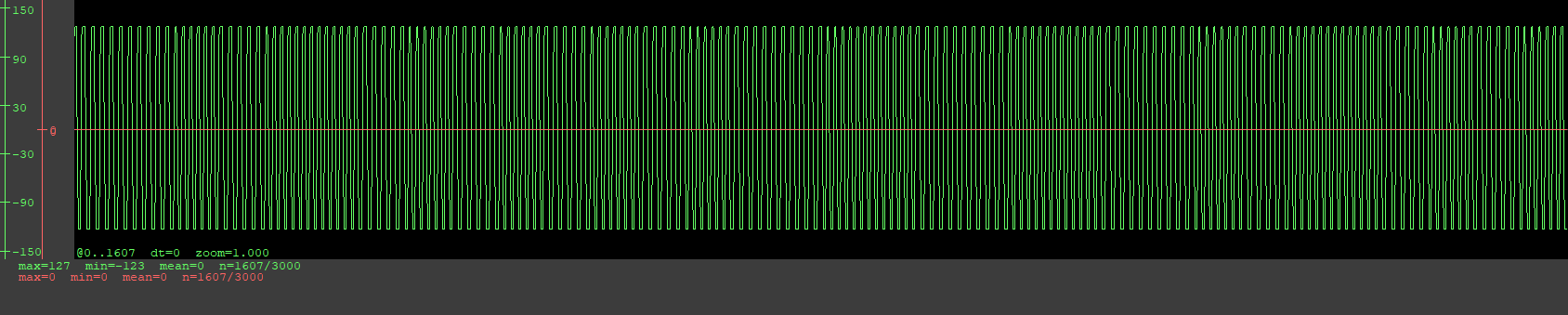
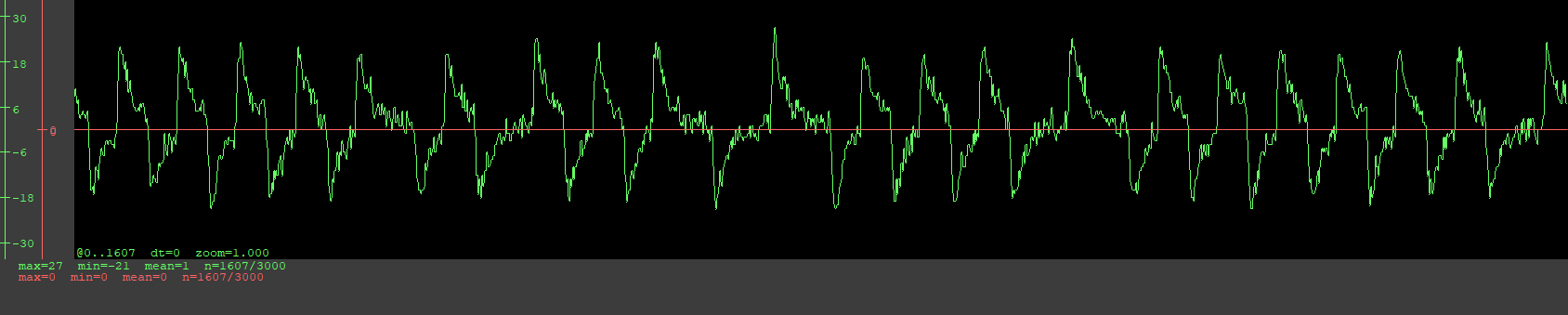
Hi! I was hesitant on creating this but I don’t really know what else to do, I feel like I’ve done it all.
To preface, I installed the NExT Chip approximately three months ago, so it has had plenty of time to heal. I believe it was a week or two after installation, I had written to it with my friend’s FOB (permission granted of course) to see if it would write. I was using the Flipper Zero at the time and it was able to write, but didn’t have any confirmation. I thought nothing of it. When I went to attempt to write again, it just wouldn’t write at all but it was able to read.
I don’t know if this is where I messed up, but my next troubleshooting steps were to attempt a wipe followed by attempting to remove the password, given I didn’t use one. I would clear the password, wipe, clear again, attempt a wipe, you get the idea. (All on the Flipper Zero)
Up until now, with working with the FlexUG4 in my other hand (not related to this ticket), I wanted to give it another shot.
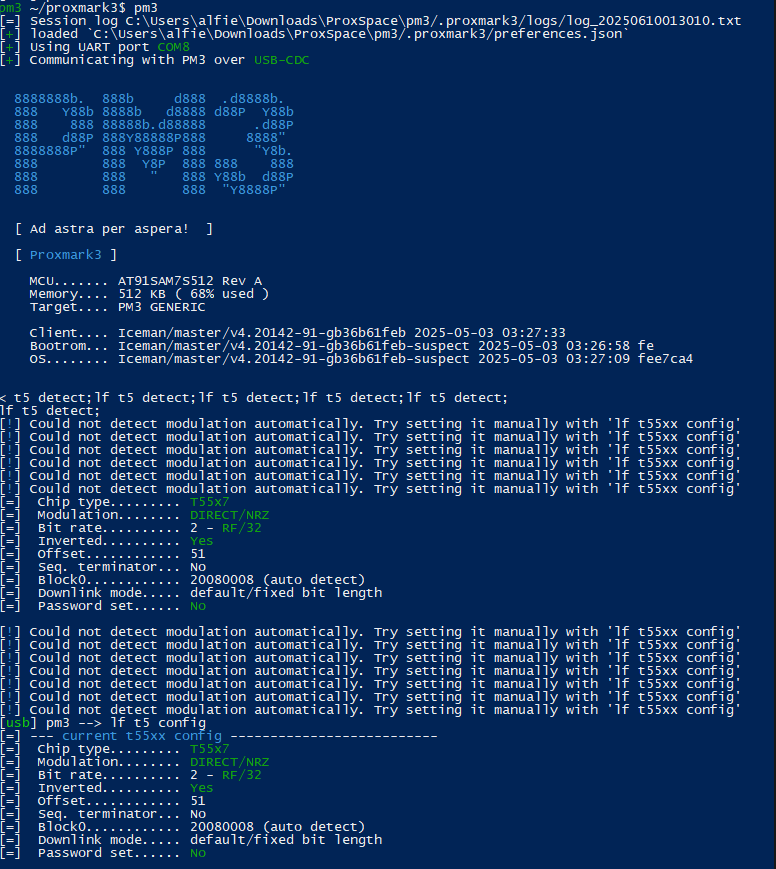
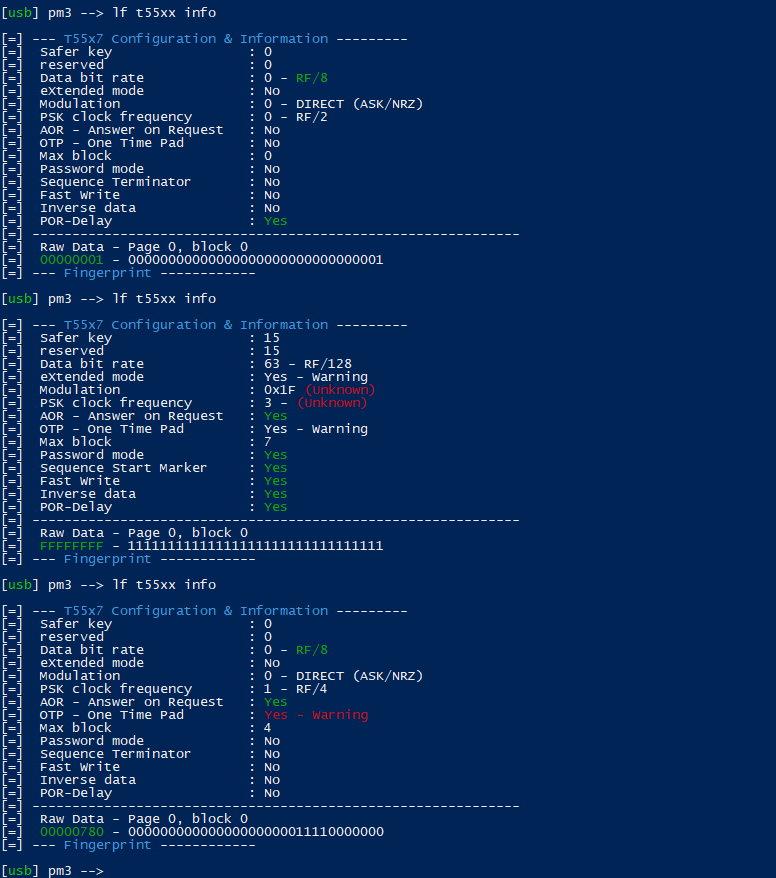
I don’t know if this is the “gotcha” of the ticket, but when running lf t55xx info multiple times against this chip, it gives the following:
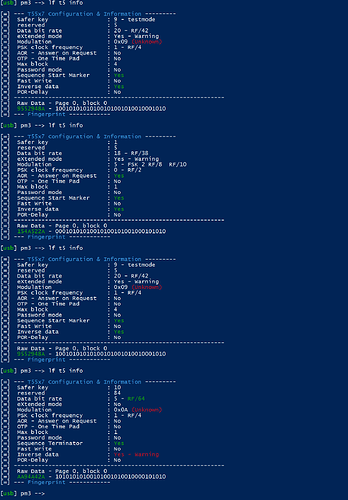
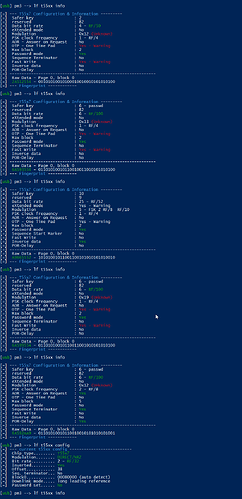
[usb] pm3 --> lf t55xx info
[=] --- T55x7 Configuration & Information ---------
[=] Safer key : 15
[=] reserved : 15
[=] Data bit rate : 63 - RF/128
[=] eXtended mode : Yes - Warning
[=] Modulation : 0x1F (Unknown)
[=] PSK clock frequency : 3 - (Unknown)
[=] AOR - Answer on Request : Yes
[=] OTP - One Time Pad : Yes - Warning
[=] Max block : 7
[=] Password mode : Yes
[=] Sequence Start Marker : Yes
[=] Fast Write : Yes
[=] Inverse data : Yes
[=] POR-Delay : Yes
[=] -------------------------------------------------------------
[=] Raw Data - Page 0, block 0
[=] FFFFFFFF - 11111111111111111111111111111111
[=] --- Fingerprint ------------
[usb] pm3 --> lf t55xx info
[=] --- T55x7 Configuration & Information ---------
[=] Safer key : 15
[=] reserved : 15
[=] Data bit rate : 63 - RF/128
[=] eXtended mode : Yes - Warning
[=] Modulation : 0x1F (Unknown)
[=] PSK clock frequency : 3 - (Unknown)
[=] AOR - Answer on Request : Yes
[=] OTP - One Time Pad : Yes - Warning
[=] Max block : 7
[=] Password mode : Yes
[=] Sequence Start Marker : Yes
[=] Fast Write : Yes
[=] Inverse data : Yes
[=] POR-Delay : Yes
[=] -------------------------------------------------------------
[=] Raw Data - Page 0, block 0
[=] FFFFFFFF - 11111111111111111111111111111111
[=] --- Fingerprint ------------
[usb] pm3 --> lf t55xx info
[usb] pm3 --> lf t55xx info
[usb] pm3 --> lf t55xx info
[=] --- T55x7 Configuration & Information ---------
[=] Safer key : 9 - testmode
[=] reserved : 32
[=] Data bit rate : 4 - RF/50
[=] eXtended mode : No
[=] Modulation : 0 - DIRECT (ASK/NRZ)
[=] PSK clock frequency : 0 - RF/2
[=] AOR - Answer on Request : No
[=] OTP - One Time Pad : Yes - Warning
[=] Max block : 1
[=] Password mode : No
[=] Sequence Terminator : No
[=] Fast Write : No
[=] Inverse data : Yes - Warning
[=] POR-Delay : No
[=] -------------------------------------------------------------
[=] Raw Data - Page 0, block 0
[=] 94100122 - 10010100000100000000000100100010
[=] --- Fingerprint ------------
[usb] pm3 --> lf t55xx info
[=] --- T55x7 Configuration & Information ---------
[=] Safer key : 10
[=] reserved : 72
[=] Data bit rate : 2 - RF/32
[=] eXtended mode : No
[=] Modulation : 0x15 (Unknown)
[=] PSK clock frequency : 0 - RF/2
[=] AOR - Answer on Request : Yes
[=] OTP - One Time Pad : No
[=] Max block : 0
[=] Password mode : Yes
[=] Sequence Terminator : No
[=] Fast Write : No
[=] Inverse data : No
[=] POR-Delay : Yes
[=] -------------------------------------------------------------
[=] Raw Data - Page 0, block 0
[=] A9095211 - 10101001000010010101001000010001
[=] --- Fingerprint ------------
Needless to say, it keeps randomizing block 0. Doing a dump is also random at times:
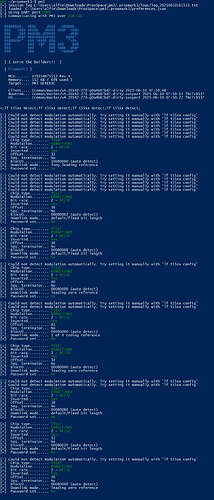
[usb] pm3 --> lf t55xx dump
[=] ------------------------- T55xx tag memory -----------------------------
[+] Page 0
[+] blk | hex data | binary | ascii
[+] ----+----------+----------------------------------+-------
[+] 00 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 01 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 02 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 03 | 00000000 | 00000000000000000000000000000000 | ....
[+] 04 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 05 | 0001FFFF | 00000000000000011111111111111111 | ....
[+] 06 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 07 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] Page 1
[+] blk | hex data | binary | ascii
[+] ----+----------+----------------------------------+-------
[+] 00 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 01 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 02 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 03 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] Saved 48 bytes to binary file `C:\Users\alfie\Downloads\ProxSpace\pm3/lf-t55xx-dump-004.bin`
[+] Saved to json file C:\Users\alfie\Downloads\ProxSpace\pm3/lf-t55xx-dump-004.json
[usb] pm3 --> lf t55xx dump
[=] ------------------------- T55xx tag memory -----------------------------
[+] Page 0
[+] blk | hex data | binary | ascii
[+] ----+----------+----------------------------------+-------
[+] 00 | 00000000 | 00000000000000000000000000000000 | ....
[+] 01 | 00000000 | 00000000000000000000000000000000 | ....
[+] 02 | 00000000 | 00000000000000000000000000000000 | ....
[+] 03 | FFFF8000 | 11111111111111111000000000000000 | ....
[+] 04 | 00000000 | 00000000000000000000000000000000 | ....
[+] 05 | 00000000 | 00000000000000000000000000000000 | ....
[+] 06 | 00000000 | 00000000000000000000000000000000 | ....
[+] 07 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] Page 1
[+] blk | hex data | binary | ascii
[+] ----+----------+----------------------------------+-------
[+] 00 | 00000000 | 00000000000000000000000000000000 | ....
[+] 01 | 00000000 | 00000000000000000000000000000000 | ....
[+] 02 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] 03 | FFFFFFFF | 11111111111111111111111111111111 | ....
[+] Saved 48 bytes to binary file `C:\Users\alfie\Downloads\ProxSpace\pm3/lf-t55xx-dump-005.bin`
[+] Saved to json file C:\Users\alfie\Downloads\ProxSpace\pm3/lf-t55xx-dump-005.json
I had attempted the following:
lf t55xx write -b 0 -d 00107060 -t --r0
lf t55xx write -b 0 -d 00107060 -t --r1
lf t55xx write -b 0 -d 00107060 -t --r2
lf t55xx write -b 0 -d 00107060 -t --r3
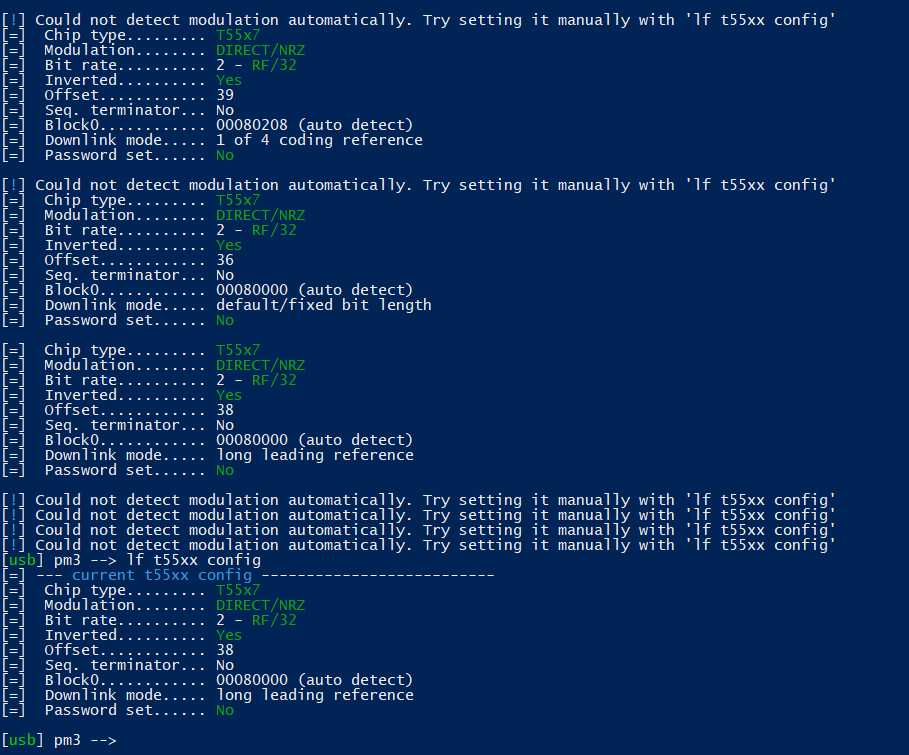
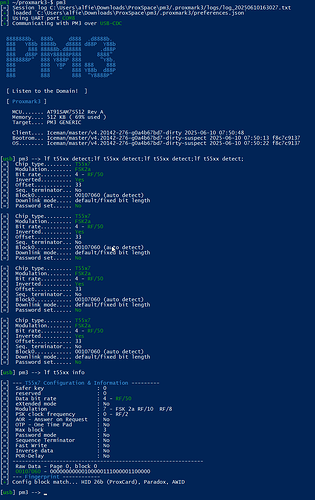
Still nothing. Detect doesn’t work except very rarely, but it only showed the following:
=] Chip type......... T55x7
[=] Modulation........ DIRECT/NRZ
[=] Bit rate.......... 2 - RF/32
[=] Inverted.......... Yes
[=] Offset............ 37
[=] Seq. terminator... No
[=] Block0............ 10080244 (auto detect)
[=] Downlink mode..... 1 of 4 coding reference
[=] Password set...... No
If there’s anything else to suggest, I’m open but I feel like it might be toast. It can still read the very first EM4100 card I wrote to it, so in a way it’s mocking me that I’ll never be able to change it.
Please let me know what suggestions or anything else to run and I’d be more than happy to share the results. Thank you!