I soft bricked mine doing just that, Android really really didn’t like the tag. Had to use some random 3rd party(non the usual) NFC app to get it to work. If I had a proxmark, I likely would’ve been able to fix it easier
I wonder if it has to do with write errors or being disconnected at the wrong time. You’d think an nfc tag is designed to handle being disconnected at any time. At least I thought so.
I think this is key, that a good coupling was made, but for whatever reason the user moved just enough to lose it and have only half data written to the tag, leaving android clueless as to whats in front of it. Especially with these x series tags, I feel like if I breathe wrong it will lose that coupling
You’re probably right there’s just one thing bothering me. Even if you have half an ndef writen the first “header” blocks are still unchanged. Sure android would be confused but apps like tag info which just dump the entire content should at least be able to read the first blocks and even dump the rest wether it makes sense or not. ![]() I might look into that, since I’m coding an nfc tool I’d like it to handle these edge cases
I might look into that, since I’m coding an nfc tool I’d like it to handle these edge cases
Ive got a proxmark easy on order dirct from DT I’ll have to learn it and try scanning again
Also, just for a quick fMi ( like a fyi but for me) what is meant when you say “coupling error” in newbie terms?
Loosing the connection with the implant. Ie. Not providing it enough power because the reader is too weak or moved during the process.
So i dont know if this will mean anything to anybody but…
Using my diag card from the kit, when i first open my phone the usual low low low HI pulse occurs UNTIL i start to move the card. Every movement results in a HI pulse of the led on the card. The same situation also occurs in NFC tools app however after a couple seconds the led is solid HI pulse. ![]()
I prefer “borked” for this term over “bricked” haha ![]() You can unbork some things… you can’t unbrick it.
You can unbork some things… you can’t unbrick it.
Sure android would be confused but apps like tag info which just dump the entire content should at least be able to read the first blocks and even dump the rest wether it makes sense or not.
Android has its way with your saucy little NFC tags well before any NFC apps get a shot at it… think of it like digital droit du seigneur. If the Android NFC stack shits the bed, your app never gets a chance. This is talked about somewhat in the long-winded post here;
TL;DR - The first batch of xSIID made December 2019 were formatted to try to use all 2k of memory across two 1k memory sectors for NFC applications, but the NFC stacks built into Android and iOS phones don’t know how to properly read multiple memory sectors in NFC Type 2 chips. Future batches are formatted to only use the first memory sector which is 1k for NFC applications. The remaining 1k is still readable and writable by phones, but only with a custom smartphone app that can directly address…
In most cases though, Android should not have a problem with a broken NDEF record… but in some instances it friggen borks hard.
Ahh so maybe when my proxmark comes in it’ll be operating on NOT andoird os but windows and then from there ill be able to fix the (possibly) broken NDEF? Or at least get an info dump.
There is a good possibility of this yes… no guarantees but I would say it’s likely fixable.
but in some instances it friggen borks hard
I’ve found success in trying multiple NFC apps and just continually writing to it until it finally works, wonder why eventually android decides to play nice
Can you install the nfc shell app?
https://play.google.com/store/apps/details?id=com.emutag.nfcshell
If you can no need to wait for proxmark to try ![]()
Also what phone is it.
Its a Galaxy S22 ultra. I have also tried NFC shell app. Again, no response from app or implant
Its almost definatly a coupling issue, get your phone use the read function so nfc is on and scanning and slowly (very slowly) move the phone around. Its one of the thing that you will have to get used to unfortunately, figuring out sweet spots
you will have to get used to unfortunately, figuring out sweet spots
Until you learn them if course
Then you’ll be tapping and rick rolling like a pro 1st time every time
![]()
Don’t forget to use you xFD to figure out where your NFC antenna is and the best orientation for implants
Ok ive got my pm3 setup what commands should i use to get the data you need for diagnosis?
prepare for ndef dump!
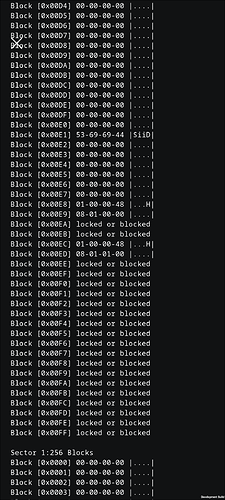
TYPE: NTAG I2C plus 1912bytes (NT3H2211FHK)
[+] Reading tag memory…
[!] Authentication Failed UL-EV1/NTAG
[=] MFU dump file information
[=] -------------------------------------------------------------
[=] Version… 00 04 04 05 02 02 15 03
[=] TBD 0… 00 00
[=] TBD 1… 00
[=] Signature… 40 85 E1 34 E0 30 53 84 66 79 3F D9 66 B3 17 60
[=] 5D 9A BF 00 05 6D AB 58 A4 A0 19 7D D1 CC 3A 62
[=] Counter 0… 00 00 00
[=] Tearing 0… 00
[=] Counter 1… 00 00 00
[=] Tearing 1… 00
[=] Counter 2… 00 00 00
[=] Tearing 2… 00
[=] Max data page… 232 ( 932 bytes )
[=] Header size… 56 bytes
[=] -------------------------------------------------------------
[=] block# | data |lck| ascii
[=] ---------±------------±–±-----
[=] 0/0x00 | 04 6E A2 D2 | | .n…
[=] 1/0x01 | CD 52 80 00 | | .R…
[=] 2/0x02 | 44 00 0F 00 | | D…
[=] 3/0x03 | E1 10 6D 00 | 1 | …m.
[=] 4/0x04 | 01 03 78 18 | 0 | …x.
[=] 5/0x05 | 77 02 03 7B | 0 | w…{
[=] 6/0x06 | 00 00 00 00 | 0 | …
[=] 7/0x07 | D8 00 00 00 | 0 | …
[=] 8/0x08 | FE 00 00 00 | 0 | …
[=] 9/0x09 | 65 3A 2F 2F | 0 | e://
[=] 10/0x0A | 2F 69 6E 74 | 0 | /int
[=] 11/0x0B | 65 72 6E 61 | 0 | erna
[=] 12/0x0C | 6C 20 73 74 | 0 | l st
[=] 13/0x0D | 6F 72 61 67 | 0 | orag
[=] 14/0x0E | 65 2F 44 6F | 0 | e/Do
[=] 15/0x0F | 77 6E 6C 6F | 0 | wnlo
[=] 16/0x10 | 61 64 2F 49 | 0 | ad/I
[=] 17/0x11 | 50 41 43 20 | 0 | PAC
[=] 18/0x12 | 53 65 70 61 | 0 | Sepa
[=] 19/0x13 | 72 61 74 69 | 0 | rati
[=] 20/0x14 | 6F 6E 73 20 | 0 | ons
[=] 21/0x15 | 43 68 65 63 | 0 | Chec
[=] 22/0x16 | 6B 6C 69 73 | 0 | klis
[=] 23/0x17 | 74 20 28 38 | 0 | t (8
[=] 24/0x18 | 20 4D 61 72 | 0 | Mar
[=] 25/0x19 | 20 32 33 29 | 0 | 23)
[=] 26/0x1A | 2E 64 6F 63 | 0 | .doc
[=] 27/0x1B | 78 FE 00 00 | 0 | x…
[=] 28/0x1C | 6F 75 20 55 | 0 | ou U
[=] 29/0x1D | 70 20 28 4F | 0 | p (O
[=] 30/0x1E | 66 66 69 63 | 0 | ffic
[=] 31/0x1F | 69 61 6C 20 | 0 | ial
[=] 32/0x20 | 4D 75 73 69 | 0 | Musi
[=] 33/0x21 | 63 20 56 69 | 0 | c Vi
[=] 34/0x22 | 64 65 6F 29 | 0 | deo)
[=] 35/0x23 | 22 20 6F 6E | 0 | " on
[=] 36/0x24 | 20 59 6F 75 | 0 | You
[=] 37/0x25 | 54 75 62 65 | 0 | Tube
[=] 38/0x26 | FE 00 00 00 | 0 | …
[=] 39/0x27 | 00 00 00 00 | 0 | …
[=] 40/0x28 | 00 00 00 00 | 0 | …
[=] 41/0x29 | 00 00 00 00 | 0 | …
[=] 42/0x2A | 00 00 00 00 | 0 | …
[=] 43/0x2B | 00 00 00 00 | 0 | …
[=] 44/0x2C | 00 00 00 00 | 0 | …
[=] 45/0x2D | 00 00 00 00 | 0 | …
[=] 46/0x2E | 00 00 00 00 | 0 | …
[=] 47/0x2F | 00 00 00 00 | 0 | …
[=] 48/0x30 | 00 00 00 00 | 0 | …
[=] 49/0x31 | 00 00 00 00 | 0 | …
[=] 50/0x32 | 00 00 00 00 | 0 | …
[=] 51/0x33 | 00 00 00 00 | 0 | …
[=] 52/0x34 | 00 00 00 00 | 0 | …
[=] 53/0x35 | 00 00 00 00 | 0 | …
[=] 54/0x36 | 00 00 00 00 | 0 | …
[=] 55/0x37 | 00 00 00 00 | 0 | …
[=] 56/0x38 | 00 00 00 00 | 0 | …
[=] 57/0x39 | 00 00 00 00 | 0 | …
[=] 58/0x3A | 00 00 00 00 | 0 | …
[=] 59/0x3B | 00 00 00 00 | 0 | …
[=] 60/0x3C | 00 00 00 00 | 0 | …
[=] 61/0x3D | 00 00 00 00 | 0 | …
[=] 62/0x3E | 00 00 00 00 | 0 | …
[=] 63/0x3F | 00 00 00 00 | 0 | …
[=] 64/0x40 | 00 00 00 00 | 0 | …
[=] 65/0x41 | 00 00 00 00 | 0 | …
[=] 66/0x42 | 00 00 00 00 | 0 | …
[=] 67/0x43 | 00 00 00 00 | 0 | …
[=] 68/0x44 | 00 00 00 00 | 0 | …
[=] 69/0x45 | 00 00 00 00 | 0 | …
[=] 70/0x46 | 00 00 00 00 | 0 | …
[=] 71/0x47 | 00 00 00 00 | 0 | …
[=] 72/0x48 | 00 00 00 00 | 0 | …
[=] 73/0x49 | 00 00 00 00 | 0 | …
[=] 74/0x4A | 00 00 00 00 | 0 | …
[=] 75/0x4B | 00 00 00 00 | 0 | …
[=] 76/0x4C | 00 00 00 00 | 0 | …
[=] 77/0x4D | 00 00 00 00 | 0 | …
[=] 78/0x4E | 00 00 00 00 | 0 | …
[=] 79/0x4F | 00 00 00 00 | 0 | …
[=] 80/0x50 | 00 00 00 00 | 0 | …
[=] 81/0x51 | 00 00 00 00 | 0 | …
[=] 82/0x52 | 00 00 00 00 | 0 | …
[=] 83/0x53 | 00 00 00 00 | 0 | …
[=] 84/0x54 | 00 00 00 00 | 0 | …
[=] 85/0x55 | 00 00 00 00 | 0 | …
[=] 86/0x56 | 00 00 00 00 | 0 | …
[=] 87/0x57 | 00 00 00 00 | 0 | …
[=] 88/0x58 | 00 00 00 00 | 0 | …
[=] 89/0x59 | 00 00 00 00 | 0 | …
[=] 90/0x5A | 00 00 00 00 | 0 | …
[=] 91/0x5B | 00 00 00 00 | 0 | …
[=] 92/0x5C | 00 00 00 00 | 0 | …
[=] 93/0x5D | 00 00 00 00 | 0 | …
[=] 94/0x5E | 00 00 00 00 | 0 | …
[=] 95/0x5F | 00 00 00 00 | 0 | …
[=] 96/0x60 | 00 00 00 00 | 0 | …
[=] 97/0x61 | 00 00 00 00 | 0 | …
[=] 98/0x62 | 00 00 00 00 | 0 | …
[=] 99/0x63 | 00 00 00 00 | 0 | …
[=] 100/0x64 | 00 00 00 00 | 0 | …
[=] 101/0x65 | 00 00 00 00 | 0 | …
[=] 102/0x66 | 00 00 00 00 | 0 | …
[=] 103/0x67 | 00 00 00 00 | 0 | …
[=] 104/0x68 | 00 00 00 00 | 0 | …
[=] 105/0x69 | 00 00 00 00 | 0 | …
[=] 106/0x6A | 00 00 00 00 | 0 | …
[=] 107/0x6B | 00 00 00 00 | 0 | …
[=] 108/0x6C | 00 00 00 00 | 0 | …
[=] 109/0x6D | 00 00 00 00 | 0 | …
[=] 110/0x6E | 00 00 00 00 | 0 | …
[=] 111/0x6F | 00 00 00 00 | 0 | …
[=] 112/0x70 | 00 00 00 00 | 0 | …
[=] 113/0x71 | 00 00 00 00 | 0 | …
[=] 114/0x72 | 00 00 00 00 | 0 | …
[=] 115/0x73 | 00 00 00 00 | 0 | …
[=] 116/0x74 | 00 00 00 00 | 0 | …
[=] 117/0x75 | 00 00 00 00 | 0 | …
[=] 118/0x76 | 00 00 00 00 | 0 | …
[=] 119/0x77 | 00 00 00 00 | 0 | …
[=] 120/0x78 | 00 00 00 00 | 0 | …
[=] 121/0x79 | 00 00 00 00 | 0 | …
[=] 122/0x7A | 00 00 00 00 | 0 | …
[=] 123/0x7B | 00 00 00 00 | 0 | …
[=] 124/0x7C | 00 00 00 00 | 0 | …
[=] 125/0x7D | 00 00 00 00 | 0 | …
[=] 126/0x7E | 00 00 00 00 | 0 | …
[=] 127/0x7F | 00 00 00 00 | 0 | …
[=] 128/0x80 | 00 00 00 00 | 0 | …
[=] 129/0x81 | 00 00 00 00 | 0 | …
[=] 130/0x82 | 00 00 00 00 | 0 | …
[=] 131/0x83 | 00 00 00 00 | 0 | …
[=] 132/0x84 | 00 00 00 00 | 0 | …
[=] 133/0x85 | 00 00 00 00 | 0 | …
[=] 134/0x86 | 00 00 00 00 | 0 | …
[=] 135/0x87 | 00 00 00 00 | 0 | …
[=] 136/0x88 | 00 00 00 00 | 0 | …
[=] 137/0x89 | 00 00 00 00 | 0 | …
[=] 138/0x8A | 00 00 00 00 | 0 | …
[=] 139/0x8B | 00 00 00 00 | 0 | …
[=] 140/0x8C | 00 00 00 00 | 0 | …
[=] 141/0x8D | 00 00 00 00 | 0 | …
[=] 142/0x8E | 00 00 00 00 | 0 | …
[=] 143/0x8F | 00 00 00 00 | 0 | …
[=] 144/0x90 | 00 00 00 00 | 0 | …
[=] 145/0x91 | 00 00 00 00 | 0 | …
[=] 146/0x92 | 00 00 00 00 | 0 | …
[=] 147/0x93 | 00 00 00 00 | 0 | …
[=] 148/0x94 | 00 00 00 00 | 0 | …
[=] 149/0x95 | 00 00 00 00 | 0 | …
[=] 150/0x96 | 00 00 00 00 | 0 | …
[=] 151/0x97 | 00 00 00 00 | 0 | …
[=] 152/0x98 | 00 00 00 00 | 0 | …
[=] 153/0x99 | 00 00 00 00 | 0 | …
[=] 154/0x9A | 00 00 00 00 | 0 | …
[=] 155/0x9B | 00 00 00 00 | 0 | …
[=] 156/0x9C | 00 00 00 00 | 0 | …
[=] 157/0x9D | 00 00 00 00 | 0 | …
[=] 158/0x9E | 00 00 00 00 | 0 | …
[=] 159/0x9F | 00 00 00 00 | 0 | …
[=] 160/0xA0 | 00 00 00 00 | 0 | …
[=] 161/0xA1 | 00 00 00 00 | 0 | …
[=] 162/0xA2 | 00 00 00 00 | 0 | …
[=] 163/0xA3 | 00 00 00 00 | 0 | …
[=] 164/0xA4 | 00 00 00 00 | 0 | …
[=] 165/0xA5 | 00 00 00 00 | 0 | …
[=] 166/0xA6 | 00 00 00 00 | 0 | …
[=] 167/0xA7 | 00 00 00 00 | 0 | …
[=] 168/0xA8 | 00 00 00 00 | 0 | …
[=] 169/0xA9 | 00 00 00 00 | 0 | …
[=] 170/0xAA | 00 00 00 00 | 0 | …
[=] 171/0xAB | 00 00 00 00 | 0 | …
[=] 172/0xAC | 00 00 00 00 | 0 | …
[=] 173/0xAD | 00 00 00 00 | 0 | …
[=] 174/0xAE | 00 00 00 00 | 0 | …
[=] 175/0xAF | 00 00 00 00 | 0 | …
[=] 176/0xB0 | 00 00 00 00 | 0 | …
[=] 177/0xB1 | 00 00 00 00 | 0 | …
[=] 178/0xB2 | 00 00 00 00 | 0 | …
[=] 179/0xB3 | 00 00 00 00 | 0 | …
[=] 180/0xB4 | 00 00 00 00 | 0 | …
[=] 181/0xB5 | 00 00 00 00 | 0 | …
[=] 182/0xB6 | 00 00 00 00 | 0 | …
[=] 183/0xB7 | 00 00 00 00 | 0 | …
[=] 184/0xB8 | 00 00 00 00 | 0 | …
[=] 185/0xB9 | 00 00 00 00 | 0 | …
[=] 186/0xBA | 00 00 00 00 | 0 | …
[=] 187/0xBB | 00 00 00 00 | 0 | …
[=] 188/0xBC | 00 00 00 00 | 0 | …
[=] 189/0xBD | 00 00 00 00 | 0 | …
[=] 190/0xBE | 00 00 00 00 | 0 | …
[=] 191/0xBF | 00 00 00 00 | 0 | …
[=] 192/0xC0 | 00 00 00 00 | 0 | …
[=] 193/0xC1 | 00 00 00 00 | 0 | …
[=] 194/0xC2 | 00 00 00 00 | 0 | …
[=] 195/0xC3 | 00 00 00 00 | 0 | …
[=] 196/0xC4 | 00 00 00 00 | 0 | …
[=] 197/0xC5 | 00 00 00 00 | 0 | …
[=] 198/0xC6 | 00 00 00 00 | 0 | …
[=] 199/0xC7 | 00 00 00 00 | 0 | …
[=] 200/0xC8 | 00 00 00 00 | 0 | …
[=] 201/0xC9 | 00 00 00 00 | 0 | …
[=] 202/0xCA | 00 00 00 00 | 0 | …
[=] 203/0xCB | 00 00 00 00 | 0 | …
[=] 204/0xCC | 00 00 00 00 | 0 | …
[=] 205/0xCD | 00 00 00 00 | 0 | …
[=] 206/0xCE | 00 00 00 00 | 0 | …
[=] 207/0xCF | 00 00 00 00 | 0 | …
[=] 208/0xD0 | 00 00 00 00 | 0 | …
[=] 209/0xD1 | 00 00 00 00 | 0 | …
[=] 210/0xD2 | 00 00 00 00 | 0 | …
[=] 211/0xD3 | 00 00 00 00 | 0 | …
[=] 212/0xD4 | 00 00 00 00 | 0 | …
[=] 213/0xD5 | 00 00 00 00 | 0 | …
[=] 214/0xD6 | 00 00 00 00 | 0 | …
[=] 215/0xD7 | 00 00 00 00 | 0 | …
[=] 216/0xD8 | 00 00 00 00 | 0 | …
[=] 217/0xD9 | 00 00 00 00 | 0 | …
[=] 218/0xDA | 00 00 00 00 | 0 | …
[=] 219/0xDB | 00 00 00 00 | 0 | …
[=] 220/0xDC | 00 00 00 00 | 0 | …
[=] 221/0xDD | 00 00 00 00 | 0 | …
[=] 222/0xDE | 00 00 00 00 | 0 | …
[=] 223/0xDF | 00 00 00 00 | 0 | …
[=] 224/0xE0 | 00 00 00 00 | 0 | …
[=] 225/0xE1 | 53 69 69 44 | 0 | SiiD
[=] 226/0xE2 | 00 00 FF 00 | 0 | …
[=] 227/0xE3 | 00 00 00 E2 | 0 | …
[=] 228/0xE4 | 00 00 00 00 | 0 | …
[=] 229/0xE5 | 00 00 00 00 | 0 | …
[=] 230/0xE6 | 00 00 00 00 | 0 | …
[=] 231/0xE7 | 00 00 00 00 | 0 | …
[=] 232/0xE8 | 01 00 F8 48 | 0 | …H
[=] 233/0xE9 | 00 00 00 00 | 0 | …
[=] ---------------------------------
Your E2-E3 and E8-E9 are different from mine
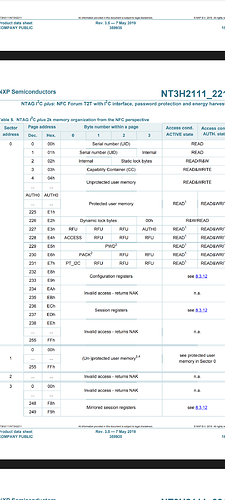
It says these blocks are “Dynamic lock bytes” and “Configuration Registers”.
o
Documentation
Maybe that’s it?
My E2 is the same 0000FF00 and my XSIID scans fine, and AUTH0 only locks blocks after it, setting it to E2 wouldn’t affect the user data area, just the end config bytes
I would probably try manually writing blocks to a known good NDEF record, if you can get a good coupling with the PM3 or the NFC Shell app
Starting in block 4 the stock DT link NDEF hex is:
00000000
00000000
0000031F
D1011B55
03666F72
756D2E64
616E6765
726F7573
7468696E
67732E63
6F6D2FFE
I would also probably just zero out the rest of your original NDEF record (Set blocks 0x04-0x25 to 00000000 before writing the above)