, and xor div key. Next, run this command:
hf iclass wrbl --blk 3 -d FFFFFFFFFFFFFFFF -k FFFFFFFFFFFFFFFF
Where “-d” is the xor div key and “-k” is the blank card’s original key, i.e., what you just put in the previous command for “–old”.
If you were able to get everything here to work, great! You should now have two effectively identical cards! Go test it out!
I am no expert, but if you have any questions/screenshots/comments/corrections, please feel free to leave them on this thread and I will do my very best to address.
I got quite a huge amount of inspiration form this post:
I would recommend reading the whole thing. That last bit where the new key is calculated and written to block 3 was largely inspired by “[NinjuhhNutz]”'s comment on the post. I recommend reading that as well, as it discusses card that are in personalization vs application mode. I did not delve into personalization mode though, as I found it very difficult to find cards that were in this state, and am trying to make the most direct guide possible. Good luck!
P.S.,
As I get more posting permissions, questions, and comments, I’ll try and order some new cards and make a full YouTube tutorial, but for now, I hope this helps!