Hello all! I’m a new member but have been lurking for a long time. I’ve mostly used my proxmark for lf research and cloning.
I’ve recently had need to clone an iClass Legacy credential and thought it would be fairly simple from what I had been reading here over the course of looking into lots of things.
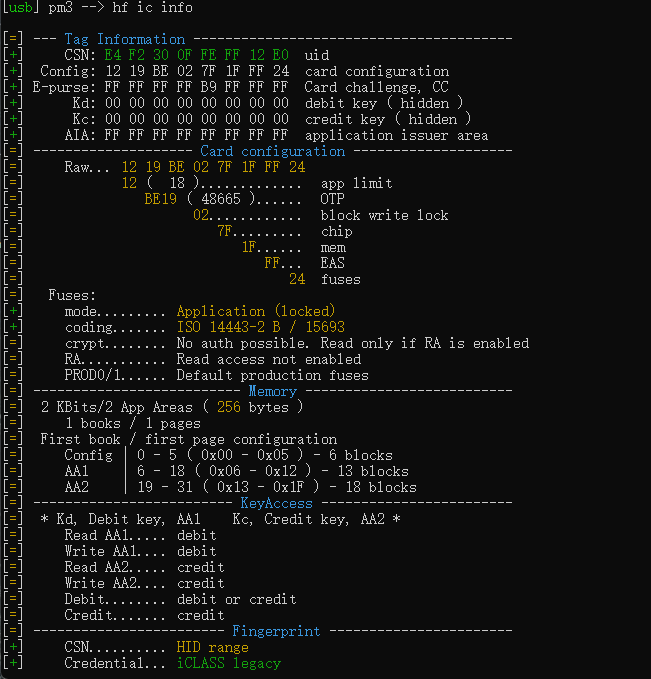
When I run the hf ic info command I get the following:
[=] --------------------- Tag Information ----------------------
[+] CSN: 02 15 9F 00 F8 FF 12 E0 uid
[+] Config: 12 FF FF FF 7F 1F FF 3C card configuration
[+] E-purse: FC E1 FF FF FF FF FF FF Card challenge, CC
[+] Kd: 00 00 00 00 00 00 00 00 debit key, hidden
[+] Kc: 00 00 00 00 00 00 00 00 credit key, hidden
[+] AIA: FF FF FF FF FF FF FF FF application issuer area
[=] -------------------- card configuration --------------------
[=] Raw: 12 FF FF FF 7F 1F FF 3C
[=] 12..................... app limit
[=] FFFF ( 65535 )...... OTP
[=] FF............ block write lock
[=] 7F......... chip
[=] 1F...... mem
[=] FF... EAS
[=] 3C fuses
[=] Fuses:
[+] mode......... Application (locked)
[+] coding....... ISO 14443-2 B / 15693
[+] crypt........ Secured page, keys not locked
[=] RA........... Read access not enabled
[=] -------------------------- Memory --------------------------
[=] 2 KBits/2 App Areas ( 256 bytes )
[=] AA1 blocks 13 { 0x06 - 0x12 (06 - 18) }
[=] AA2 blocks 18 { 0x13 - 0x1F (19 - 31) }
[=] ------------------------- KeyAccess ------------------------
[=] * Kd, Debit key, AA1 Kc, Credit key, AA2 *
[=] Read A....... debit or credit
[=] Read B....... debit or credit
[=] Write A...... credit
[=] Write B...... credit
[=] Debit........ debit or credit
[=] Credit....... credit
[=] ------------------------ Fingerprint -----------------------
[+] CSN.......... HID range
[+] Credential... iCLASS legacy
[+] Card type.... PicoPass 2K
Which shows it’s an iClass Legacy credential.
When I run any command like: “hf ic dump --ki 0” I get a response like:
[+] Using AA1 (debit) key[0] AE A6 84 A6 DA B2 32 78
[=] Card has at least 2 application areas. AA1 limit 18 (0x12) AA2 limit 31 (0x1F)
.
[!!] failed to communicate with card
When I run hf search I get:
pm3 --> hf search
[\] Searching for iCLASS / PicoPass tag...
[+] iCLASS / Picopass CSN: 02 15 9F 00 F8 FF 12 E0
[+] Valid iCLASS tag / PicoPass tag found
When I run “hf ic chk -f iclass_default_keys.dic” I get:
[+] loaded 11 keys from dictionary file C:\Working\ProxSpace\pm3\proxmark3\client\dictionaries/iclass_default_keys.dic
[+] Reading tag CSN / CCNR...
[+] CSN: 02 15 9F 00 F8 FF 12 E0
[+] CCNR: FC E1 FF FF FF FF FF FF 00 00 00 00
[=] Generating diversified keys
[+] Searching for DEBIT key...
[/]Chunk [000/11]
[+] time in iclass chk 2.3 seconds
It doesn’t say that it found any valid keys for it.
I’m starting to wonder if the readers are set to use a non standard key or something else I’m not thinking of.
[ CLIENT ]
RRG/Iceman/master/v4.14434-62-gf4487abed 2021-10-16 14:42:19
compiled with… MinGW-w64 10.3.0
platform… Windows (64b) / x86_64
[ PROXMARK3 ]
firmware… PM3 GENERIC
[ ARM ]
bootrom: RRG/Iceman/master/v4.14434-62-gf4487abed 2021-10-16 14:44:03
os: RRG/Iceman/master/v4.14434-62-gf4487abed 2021-10-16 14:44:34
compiled with GCC 10.1.0
[ FPGA ]
LF image built for 2s30vq100 on 2020-07-08 at 23:08:07
HF image built for 2s30vq100 on 2020-07-08 at 23:08:19
HF FeliCa image built for 2s30vq100 on 2020-07-08 at 23:08:30
[ Hardware ]
–= uC: AT91SAM7S512 Rev B
–= Embedded Processor: ARM7TDMI
–= Internal SRAM size: 64K bytes
–= Architecture identifier: AT91SAM7Sxx Series
–= Embedded flash memory 512K bytes ( 53% used )
Sorry for the long post with a bunch of copied outputs but I’m stumped and need a push in the right direction.
I’ve scoured the internet and this forum for people having the same issue but have only found @695 and the info posted in Cloning a HID IClass 2k key fob - #19 by 695
I also think the info from @NinjuhhNutz posted in So You Want To Implant An HID Card may also be key but I can’t quite figure out what’s going on…
Thanks if you read this far, any help would be most appreciated!