ayeosq
February 6, 2025, 2:15am
1
This my hardware info
[ Proxmark3 RFID instrument ]
MCU....... AT91SAM7S512 Rev A
Memory.... 512 KB ( 66% used )
Client.... Iceman/master/v4.19552-324-g1f07e818e 2025-02-05 22:09:51
Bootrom... Iceman/master/v4.19552-324-g1f07e818e-suspect 2025-02-05 22:07:49
OS........ Iceman/master/v4.19552-324-g1f07e818e-suspect 2025-02-05 22:08:25
Target.... PM3 GENERIC
This is what I get from info:
[=] --- Tag Information ----------------------------------------
[+] CSN: B2 4A E4 01 F9 FF 12 E0 uid
[+] Config: 12 FF FF FF 7F 1F FF 3C card configuration
[+] E-purse: FF FF FF FF 01 FD FF FF Card challenge, CC
[+] Kd: 00 00 00 00 00 00 00 00 debit key ( hidden )
[+] Kc: 00 00 00 00 00 00 00 00 credit key ( hidden )
[+] AIA: FF FF FF FF FF FF FF FF application issuer area
[=] -------------------- Card configuration --------------------
[=] Raw... 12 FF FF FF 7F 1F FF 3C
[=] 12 ( 18 )............. app limit
[=] FFFF ( 65535 )...... OTP
[=] FF............ block write lock
[=] 7F......... chip
[=] 1F...... mem
[=] FF... EAS
[=] 3C fuses
[=] Fuses:
[+] mode......... Application (locked)
[+] coding....... ISO 14443-2 B / 15693
[+] crypt........ Secured page, keys not locked
[=] RA........... Read access not enabled
[=] PROD0/1...... Default production fuses
[=] -------------------------- Memory --------------------------
[=] 2 KBits/2 App Areas ( 256 bytes )
[=] 1 books / 1 pages
[=] First book / first page configuration
[=] Config | 0 - 5 ( 0x00 - 0x05 ) - 6 blocks
[=] AA1 | 6 - 18 ( 0x06 - 0x12 ) - 13 blocks
[=] AA2 | 19 - 31 ( 0x13 - 0x1F ) - 18 blocks
[=] ------------------------- KeyAccess ------------------------
[=] * Kd, Debit key, AA1 Kc, Credit key, AA2 *
[=] Read AA1..... debit
[=] Write AA1.... debit
[=] Read AA2..... credit
[=] Write AA2.... credit
[=] Debit........ debit or credit
[=] Credit....... credit
[=] ------------------------ Fingerprint -----------------------
[+] CSN.......... HID range
[+] Credential... iCLASS legacy
[+] Card type.... PicoPass 2K
[+] Card chip.... NEW Silicon (No 14b support)
Below are my chk with default keys and elite keys, no keys found
[usb] pm3 --> hf iclass chk -f
[+] Loaded 29 keys from dictionary file `C:\Users\User\Downloads\ProxSpace\ProxSpace\pm3\proxmark3\client\dictionaries\iclass_default_keys.dic`
[+] Reading tag CSN / CCNR...
[+] CSN: B2 4A E4 01 F9 FF 12 E0
[+] CCNR: FF FF FF FF 01 FD FF FF 00 00 00 00
[=] Generating diversified keys
[+] Searching for DEBIT key...
[\]Chunk [000/29]
[+] time in iclass chk 1.0 seconds
[usb] pm3 --> hf iclass chk -f C:\Users\User\Downloads\ProxSpace\ProxSpace\pm3\proxmark3\client\dictionaries\iclass_elite_keys.dic --elite
[+] Loaded 729 keys from dictionary file `C:\Users\User\Downloads\ProxSpace\ProxSpace\pm3\proxmark3\client\dictionaries\iclass_elite_keys.dic`
[+] Reading tag CSN / CCNR...
[+] CSN: B2 4A E4 01 F9 FF 12 E0
[+] CCNR: FF FF FF FF 01 FD FF FF 00 00 00 00
[=] Generating diversified keys using elite algo
[+] Searching for DEBIT key...
[-]Chunk [127/729]
[+] Found valid key XX XX XX XX XX XX XX XX
[+] time in iclass chk 4.5 seconds
[+] Key already at keyslot 4
[?] Try `hf iclass managekeys -p` to view keys
This is what I get from dump:
[usb] pm3 --> hf iclass dump --ki 0
[+] Using AA1 (debit) key[0] AE A6 84 A6 DA B2 32 78
[=] Card has at least 2 application areas. AA1 limit 18 (0x12) AA2 limit 31 (0x1F)
.
[!!] failed to communicate with card
[usb] pm3 --> hf iclass dump --ki 1
[+] Using AA1 (debit) key[1] FD CB 5A 52 EA 8F 30 90
[=] Card has at least 2 application areas. AA1 limit 18 (0x12) AA2 limit 31 (0x1F)
.
[!!] failed to communicate with card
[usb] pm3 --> hf iclass dump --ki 2
[+] Using AA1 (debit) key[2] F0 E1 D2 C3 B4 A5 96 87
[=] Card has at least 2 application areas. AA1 limit 18 (0x12) AA2 limit 31 (0x1F)
.
[!!] failed to communicate with card
Can I get some help here on what I missed out?
Else I guess, I have to get near a physical reader to find the custom key: Running a LOCLASS attack on a reader on site and using a valid know CSN
ayeosq
February 6, 2025, 3:14am
3
This is what I get from info:
[=] --- Tag Information ----------------------------------------
[+] CSN: B2 4A E4 01 F9 FF 12 E0 uid
[+] Config: 12 FF FF FF 7F 1F FF 3C card configuration
[+] E-purse: FF FF FF FF 01 FD FF FF Card challenge, CC
[+] Kd: 00 00 00 00 00 00 00 00 debit key ( hidden )
[+] Kc: 00 00 00 00 00 00 00 00 credit key ( hidden )
[+] AIA: FF FF FF FF FF FF FF FF application issuer area
[=] -------------------- Card configuration --------------------
[=] Raw... 12 FF FF FF 7F 1F FF 3C
[=] 12 ( 18 )............. app limit
[=] FFFF ( 65535 )...... OTP
[=] FF............ block write lock
[=] 7F......... chip
[=] 1F...... mem
[=] FF... EAS
[=] 3C fuses
[=] Fuses:
[+] mode......... Application (locked)
[+] coding....... ISO 14443-2 B / 15693
[+] crypt........ Secured page, keys not locked
[=] RA........... Read access not enabled
[=] PROD0/1...... Default production fuses
[=] -------------------------- Memory --------------------------
[=] 2 KBits/2 App Areas ( 256 bytes )
[=] 1 books / 1 pages
[=] First book / first page configuration
[=] Config | 0 - 5 ( 0x00 - 0x05 ) - 6 blocks
[=] AA1 | 6 - 18 ( 0x06 - 0x12 ) - 13 blocks
[=] AA2 | 19 - 31 ( 0x13 - 0x1F ) - 18 blocks
[=] ------------------------- KeyAccess ------------------------
[=] * Kd, Debit key, AA1 Kc, Credit key, AA2 *
[=] Read AA1..... debit
[=] Write AA1.... debit
[=] Read AA2..... credit
[=] Write AA2.... credit
[=] Debit........ debit or credit
[=] Credit....... credit
[=] ------------------------ Fingerprint -----------------------
[+] CSN.......... HID range
[+] Credential... iCLASS legacy
[+] Card type.... PicoPass 2K
[+] Card chip.... NEW Silicon (No 14b support)
Below are my chk with default keys and elite keys:
[usb] pm3 --> hf iclass chk -f
[+] Loaded 29 keys from dictionary file `C:\Users\User\Downloads\ProxSpace\ProxSpace\pm3\proxmark3\client\dictionaries\iclass_default_keys.dic`
[+] Reading tag CSN / CCNR...
[+] CSN: B2 4A E4 01 F9 FF 12 E0
[+] CCNR: FF FF FF FF 01 FD FF FF 00 00 00 00
[=] Generating diversified keys
[+] Searching for DEBIT key...
[\]Chunk [000/29]
[+] time in iclass chk 1.0 seconds
[usb] pm3 --> hf iclass chk -f C:\Users\User\Downloads\ProxSpace\ProxSpace\pm3\proxmark3\client\dictionaries\iclass_elite_keys.dic --elite
[+] Loaded 729 keys from dictionary file `C:\Users\User\Downloads\ProxSpace\ProxSpace\pm3\proxmark3\client\dictionaries\iclass_elite_keys.dic`
[+] Reading tag CSN / CCNR...
[+] CSN: B2 4A E4 01 F9 FF 12 E0
[+] CCNR: FF FF FF FF 01 FD FF FF 00 00 00 00
[=] Generating diversified keys using elite algo
[+] Searching for DEBIT key...
[-]Chunk [127/729]
[+] Found valid key XX XX XX XX XX XX XX XX
[+] time in iclass chk 4.5 seconds
[+] Key already at keyslot 4
[?] Try `hf iclass managekeys -p` to view keys
This is what I get from dump:
[usb] pm3 --> hf iclass dump --ki 4 --elite
[+] Using AA1 (debit) key[4] xx
[=] Card has at least 2 application areas. AA1 limit 18 (0x12) AA2 limit 31 (0x1F)
.
[=] --------------------------- Tag memory ----------------------------
[=] block# | data | ascii |lck| info
[=] ---------+-------------------------+----------+---+----------------
[=] 0/0x00 | B2 4A E4 01 F9 FF 12 E0 | .J...... | | CSN
[=] 1/0x01 | 12 FF FF FF 7F 1F FF 3C | .......< | | Config
[=] 2/0x02 | FF FF FF FF 01 FD FF FF | ........ | | E-purse
[=] 3/0x03 | 47 91 1F FC DE FA 68 11 | G.....h. | | Debit
[=] 4/0x04 | FF FF FF FF FF FF FF FF | ........ | | Credit
[=] 5/0x05 | FF FF FF FF FF FF FF FF | ........ | | AIA
[=] 6/0x06 | 03 03 03 03 00 03 E0 17 | ........ | | User / HID CFG
[=] 7/0x07 | E7 D2 3D 7E 3A C7 A9 1A | ..=~:... | | User / Enc Cred
[=] 8/0x08 | 2A D4 C8 21 1F 99 68 71 | *..!..hq | | User / Enc Cred
[=] 9/0x09 | 2A D4 C8 21 1F 99 68 71 | *..!..hq | | User / Enc Cred
[=] 10/0x0A | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 11/0x0B | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 12/0x0C | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 13/0x0D | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 14/0x0E | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 15/0x0F | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 16/0x10 | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 17/0x11 | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] 18/0x12 | 3A 66 BD BD 5A 17 74 4B | :f..Z.tK | | User
[=] ---------+-------------------------+----------+---+----------------
[?] yellow = legacy credential
[+] saving dump file - 19 blocks read
[+] Saved 152 bytes to binary file `xx.bin`
[+] Saved to json file `xx.json`
[?] Try `hf iclass decrypt -f` to decrypt dump file
[?] Try `hf iclass view -f` to view dump file
Whats next to copy to a blank?
1 Like
ayeosq
February 6, 2025, 3:15am
4
Updated, was looking at what I was missing out and edited the post. Now able to get the key.
1 Like
hf iclass encode --w H10301 --fc 28 --cn 53451 --ki <key index for blank, probably 0>
Then try your card, if it doesn’t work then your reader system might not support default keying, and you’ll need someone smarter than me to walk you through changing the keys on the blank
ayeosq
February 6, 2025, 4:15am
6
that work, how did you get the card number?
1 Like
This block:[=] 7/0x07 | E7 D2 3D 7E 3A C7 A9 1A | ..=~:... | | User / Enc Cred
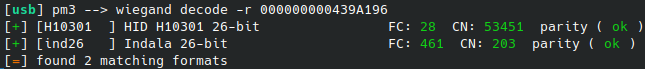
You can use hf iclass decrypt -d E7D23D7E3AC7A91A to get a look at the proper hex: 000000000439A196
And finally a wiegand decode -r 000000000439A196 will try to decode that into the actual credential data if it’s a known format, which it is in this case
ayeosq
February 6, 2025, 6:44am
8
Can’t seem to get the cn and fc
[usb] pm3 --> hf iclass decrypt -d E7D23D7E3AC7A91A
[+] Loaded 16 bytes from binary file `iclass_decryptionkey.bin`
[+] encrypted... E7D23D7E3AC7A91A
[+] plain....... 000000000439A196
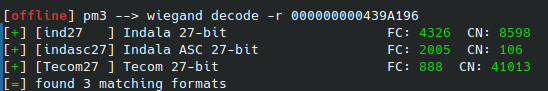
[usb] pm3 --> wiegand decode -r 000000000439A196
[+] [ind27 ] Indala 27-bit FC: 4326 CN: 8598
[+] [indasc27] Indala ASC 27-bit FC: 2005 CN: 106
[+] [Tecom27 ] Tecom 27-bit FC: 888 CN: 41013
[=] found 3 matching formats
Do I actually need to do these generate XOR keys, read block and write block mentioned in https://forum.dangerousthings.com/t/so-you-want-to-implant-an-hid-card/14180/2 ?
I have no idea why that command would decode it weird for you, it shouldn’t be related to the iClass keys at all, wiegand isn’t related to the card type at all
ayeosq
February 6, 2025, 7:20am
10
Still can’t get what you get.
Wonder why others had those other steps, what do they do:https://forum.dangerousthings.com/t/need-help-cloning-hid-iclass-legacy/16334/16
There’s some good info on the different key types and things like that in this thread from a few days ago:
So, I have seen many different post giving hints, recommendations, asking questions, and so on, for how to clone an HID iCLASS DY card. It seems to be the typical choice for a varieties of universities out there. After some months, and much silliness, I have gotten a reliable system down, so I have decided to write a guide. Millage may vary. Also, I am not an expert. This is my first RFID project ever, but I did get it to work, and hope you will too!
First step, buy a Proxmark 3 Easy, found her…
I’m not totally familiar with that part of iClass, I believe it comes back to:
Either way, the wiegand decode command does not care about iclass in any way
Upon updating my PM3 client to the latest source, I get the same decode as you:
This appears to be a bug, as I can confirm that when I copy the same block 7 data to a test card, both hf iclass info and my testing HID MultiClass Reader both report the H10301 credential from my original decode
2 Likes
Iceman
February 6, 2025, 8:46am
12
there is a known bug in the wiegand decoder atm…
3 Likes
ayeosq
March 1, 2025, 3:57am
13
The correct decode happens when I did a:
[usb] pm3 --> hf iclass decrypt -f XXXX.XXX
[=] ------------------------ Block 7 decoder --------------------------
[+] Binary... 27 - 100001110011010000110010110
[+] [ind27 ] Indala 27-bit FC: 4326 CN: 8598
[+] [indasc27] Indala ASC 27-bit FC: 2005 CN: 106
[+] [Tecom27 ] Tecom 27-bit FC: 888 CN: 41013
[=] found 3 matching 27-bit formats
[=] Trying without a preamble bit...
[+] [H10301 ] HID H10301 26-bit FC: 28 CN: 53451 parity ( ok )
[+] [ind26 ] Indala 26-bit FC: 461 CN: 203 parity ( ok )
[=] found 2 matching 26-bit formats
[=] -------------------------------------------------------------------
1 Like
Iceman
March 2, 2025, 5:55am
14
Some community fixes was merged, enjoy!
4 Likes