Last November I got this implant NXP - Mifare Ultralight (Ultralight C). I immediately loved it. I’ve been using NFC tools pro to write tasks on it. However today, after a couple of conditional tasks I added, it stopped working and it doesn’t accept writing anymore. I did always used a condition and an end of the condition, so I wouldn’t get in trouble.
Somehow it seems to have corrupted my chip and I’m now so sad. I don’t know what to do to recorver it. It fails to write no matter what I try. Please could somebody help me ![]()
Can you confirm which product this is? We don’t sell an Ultralight C implant. Do you have an order number we can reference?
Also, can you post full scan data from How to share NFC chip data via TagInfo app - DT Info - Dangerous Things Forum app?
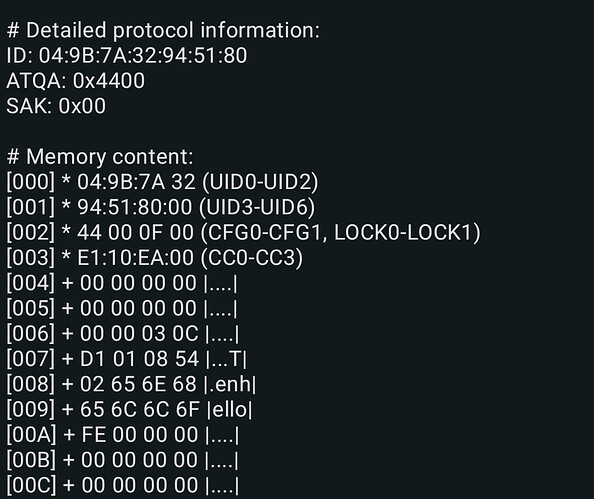
Order number I don’t think I have. Here is the full scan.
04-9B-7A-32-94-51-80_2021-12-27 20-57-49_taginfo_scan.txt (15.8 KB)
OK so it’s an xSIID try this.
It didn’t work ![]()
Here is what I’ve got:
My phone is complaining about the old version of NFC Shell, but there is no newer version, right?
That version of NFC shell should be fine. From your tag info scan data I think you should try a different set of commands. I will post those shortly.
Hi Amal, did you find anything?
Damn! Forgot! I’ll get this sorted shortly.
I decided and managed to clean up the memory content using the NFC Advanced commands. I was hoping that any corrupted text would go away. Then I was all clean but the tag still didn’t accept to write anything on it.
Then I found the TagWriter App and tried to use the erase & format. It didn’t work either because it complained that the tag was protected.
Then I tried to write anything again just to test. I was surprised that it worked! TagWriter managed to write while NFC Tools could not. Why? I’m puzzled.
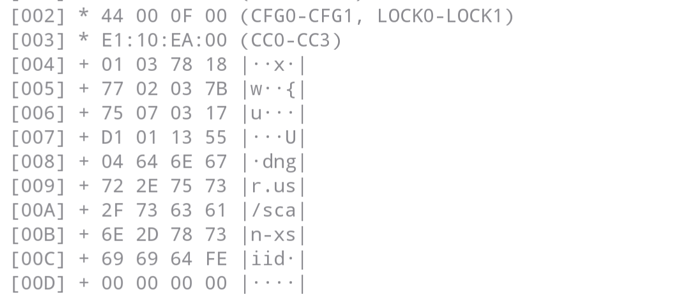
I’m sending the TagInfo after the fix for you to compare. It seems to have less memory blocks.
I’m happy that I can use my tag again \o/ ![]()
04-9B-7A-32-94-51-80_2022-01-16 02-28-53_taginfo_scan.txt (11.5 KB)
The problem has to do with how the capability container was set up. This is read only now and cannot be changed. Basically you see how pages 04 to 06 are set to null values 00… those pages should contain TLV data to tell the NFC device (your phone) how to handle the memory pages available to it because the capability container is … well it’s wonky.
So at this point it’s up to the flexibility of the app in question to decide how to handle exceptions and errors and unexpected values like this situation, and tag writer just does a better job of it.
Now that there is a clean ndef record on the chip, other apps should be able to modify it.
That is what the TLV looks like. The actual NDEF record starts at page 006 bytes 03 17
Well, I tried to write in the 04 to 06 and now I think I succeeded in totally breaking it. I think I bricked the memory… I cannot even read it anymore… stupid me.
I know, I take responsibility for it, but do you think is there a way of saving it?
You can’t brick the memory (because we made it so you couldn’t), but you can fuck it so hard the phone will fail to handle it because again, phones are absolutely dog shit NFC devices. To fix it you’ll need a proxmark3 or an acr122u and some software like the kava version of NFC tools.
I think I did an excellent job in funcking it up haha. I will then do what you said and when I have results, I’ll post them here.
Thank you for the help so far.
Hi Amal, so long! I hope you are well ![]()
I bought and setup the proxmark3. I have not managed to get any readings from my implant with it. The proxmark3 do not lit the light of the implant while my cellphone does. Could you give me a tip of what should I do?
I tried some commands and the only one that gave me something was this:
pm3 --> lf search
[=] NOTE: some demods output possible binary
[=] if it finds something that looks like a tag
[=] False Positives ARE possible
[=]
[=] Checking for known tags...
[=]
[=] Odd size, false positive?
[+] Indala (len 169) Raw: 80000000000200010800080000080040000205900800000100080000
[+] Valid Indala ID found!
[=] Couldn't identify a chipset
What implant do you have?
I see you are doing an lf search, I assume you have an xEM, a NExT Implant or a FlexEM etc.
Coupling is critical, can you take a photo of how you are trying to read your implant?
Can you try a lf search with your LF xFD ![]()
How long ago did you install implant?
What guide do you follow to setup your Proxmark?
Do you have a full sized test card to try it on?
From earlier in the thread, it’s an xSIID. Try hf search
You want the implant to be laying across the antenna, and you may need to press it into your hand a bit to get a read.
Yes, it is a xSIID
I tried hf as well with no luck ![]()
pm3 --> hf search
[!] No known/supported 13.56 MHz tags found
The implant has almost 1 year.
I followed these instructions to setup the Proxmark. I was able to read a full sized test card.
I have try to put my hand on the antenna following the instructions, it still does not work.
The line is where the implant is
Trying one side
Trying the other side
that is the LF antenna you are using, you want to use the other antenna on there, the flat black part
Yes, I tried both antennas the LF and the HF. For HF I tried top and bottom of the reader.
Can you show how it’s being held to your implant?
Also have you used the delay command?
It’s much easier to position the proxmark3 if you have a delay in place