From the same manufacturer as the Serial Bluetooth Adapter - RS232, Long Range, here’s a review of the US Converters Serial WiFi Adapter - RS232 (P/N UCW232C):
[Okay, this one has been discontinued. But you can still get it on the cheap here, or get its replacement here. This review applies to both, as these devices basically work the same way]
What is it?
Same idea as with the bluetooth converter: if you use a serial RFID or NFC reader and you want to reduce cable clutter, but you want to connect to it through Wifi (if your computer doesn’t have bluetooth, say), this little guy is for you.
As with the bluetooth version, this review is focused on Linux. I don’t have Windows, sorry… But if you need to set it up under Windows, the setup is described extensively on the manufacturer’s website.
This device has the exact same form factor as its bluetooth sibling, and also comes in a small white cardboard box with a mini USB cable, a solder-on miniature Molex connector cable, a DB9 gender bender and a single page instruction sheet that will have you reach for the reading glasses. It too can be powered by 5V USB, 4.8 → 24V DC through pin 9 of the DB9 connector, or through the dedicated Molex connector.
Configuration
The device has a small switch on the side to select powering it through the USB port or externally. It also has two dip switches on the face to select whether you want it to draw power from pin 9 of the DB9, or send power to the pin. The latter option exists if you want to power your reader from the converter, but the current is limited to 100 mA. Not terribly useful in my opinion.
Beware that if you select the wrong combination of dip switches and send different voltages through the pin and through USB or through the Molex connector at the same time, you’ll zap the PCB, as explained in the manual.
However, the manual is wrong on one point: if you want to power the converter through the DB9 pin, the manual says you should leave both front face dip switches on the N/A position. This is incorrect: you need to enable the “In” dip switch, as well as the side power switch. Quite unnerving to have to discover that error by deliberately going against the stark warning printed in the manual.
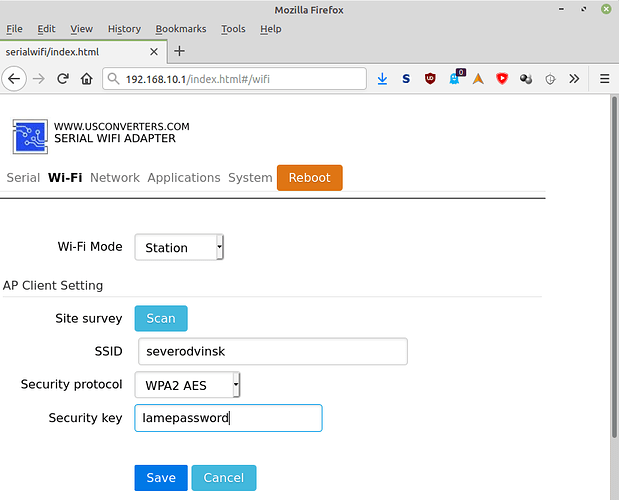
Software-wise, once you power up the device, it can be accessed as a Wifi access point: connect to it (password “12345678”) then go to the internal web server at 192.168.10.1. There, you can configure the device to connect to your own Wifi access point:
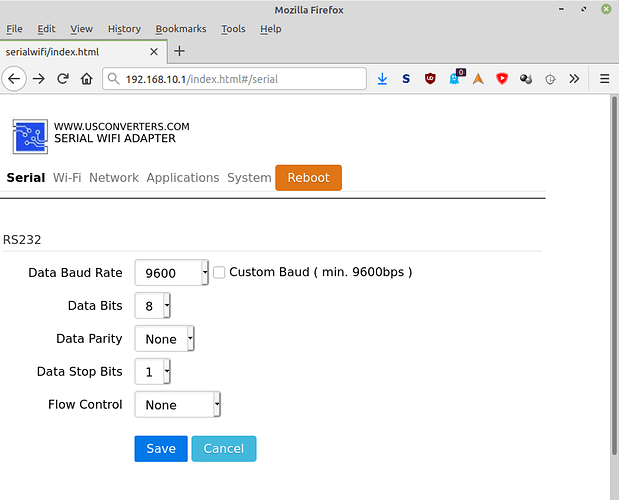
You can also set the serial port’s parameter, if 9600 8N1 doesn’t suit you:
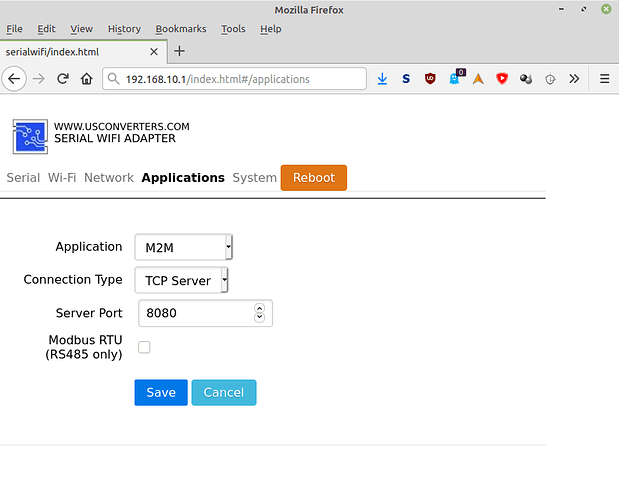
Finally, you can set the way you want the device to transfer the serial traffic. There are 3 options: TCP server (you connect to the device with a simple TCP connection), TCP client (the device connects to a simple TCP server of your choosing) and HTTP (the device sends data packets to an HTTP server using the GET or POST method).
Here I’m showing a screenshot of the TCP server method, which is what I’ll be using to configure the brige to a Linux machine (see below):
Once you’ve saved everything, click on reboot. Then reconnect your computer to your regular Wifi access point, and head to the IP you assigned to the device - which, at this point, should also have connected to your AP and either gotten its address through DHCP, or used the IP you configured manually:
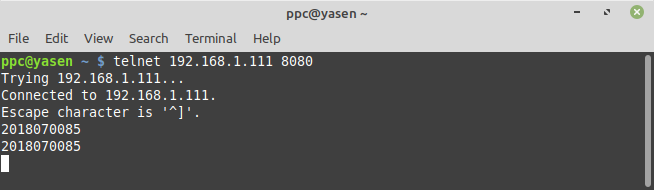
At this point, you should be able to see traffic. To test this, telnet to the device and port number you configured in the Application tab, and scan a few RFID cards: you should see them come through the telnet connection:
Now you can get the data through a simple TCP socket. That’s great if you have an application that can read/write RFID data through a TCP socket, but let’s face it: unless you code it yourself, that’s pretty unlikely ![]()
So now what you need to do is to configure your Linux box to create a fake serial port device file and bridge the data to/from the socket to/from that fake serial port.
Fortunately, there is a very versatile tool that can do exactly that, that’s included in almost all Unix distros since the beginning of time: socat.
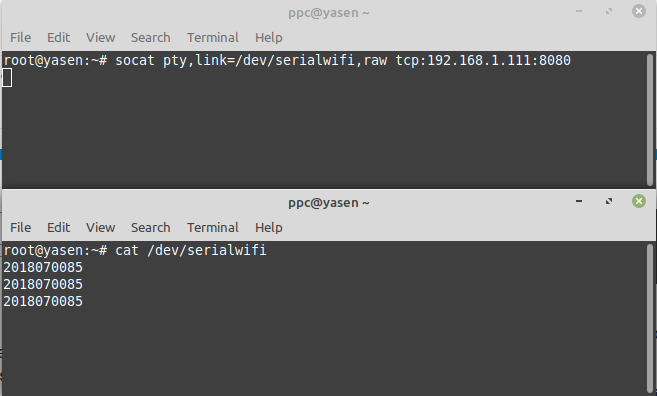
Try it as root on the command line in a separate console, then dump the newly created serial device file using the regular text cat in another console:
Great! Now you can create a fake serial device to access your serial reader from any serial-enabled application through the Wifi converter. But of course you want this to run at boot time, and reconnect automatically whenever the TCP connection drops for any reason.
To make that happen - assuming your Linux distro runs systemd (if it doesn’t, you’ll need to create a SystemV init script) - all you need to do is create a systemd service file that will automatically respawn socat in the background.
To do this , create the file /lib/systemd/system/serialwifi.service with the following content:
[Unit]
Description=Serial Wifi adapter virtual serial device
[Service]
Type=simple
ExecStart=/bin/bash -c 'HOST=192.18.1.111; PORT=8080; /usr/bin/socat pty,link=/dev/serialwifi,raw tcp:$HOST:$PORT & PID=$!; while [ 1 ]; do if ! /bin/ping -c1 -W1 $HOST 2> /dev/null >/dev/null; then /bin/kill $PID; break; fi; if ! /bin/ps -p $PID > /dev/null; then break; fi; /bin/sleep 1; done'
Restart=always
RestartSec=5
[Install]
WantedBy=multi-user.target
Then, as root, enable and start the service:
# systemctl enable serialwifi
# systemctl start serialwifi
Confirm that the /dev/serialwifi file has been created. Voila: your virtual serial link is ready.
Price:
$67.50 direct from the manufacturer [same price for the new revision], or €39 from the European distributor.
Verdict:
![]() No fuss, no nonsense network settings. It’s hard to do simpler.
No fuss, no nonsense network settings. It’s hard to do simpler.
![]() Wide range of power voltages
Wide range of power voltages
![]() Only draws 90 mA
Only draws 90 mA
![]() You can set up a pair of them as client-server to create a “wireless serial cable” without configuring anything
You can set up a pair of them as client-server to create a “wireless serial cable” without configuring anything
![]() Not too expensive
Not too expensive
![]() You can fry the device if you’re not careful. Just be careful… Once… It shouldn’t be too hard.
You can fry the device if you’re not careful. Just be careful… Once… It shouldn’t be too hard.