Wow you’re AGP old… haha though I bet we both remember the C64 / TSR-80 / PET days.
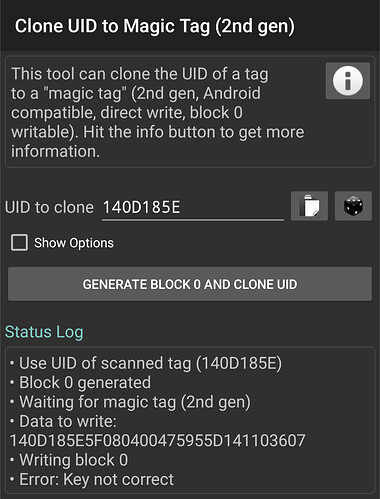
This is what i read for the original tag:
[usb] pm3 --> hf search
[|] Searching for ISO14443-A tag...
[+] UID: 14 0D 18 5E
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] proprietary non iso14443-4 card found, RATS not supported
[+] Prng detection: weak
[#] Auth error
[?] Hint: try `hf mf` commands
[+] Valid ISO 14443-A tag found
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 001 | 007 | 8A19D40CF2B5 | N | 8A19D40CF2B5 | R
[+] 002 | 011 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 003 | 015 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 004 | 019 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 005 | 023 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 006 | 027 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 007 | 031 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 008 | 035 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 009 | 039 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 010 | 043 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 011 | 047 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 012 | 051 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 013 | 055 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 014 | 059 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] 015 | 063 | FFFFFFFFFFFF | D | FFFFFFFFFFFF | D
[+] -----+-----+--------------+---+--------------+----
[usb] pm3 --> hf mf rdsc -s 0
[=] # | sector 00 / 0x00 | ascii
[=] ----+-------------------------------------------------+-----------------
[=] 0 | 14 0D 18 5E 5F 08 04 00 03 7C 67 A9 4E 0D 52 1D | ...^_....|g.N.R.
[=] 1 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] 2 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] 3 | 00 00 00 00 00 00 FF 07 80 69 FF FF FF FF FF FF | .........i......
[usb] pm3 --> hf mf rdsc -s 1 -k 8A19D40CF2B5
[=] # | sector 01 / 0x01 | ascii
[=] ----+-------------------------------------------------+-----------------
[=] 4 | 4D B2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | M...............
[=] 5 | 00 20 11 C1 82 00 0D E1 88 A8 78 D6 14 E9 98 00 | . ........x.....
[=] 6 | F4 3A 69 C8 9A 00 00 00 00 00 00 00 00 00 00 00 | .:i.............
[=] 7 | 00 00 00 00 00 00 FF 07 80 69 8A 19 D4 0C F2 B5 | .........i......
After changing the UG4 to 7 byte UID, i get this error in MTC
So i changed it back to 4 byte UIID and still get the error when tryin to wipe
[usb] pm3 --> script run hf_mf_ultimatecard -w
[+] executing lua C:\PM3\ProxSpace\pm3\proxmark3\client\luascripts/hf_mf_ultimatecard.lua
[+] args '-w'
ERROR:
[+] finished hf_mf_ultimatecard
and now ![]()
[usb] pm3 --> hf mf autopwn
[!] no known key was supplied, key recovery might fail
[+] loaded 56 keys from hardcoded default array
[=] running strategy 1
[=] Chunk 1.5s | found 0/32 keys (56)
[=] running strategy 2
[=] ..
[=] Chunk 5.6s | found 0/32 keys (56)
[=] Expected execution time is about 25seconds on average
[=] Press pm3-button to abort
[=] Running darkside ....................................................................................................................................................................................................................................................................................................................
hrm not a 7 byte then but the uid that was on it 04112233 is usually a placeholder 7byte.
ping me tmr ill have a go at it
The last graphics card I bought was a BFG 9800 GTX and I thought I was the coolest kid
Hahah BFG
I’ve never heard this before… now it’s stuck on repeat.

Check out Fetts Vette. Mc Chris is great if you’re into nerd core
though I bet we both remember the C64 / TSR-80 / PET days.
Not sure if those even made it to south america… But I’m only 486 and ISA old.
But I’m only 486 and ISA old.
oh … hmm… so… you’re a young whipper snapper then. ![]()
But I’m only 486 and ISA old.
My second PC was a 486. I remember those days, when RAM was $100 per meg stick, and a 10MB drive was huge.
The CE mark can be self issued, which wouldn’t be a problem is tracking down chinise companies was possible…
Good thing that china has a need to fake everything so it’s obvious in a some cases. They could technically use any certification logos, who’s going to track them down anyways?
Something something one country two systems with their so called “capitalist market” that is far from a free market and lacks the checks and balances of actual capitalism… And the government remains the owner of the land, natural resources, and large amounts of capital.
Fuck china and their BS in which success heavily mediated by politics and the party instead of market accountability.
Although I will say I use Chinese calipers and they must have got them down to a science because they’re great.
One day I’ll pick up some mitutoyo’s
This was a good video too with some neat tricks.
He has a whole series of songs specifically for some of the other bounty hunters too. Fettes vette is the most famous but Bossk on a segway is my personal fav
He has some bangers. White kids love hip hop and the tussin brings me back.
Thinking of fidget toys I’m reminded of zinc and it’s Tesla meter. I’m wondering @Az_F if you could make a game out of this. Like plot the magnet strength vs time and do something like flappy bird.
Running locally in my
basement!Laboratory Yay!
or
Running locally in my
basement!Lair Yay!
According to google, it’s a Bangladesh version from 1998. The plot seam like it might be a fun watch ![]()