I just got off a call with Our Lord And Savior @Amal Graafstra ![]() and we have no idea what’s going on.
and we have no idea what’s going on.
@Amal the implant is giving a signal, I was wrong about it just giving off noise
TLDR
Three t5577s are non-functional, all in different ways. I don’t know if I got really unlucky, my proxmark is broken, or I broke them all.
Proxmark
I have a PM3 Easy, and the 2 t5577 cards I talk about came with it from DT
Here's the PM3 startup stuff if you want it
[=] Session log D:\ProxSpace\pm3/.proxmark3/logs/log_20210928.txt
[+] loaded from JSON file D:\ProxSpace\pm3/.proxmark3/preferences.json
[=] Using UART port com8
[=] Communicating with PM3 over USB-CDC
██████╗ ███╗ ███╗█████╗
██╔══██╗████╗ ████║╚═══██╗
██████╔╝██╔████╔██║ ████╔╝
██╔═══╝ ██║╚██╔╝██║ ╚══██╗
██║ ██║ ╚═╝ ██║█████╔╝
╚═╝ ╚═╝ ╚═╝╚════╝ [ Iceman ]
[ Proxmark3 RFID instrument ]
[ CLIENT ]
client: RRG/Iceman/master/v4.14434-14-g1850e9fa4 2021-09-28 17:11:53
compiled with MinGW-w64 10.3.0 OS:Windows (64b) ARCH:x86_64
[ PROXMARK3 ]
firmware.................. PM3 GENERIC
[ ARM ]
bootrom: RRG/Iceman/master/v4.14434-14-g1850e9fa4 2021-09-28 17:14:34
os: RRG/Iceman/master/v4.14434-14-g1850e9fa4 2021-09-28 17:15:16
compiled with GCC 10.1.0
[ FPGA ]
LF image built for 2s30vq100 on 2020-07-08 at 23:08:07
HF image built for 2s30vq100 on 2020-07-08 at 23:08:19
HF FeliCa image built for 2s30vq100 on 2020-07-08 at 23:08:30
[ Hardware ]
--= uC: AT91SAM7S512 Rev B
--= Embedded Processor: ARM7TDMI
--= Internal SRAM size: 64K bytes
--= Architecture identifier: AT91SAM7Sxx Series
--= Embedded flash memory 512K bytes ( 53% used )
[usb] pm3 --> hw tune
[=] ---------- Reminder ------------------------
[=] `hw tune` doesn't actively tune your antennas,
[=] it's only informative.
[=] Measuring antenna characteristics, please wait...
[/] 10
[=] ---------- LF Antenna ----------
[+] LF antenna: 24.47 V - 125.00 kHz
[+] LF antenna: 15.95 V - 134.83 kHz
[+] LF optimal: 26.90 V - 120.00 kHz
[+] Approx. Q factor (*): 6.8 by frequency bandwidth measurement
[+] Approx. Q factor (*): 7.8 by peak voltage measurement
[+] LF antenna is OK
[=] ---------- HF Antenna ----------
[+] HF antenna: 15.20 V - 13.56 MHz
[+] Approx. Q factor (*): 4.4 by peak voltage measurement
[+] HF antenna is OK
(*) Q factor must be measured without tag on the antenna
[+] Displaying LF tuning graph. Divisor 88 (blue) is 134.83 kHz, 95 (red) is 125.00 kHz.
Cards
I have an NExT and 2 t5577 test cards which do the following
Implant LF side
- (HF side works flawlessly)
- 300mV drop on lf tune
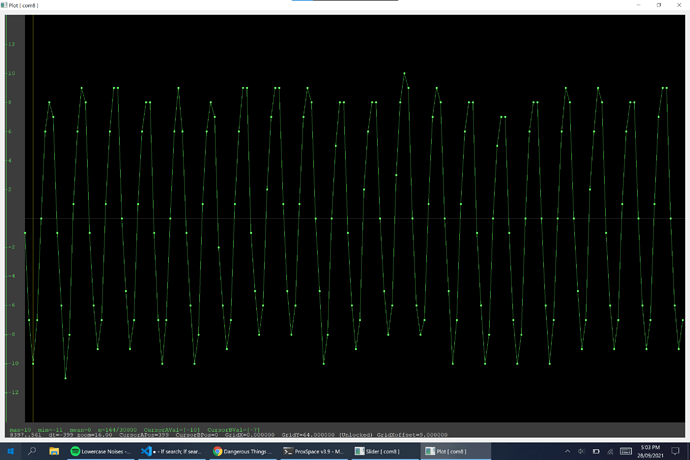
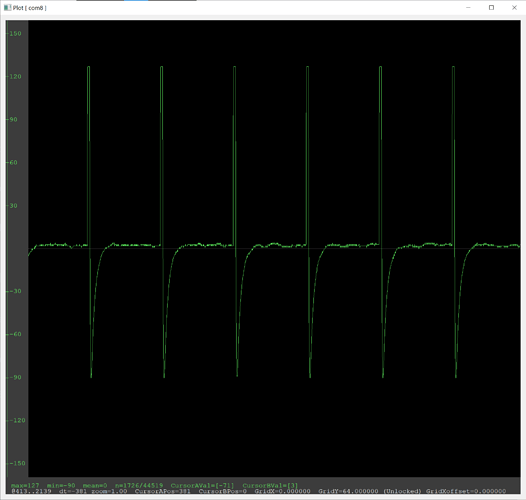
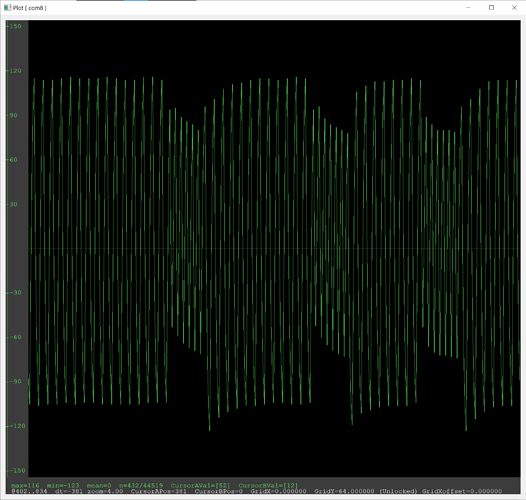
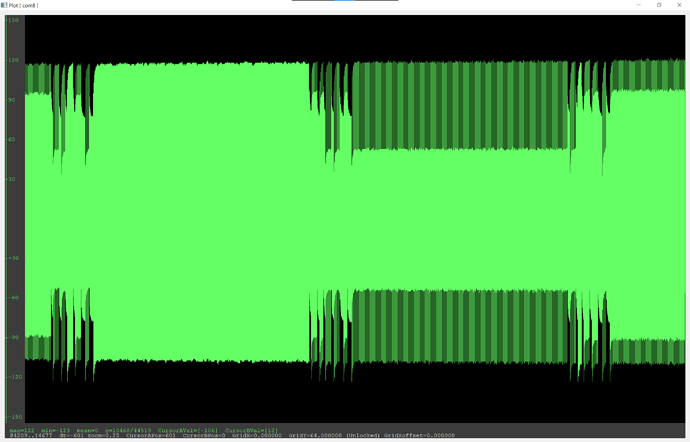
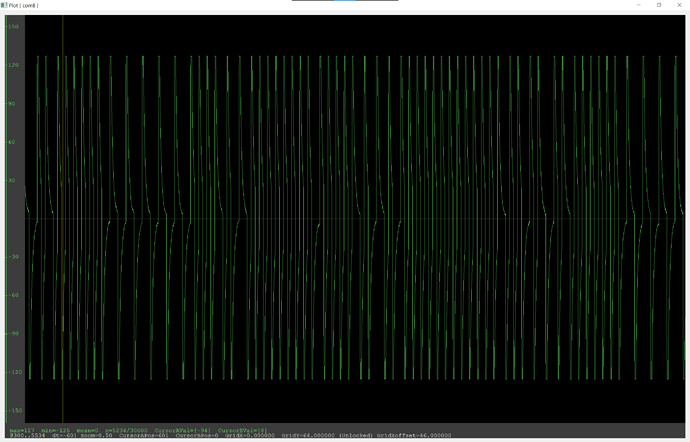
lf searchsaysNo known 125/134 kHz tags found! Couldn't identify a chipsetdata plotshows a repeating sin-like wave but it only peaks at around 15 units at best (120 for other cards)
Card A
- theoretically a t5577, from DT
lf searchfinds an Indala ID but it changes every time I scan (most likely an error) and doesn’t find any chipsetdata plotshows a repeating heartbeat-like pattern
Card B
- theoretically a t5577, from DT
lf searchdoesn’t find any tags, but does identify a t55xx chipset- I don’t really know how to describe this ones
data plot - the plot changes to what looks like an EM410x and back during an
ld search
Door card
- card from an LF access system
- Shows up as an EM410x
Tests
I’ve done everything on my NExT and the two t5577 cards
Card A
lf t5 detect
Says this only when the antenna is touching the card, but dump returns 00040004 for all blocks in page 0, and 096B2184 in page 1, and writes don’t work
[=] Chip type......... T55x7
[=] Modulation........ DIRECT/NRZ
[=] Bit rate.......... 1 - RF/16
[=] Inverted.......... No
[=] Offset............ 33
[=] Seq. terminator... No
[=] Block0............ 00040004 (auto detect)
[=] Downlink mode..... default/fixed bit length
[=] Password set...... No
lf t5 p1detect
Nothing
lf t5 info
Nothing
lf t5 brute -s 00000000 -e ffffffff
Succeeds on any password, saying:
[=] Chip type......... T55x7
[=] Modulation........ DIRECT/NRZ
[=] Bit rate.......... 1 - RF/16
[=] Inverted.......... No
[=] Offset............ 33
[=] Seq. terminator... No
[=] Block0............ 00040004 (auto detect)
[=] Downlink mode..... default/fixed bit length
[=] Password set...... Yes
[=] Password.......... 00000200
I think this is just because it’s reading 00040004 for the config block
Test mode
this with password 11111111, 00000000, and no password; and all those at different distances:
lf t5 write -b 0 -d 00107071 -p 11111111 -t
lf t5 wipe
lf em 41 clone --id 0F0368568B
lf search
No change.
Card B
lf t5 detect
Nope
lf t5 p1detect
[+] T55xx chip found! Downlink Mode used : default/fixed bit length
lf t5 info
Nothing
lf t5 brute -s 00000000 -e ffffffff
Nup
Test mode
Same script as before, tried alt passwords and different distances.
Nothing at all.
Implant
lf t5 detect
Nufin
lf t5 p1detect
Zilch
lf t5 info
literally nothing but a linefeed
lf t5 brute -s 00000000 -e ffffffff
Noop
Test mode
Same , and you guessed it, nothing.
Raw input/output
Script
lf t5 write -b 0 -d 00107071 -p 11111111 -t
lf t5 wipe
lf em 41 clone --id 0F0368568B
lf search
lf t5 write -b 0 -d 00107071 -p 00000000 -t
lf t5 wipe
lf em 41 clone --id 0F0368568B
lf search
lf t5 write -b 0 -d 00107071 -t
lf t5 wipe
lf em 41 clone --id 0F0368568B
lf search
lf t5 detect
lf t5 p1detect
lf t5 info
lf t5 recover
Card A (2cm)
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 11111111 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x11111111
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[+] Indala (len 118) Raw: 7ffffffffffffffffffffffffffffc00000200000002000000020000
[+] Valid Indala ID found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 00000000 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x00000000
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[+] Chipset detection: T55xx
[?] Hint: try `lf t55xx` commands
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -t
[=] Writing page 0 block: 00 data: 0x00107071
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[+] Indala (len 141) Raw: 80000000000000000000000000000bfffffdffffff02000000020000
[+] Valid Indala ID found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 --> lf t5 detect
[!] Could not detect modulation automatically. Try setting it manually with 'lf t55xx config'
[usb] pm3 --> lf t5 p1detect
[!] Could not detect modulation automatically. Try setting it manually with 'lf t55xx config'
[usb] pm3 --> lf t5 info
[usb] pm3 --> lf t5 recover
[=] press <Enter> to exit
[=] Trying password 00000001
[=] Trying password 00000002
[=] Trying password 00000004
[=] Trying password 00000008
[=] Trying password 00000010
[=] Trying password 00000020
[=] Trying password 00000040
[=] Trying password 00000080
[=] Trying password 00000100
[=] Trying password 00000200
[=] Trying password 00000400
[=] Trying password 00000800
[=] Trying password 00001000
[=] Trying password 00002000
[=] Trying password 00004000
[=] Trying password 00008000
[=] Trying password 00010000
[=] Trying password 00020000
[=] Trying password 00040000
[=] Trying password 00080000
[=] Trying password 00100000
[=] Trying password 00200000
[=] Trying password 00400000
[=] Trying password 00800000
[=] Trying password 01000000
[=] Trying password 02000000
[=] Trying password 04000000
[=] Trying password 08000000
[=] Trying password 10000000
[=] Trying password 20000000
[=] Trying password 40000000
[=] Trying password 80000000
[=] Trying password 00000000
[-] Recover password failed
[usb] pm3 -->
Card A (Touching)
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 11111111 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x11111111
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[+] Indala (len 173) Raw: 80000000000000000000000000003fefffefffefffeffdfffdfffdff
[+] Valid Indala ID found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 00000000 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x00000000
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[+] Indala (len 143) Raw: 80000000000000000000000000000ff7fff7fefffef0010001000100
[+] Valid Indala ID found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -t
[=] Writing page 0 block: 00 data: 0x00107071
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[+] Indala (len 187) Raw: 80000000000000000000000000007ffbfffbfffbfffbfffffefffeff
[+] Valid Indala ID found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 -->
[usb] pm3 --> lf t5 detect
[=] Chip type......... T55x7
[=] Modulation........ DIRECT/NRZ
[=] Bit rate.......... 1 - RF/16
[=] Inverted.......... No
[=] Offset............ 33
[=] Seq. terminator... No
[=] Block0............ 00040004 (auto detect)
[=] Downlink mode..... default/fixed bit length
[=] Password set...... No
[usb] pm3 --> lf t5 p1detect
[!] Could not detect modulation automatically. Try setting it manually with 'lf t55xx config'
[usb] pm3 --> lf t5 info
[=] --- T55x7 Configuration & Information ---------
[=] Safer key : 0
[=] reserved : 0
[=] Data bit rate : 1 - RF/16
[=] eXtended mode : No
[=] Modulation : 0 - DIRECT (ASK/NRZ)
[=] PSK clock frequency : 0 - RF/2
[=] AOR - Answer on Request : No
[=] OTP - One Time Pad : No
[=] Max block : 0
[=] Password mode : No
[=] Sequence Terminator : No
[=] Fast Write : Yes - Warning
[=] Inverse data : No
[=] POR-Delay : No
[=] -------------------------------------------------------------
[=] Raw Data - Page 0, block 0
[=] 00040004 - 00000000000001000000000000000100
[=] --- Fingerprint ------------
[usb] pm3 --> lf t5 recover
[=] press <Enter> to exit
[=] Trying password 00000001
[=] Chip type......... T55x7
[=] Modulation........ DIRECT/NRZ
[=] Bit rate.......... 1 - RF/16
[=] Inverted.......... No
[=] Offset............ 33
[=] Seq. terminator... No
[=] Block0............ 00040004 (auto detect)
[=] Downlink mode..... default/fixed bit length
[=] Password set...... Yes
[=] Password.......... 00000001
[+] Found valid password: [ 00000001 ]
Downlink Mode used : default/fixed bit length
[usb] pm3 -->
Card B
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 11111111 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x11111111
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[+] Chipset detection: T55xx
[?] Hint: try `lf t55xx` commands
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 00000000 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x00000000
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[+] Chipset detection: T55xx
[?] Hint: try `lf t55xx` commands
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -t
[=] Writing page 0 block: 00 data: 0x00107071
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[+] Chipset detection: T55xx
[?] Hint: try `lf t55xx` commands
[usb] pm3 -->
[usb] pm3 -->
[usb] pm3 --> lf t5 detect
[!] Could not detect modulation automatically. Try setting it manually with 'lf t55xx config'
[usb] pm3 --> lf t5 p1detect
[+] T55xx chip found!
Downlink Mode used : default/fixed bit length
[usb] pm3 --> lf t5 info
[usb] pm3 --> lf t5 recover
[=] press <Enter> to exit
[=] Trying password 00000001
[=] Trying password 00000002
[=] Trying password 00000004
[=] Trying password 00000008
[=] Trying password 00000010
[=] Trying password 00000020
[=] Trying password 00000040
[=] Trying password 00000080
[=] Trying password 00000100
[=] Trying password 00000200
[=] Trying password 00000400
[=] Trying password 00000800
[=] Trying password 00001000
[=] Trying password 00002000
[=] Trying password 00004000
[=] Trying password 00008000
[=] Trying password 00010000
[=] Trying password 00020000
[=] Trying password 00040000
[=] Trying password 00080000
[=] Trying password 00100000
[=] Trying password 00200000
[=] Trying password 00400000
[=] Trying password 00800000
[=] Trying password 01000000
[=] Trying password 02000000
[=] Trying password 04000000
[=] Trying password 08000000
[=] Trying password 10000000
[=] Trying password 20000000
[=] Trying password 40000000
[=] Trying password 80000000
[=] Trying password 00000000
[-] Recover password failed
[usb] pm3 -->
Implant
How are you reading this?! Well done, have a cookie ![]()
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 11111111 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x11111111
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -p 00000000 -t
[=] Writing page 0 block: 00 data: 0x00107071 pwd: 0x00000000
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 --> lf t5 write -b 0 -d 00107071 -t
[=] Writing page 0 block: 00 data: 0x00107071
[#] Using Test Mode
[usb] pm3 --> lf t5 wipe
[=] Target T55x7 tag
[=] Default configuration block 000880E0
[=] Begin wiping...
[=] Writing page 0 block: 00 data: 0x000880E0
[=] Writing page 0 block: 01 data: 0x00000000
[=] Writing page 0 block: 02 data: 0x00000000
[=] Writing page 0 block: 03 data: 0x00000000
[=] Writing page 0 block: 04 data: 0x00000000
[=] Writing page 0 block: 05 data: 0x00000000
[=] Writing page 0 block: 06 data: 0x00000000
[=] Writing page 0 block: 07 data: 0x00000000
[usb] pm3 --> lf em 41 clone --id 0F0368568B
[+] Preparing to clone EM4102 to T55x7 tag with EM Tag ID 0F0368568B (RF/64)
[#] Clock rate: 64
[#] Tag T55x7 written with 0xff83c03322a646e4
[+] Done
[?] Hint: try `lf em 410x reader` to verify
[usb] pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[-] No known 125/134 kHz tags found!
[=] Couldn't identify a chipset
[usb] pm3 -->
[usb] pm3 -->
[usb] pm3 --> lf t5 detect
[!] Could not detect modulation automatically. Try setting it manually with 'lf t55xx config'
[usb] pm3 --> lf t5 p1detect
[!] Could not detect modulation automatically. Try setting it manually with 'lf t55xx config'
[usb] pm3 --> lf t5 info
[usb] pm3 --> lf t5 recover
[=] press <Enter> to exit
[=] Trying password 00000001
[=] Trying password 00000002
[=] Trying password 00000004
[=] Trying password 00000008
[=] Trying password 00000010
[=] Trying password 00000020
[=] Trying password 00000040
[=] Trying password 00000080
[=] Trying password 00000100
[=] Trying password 00000200
[=] Trying password 00000400
[=] Trying password 00000800
[=] Trying password 00001000
[=] Trying password 00002000
[=] Trying password 00004000
[=] Trying password 00008000
[=] Trying password 00010000
[=] Trying password 00020000
[=] Trying password 00040000
[=] Trying password 00080000
[=] Trying password 00100000
[=] Trying password 00200000
[=] Trying password 00400000
[=] Trying password 00800000
[=] Trying password 01000000
[=] Trying password 02000000
[=] Trying password 04000000
[=] Trying password 08000000
[=] Trying password 10000000
[=] Trying password 20000000
[=] Trying password 40000000
[=] Trying password 80000000
[=] Trying password 00000000
[-] Recover password failed
[usb] pm3 -->
I’m very impressed you got here, but I’m suffering so you should too