Hey everyone, back again after my regularly scheduled break to talk about cloning my Ultralight EV1 access card. I’ve been toying around with the NTAG21x from KSEC and have found some strange stuff. For reference, cloning aspects of the NTAG21x used the iceman NTAG script and hf mfu commands.
So, first of all, below are the screenshots of the Proxmark3Easy hf mfu info and hf 14a sniff of both the cloned card and original card.
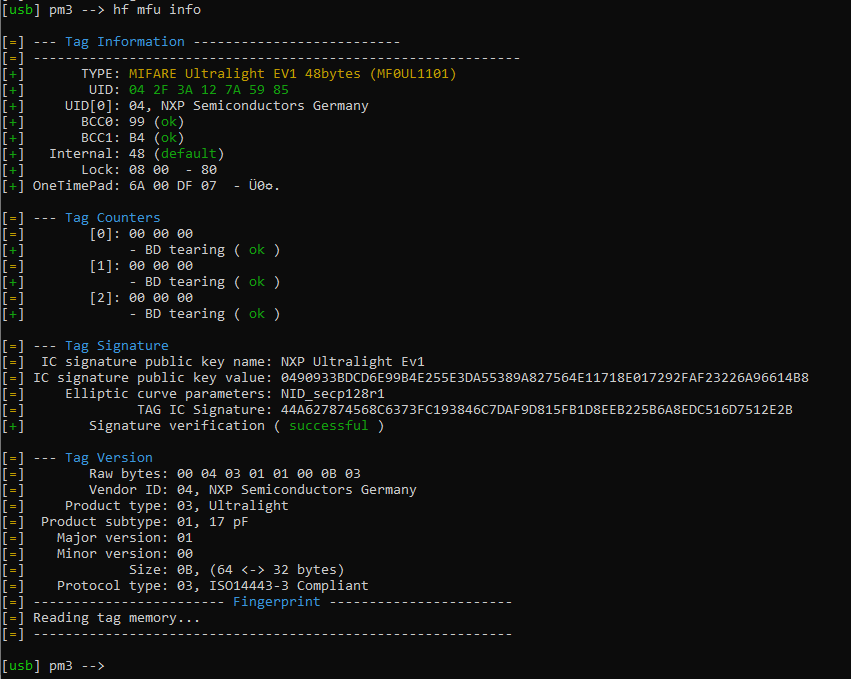
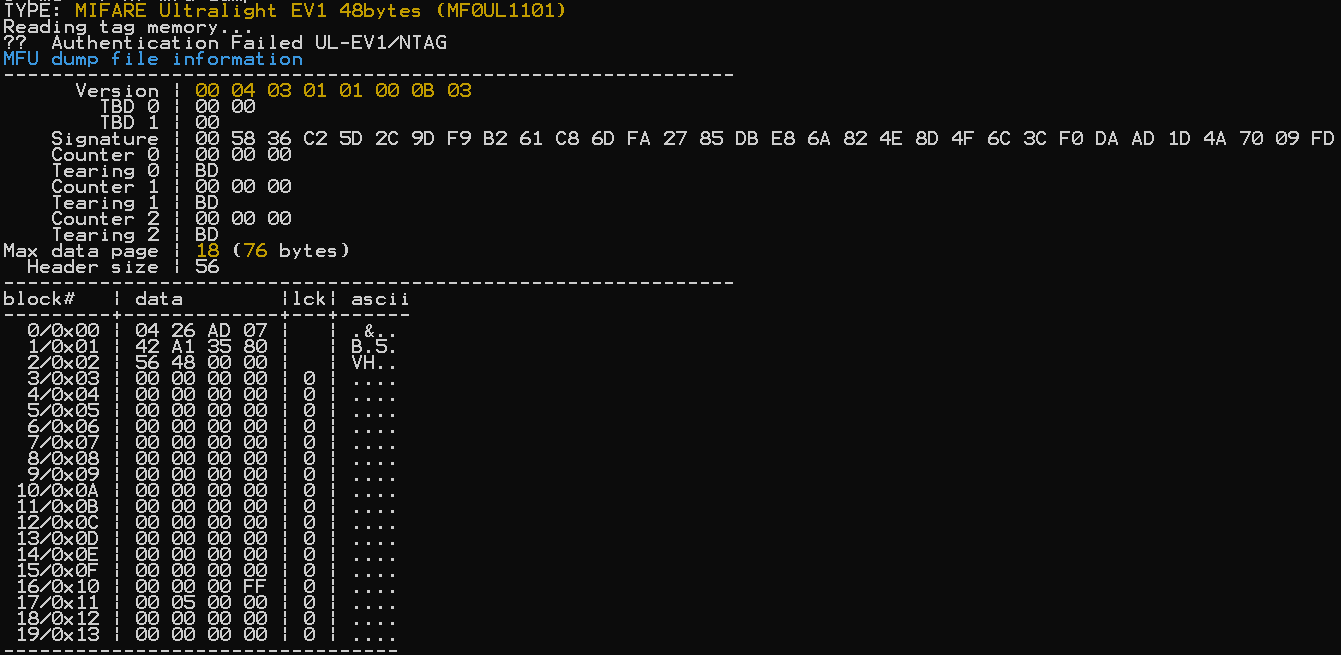
Original Card hf mfu info:
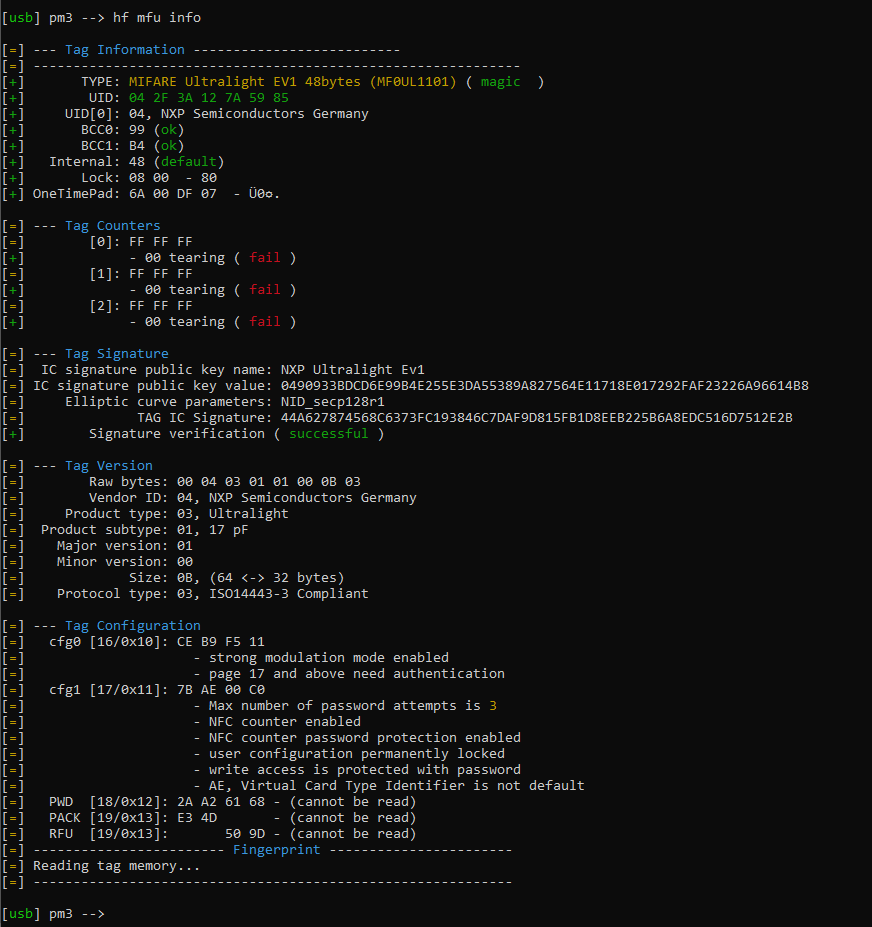
Cloned Card hf mfu info:
For the most part, the two cards look very similar. There also seems to be an issue with the tearing, which is visible in the info screenshot and with the counters in the dump, as well as different “Lock” values, which I’m not sure how to change. The process for figuring out the block content was done through hf mfu rdbl -b BLOCKNUMBER of the original card and then hf mfu wrbl -b BLOCKNUMBER -d 4BYTES on the cloned card.
I then did sniffs on both, doing three separate reads and grabbing the most complete cycle from all three for each.
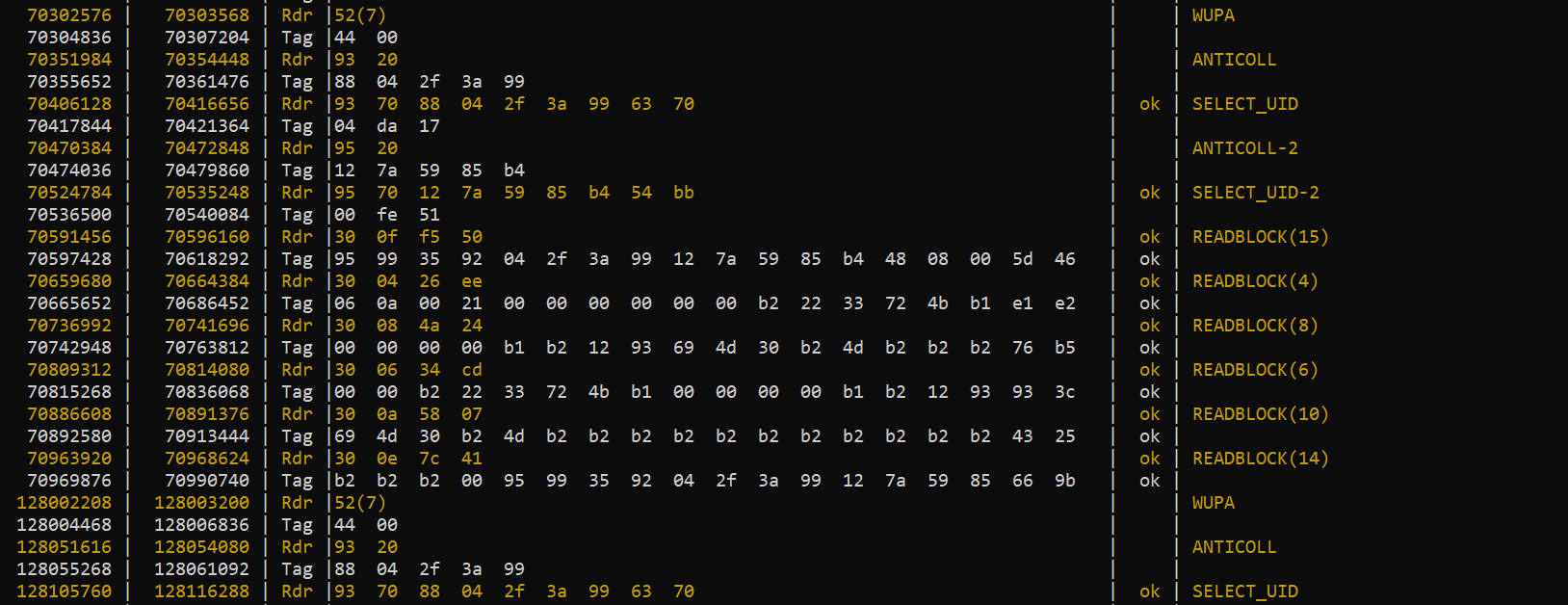
Original Card hf 14a sniff:
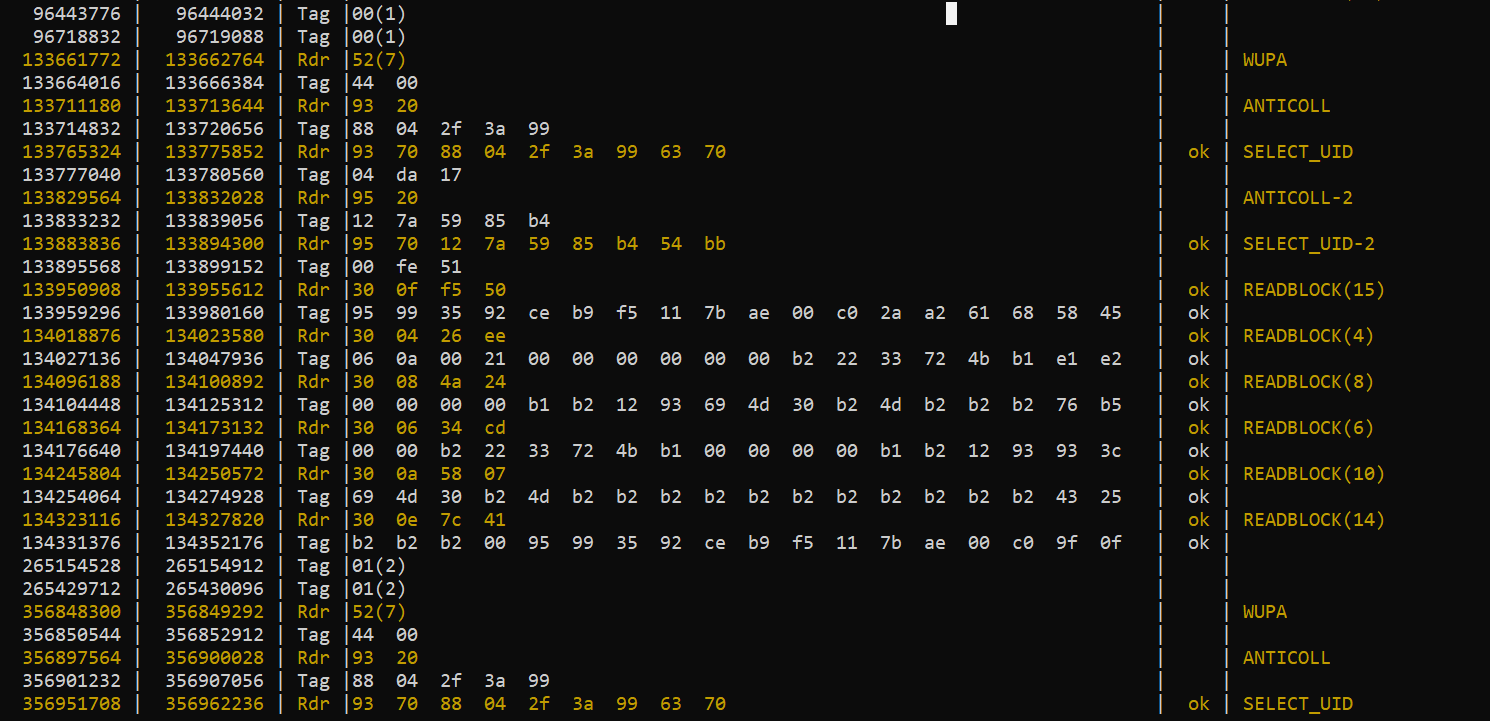
Cloned Card hf 14a sniff:
In reading the blocks from the original card, though, something interesting happened. At some point after reading one of the blocks in the sniff, the original card stopped being recognized by the reader. It would no longer unlock the door, which leads me to believe there may be some sort of protection on the card that de-registers it when someone tries to read a block as some anti-copy protection method?
The dumps for each card are identicaly up until the 15th block, since 16-19 are locked on the real card.
Original Card hf mfu dump:
{
"Created": "proxmark3",
"FileType": "mfu",
"Card": {
"UID": "042F3A127A5985",
"Version": "0004030101000B03",
"TBO_0": "0000",
"TBO_1": "00",
"Signature": "44A627874568C6373FC193846C7DAF9D815FB1D8EEB225B6A8EDC516D7512E2B",
"Counter0": "000000",
"Tearing0": "BD",
"Counter1": "000000",
"Tearing1": "BD",
"Counter2": "000000",
"Tearing2": "BD"
},
"blocks": {
"0": "042F3A99",
"1": "127A5985",
"2": "B4480800",
"3": "6A00DF07",
"4": "060A0021",
"5": "00000000",
"6": "0000B222",
"7": "33724BB1",
"8": "00000000",
"9": "B1B21293",
"10": "694D30B2",
"11": "4DB2B2B2",
"12": "B2B2B2B2",
"13": "B2B2B2B2",
"14": "B2B2B200",
"15": "95993592"
}
}
Cloned Card hf mfu dump:
{
"Created": "proxmark3",
"FileType": "mfu",
"Card": {
"UID": "042F3A127A5985",
"Version": "0004030101000B03",
"TBO_0": "0000",
"TBO_1": "00",
"Signature": "44A627874568C6373FC193846C7DAF9D815FB1D8EEB225B6A8EDC516D7512E2B",
"Counter0": "FFFFFF",
"Tearing0": "00",
"Counter1": "FFFFFF",
"Tearing1": "00",
"Counter2": "FFFFFF",
"Tearing2": "00"
},
"blocks": {
"0": "042F3A99",
"1": "127A5985",
"2": "B4480800",
"3": "6A00DF07",
"4": "060A0021",
"5": "00000000",
"6": "0000B222",
"7": "33724BB1",
"8": "00000000",
"9": "B1B21293",
"10": "694D30B2",
"11": "4DB2B2B2",
"12": "B2B2B2B2",
"13": "B2B2B2B2",
"14": "B2B2B200",
"15": "95993592",
"16": "CEB9F511",
"17": "7BAE00C0",
"18": "2AA26168",
"19": "0000509D"
}
}
Looking at the sniff, I can see some discrepancies, which are better illustrated with a dump of each card. So, I’m a little unsure of how to move forward. Since it seems that blocks 16 - 19 are locked on the original card, I’ll have to find them through the sniff. However, I’m seeing discrepancies in the responses to the reader. If we break down the blocks by bytes: returned by each Tag Response in the sniff, we get the following table:
| Block | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 |
|-------------|-------------|-------------|-------------|-------------|----------------|-------------|---------------|-------------|---------------|-------------|---------------|-------------|-------------|-------------|---------------|-----------------|
| 4 Response | 06 0a 00 21 | 00 00 00 00 | 00 00 b2 22 | 33 72 4b b1 | e1 e2 N/A N/A | | | | | | | | | | | |
| 6 Response | | | 00 00 b2 22 | 33 72 4b b1 | 00 00 00 00 | b1 b2 12 93 | 93 3c N/A N/A | | | | | | | | | |
| 8 Response | | | | | 00 00 00 00 | b1 b2 12 93 | 69 4d 30 b2 | 4d b2 b2 b2 | 76 b5 N/A N/A | | | | | | | |
| 10 Response | | | | | | | 69 4d 30 b2 | 4d b2 b2 b2 | b2 b2 b2 b2 | b2 b2 b2 b2 | 43 25 N/A N/A | | | | | |
| 14 Response | | | | | | | | | | | b2 b2 b2 00 | 95 99 35 92 | 04 2f 3a 99 | 12 7a 59 85 | 66 9b N/A N/A | N/A N/A N/A N/A |
| 15 Response | | | | | | | | | | | | 95 99 35 92 | 04 2f 3a 99 | 12 7a 59 85 | b4 48 08 00 | 5d 46 N/A N/A |
It appears that the last two values in every response don’t match up to the corresponding first two values of their respective block. Is it possible these two values arent actually supposed to be the first two from a block, but some response code from the tag?
Any help with any of this would be greatly appreciated. The end goal here is to hopefully grab a FlexMN and clone the card onto their, but I want to get this sorted before even thinking about an order.