I got my NExT installed yesterday. It was giving me no issues. I tried to write using NFC tools and the writing was successful. I went to scan it and now android gives me an invalid tag error. I tried to reformat it with NFC tools , NXP writer, and DT support tool. It does scan using the NXP reader, but not the writer. The full scan data is below.
The tag is showing up at a ntag216 and not a mifare.
You got it implanted yesterday and swelling can make the chip hard to read. So you might have problems for the first two weeks. It’s normal.
Also, proper placement is crucial when writing. I recommend searching for the best spot on the back of your phone with the HF field detector keychain.
1 Like
I read your old thread when you had the same issues. How did you fix it?
I do have a proxmark 3 easy
abc123def4:
How did you fix it?
Just wait…
When your implant is first installed, there is minimal swelling/inflammation.
Then it slowly builds up before dissipating.
2 Likes
PS we can all see your phone number, might want to take the picture down.
Update. it appears to be an issue with block 0. I have tried everything. But when I try to correct block 0 I get an “Auth Error”. Any Idea?
I would still wait for another 1 and a half weeks before trying to do anything with it.
2 Likes
So, I’ve been playing with these tags a bit and I have a theory as to what your problem may be. Android phones often have those digital wallets that detect NFC pads at stores and such. It’s possible when you wrote certain data to your implant, it’s triggering the digital wallet app and erroring out because the digital wallet is being passed data it doesn’t understand. Basically either writting the error over the app you expect, or not triggering it to load at all. It’s still just a theory, but I’m about 70% sure that the issue.
amal
August 22, 2022, 9:27pm
12
Close. Android has an NDEF library that basically forces the OS to fully scan the tag first. All memory sectors. Then decide if it wants to hand over the NFC intent to whatever app might be waiting for it. The problem is, there are certain functions in the NDEF parser that fail hard if the NDEF record is corrupted in certain specific ways. Because the OS can’t handle these failures it just puts an error dialog and stops. The apps never get a chance to even see the NFC tag. Therefore it becomes necessary to fix the NDEF record using an alternative device like a proxmark or a USB reader with the Java version of NFC tools on Windows or Mac.
I tried using the Proxmark to write to the NExT . But when I do I just get a bunch of auth errors. I think when the write went wrong it locked the chip.
amal
August 22, 2022, 10:12pm
14
It’s not really possible to lock the chip. We disable the lock bits at the factory, and the password protected memory content only extends to the configuration bytes and not user memory.
Can you do a dump of the memory from the proxmark?
What are the commands to run
amal
August 23, 2022, 7:50pm
16
can you detail exactly what you mean here?
When I try and write anything to the chip I get an AUTH ERROR. I tried writing a dump file from another tag to it I got the auth error on every sector and every block. Does anyone have a dump file from a fresh NExT I try writing to mine?
amal
August 23, 2022, 8:34pm
18
What I mean is, post the commands you are trying and the responses. Screenshots tend to work best.
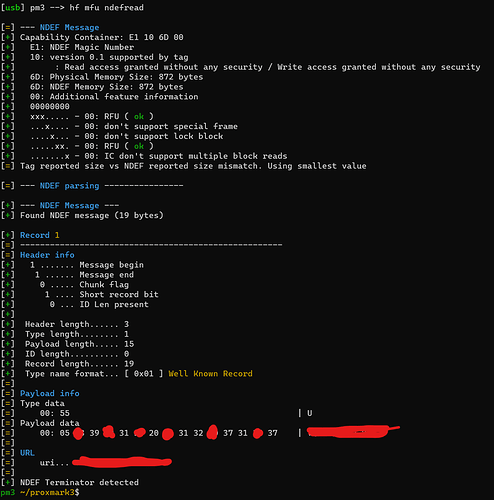
I realized that I was running the wrong commands. I was trying to do and restore the information from a Mifare classic. That is why I was getting all of the errors. This is what the NDEF scan shows from my Proxmark. I do see at the end it has an NDEF terminator at the end. Could this be causing the issue?
Here is what I get when I do a DUMP. The “X” represents a phone number.
[usb] pm3 → hf mfu dump
[=] MFU dump file information
[=] -------------------------------------------------------------NExT
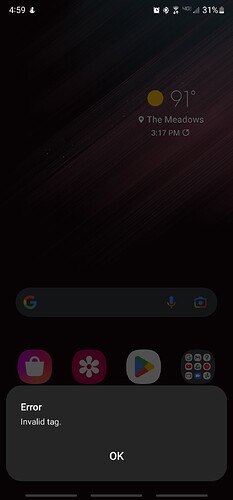
This is the error I get when trying to scan on android.
amal
August 23, 2022, 11:27pm
21
i think at this point i would just zero out all the blocks and see if you can use nfc tools or tagwriter to re-write a basic ndef record to it. i believe you can do this by using the write block command over and over;
hf mfu wrbl -b 4 -d 00000000
I think 15 blocks is enough for android to give up.
2 Likes