I want to install a Java Card implant soon and an doing some preliminary testing before deciding on whether to install the Apex Flex I have or instead purchase either an Apex Mega or FlexSecure.
I also have a number of Java Card devices that date back to original VivoKey beta. They include:
- 1 encased VivoKey tapped to the back of a business card
- 2 “naked” VivoKeys tapped to the back of business cards
- several Fidesmo test cards
- a Fidesmo branded Yubikey-style NFC/USB combo
My goal has been to simply get 3 applets tested and working on a single VivoKey. The FIDO applet, the OTP applet, and the HMAC applet. I’ve had some success, but am still a ways off and not sure what else to try.
I’m using a combination of:
- Samsung Galaxy S23 Ultra
- Pixel 4 XL
- ACR122U
- Digital Logic DL533R CS IP54 w/ Booster (another PC reader)
I’ve had some partial successes but have not been able to get all 3 applets installed and tested. Below are some of the issues I’ve had and some questions.
1. Cannot install any applet via Fidesmo’s fdsm utility
@StarGate01 Is it still possible to install applets directly via fdsm? I remember doing this back in the VK beta, but every app I’ve tried to install, I get a Unexpected error: Failed to run service: newPosition < 0: (-2 < 0). I’m using the command fdsm.exe --run <app_id>/install and am obtaining the app IDs either from the Fidesmo app on my phone or Fidesmo’s API.
I’ve tried multiple applets, including the “free memory” applet, which I kind of use as my test app, since I presume it has one of the smallest sizes.
I’ve tried using both the .exe utility and the .jar file. I’m using the latest release (fdsm v23.04.18-0-g5ddce34).
I’m using the ACR122U and have tried installing applets dozens of times in various orientations of the VivoKey; both the naked and encased ones. I also tried using the DL533R, but it bricked one of the VKs on the first install attempt.
I have been able to use both the ACR122U and the DL533R to install the Fidesmo “Applet Platform Tests” applet on a Fidesmo test card.
Destroying/removing applets via fdsm --run <appId>/[destroy|uninstall] works almost without fail. Listing applets also works.
My biggest concern is that if I can’t get even a single applet installed on a naked flex chip using a desktop reader, than the FlexSecure won’t be a viable option. Is there any reason to expect different performance when installing an applet to the flexSecure via gp than installing an applet to the original VivoKey via fdsm?
2. OTP Applications
Summary:
- I cannot use the Apex Manager to add OTP accounts to any device. The app just remains on the “Scan your Apex” screen, with no vibration or other indication of success or failure.
- The Apex Manager can scan the JavaCard devices and show the OTP codes that have already been installed.
- I get the same behavior of being able to see codes, but not install new ones on the Yubikey Auth app.
- Both apps seem to have a bug/issue where after a silently failing attempt to add a new OTP account, neither app will even read or acknowledge the NFC device unless the app is force killed and reopened.
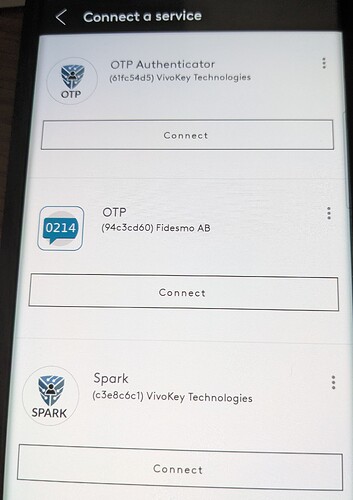
- The Yubikey Authenticator app no longer works with the Fidesmo OTP applet. This isn’t a DT issue, just adding it here for completeness.
- The Vivokey OTP applet is almost impossible to install. In 4+ hours of trying across two phones, I was only ever able to get it installed once to a VK Beta (it was the one that was encased).
- Compare this to a more acceptable 20% success rate when installing the FIDO2 applet (which I believe is substantially larger and thus would require even better coupling).
- I am also able to install the Fidesmo OTP applet with a much higher success rate.
I’m sure many of these issues are related. I guess its possible that all of these are just under the “bad connection/coupling” heading, but that seems hard to believe. Especially given that I have been able to install the FIDO2 applet multiple times (although I haven’t tested actually using it yet).
A few questions:
- My understanding is that the new version of the VivoKey OTP applet uses the same AID as a Yubikey and thus should be readable and writable by both the Apex Manager and the Yubikey Auth apps. Is this correct?
- For purposes of writing new OTP accounts, it shouldn’t matter whether the underlying device is a VivoKey beta, an Apex Flex, or a Fidesmo Yubikey style card, right? As long as the VivoKey OPT applet was successfully installed and recognized by Apex Manager, the actual hardware/chip is irrelevant.
- I’m using Generate QR Codes for Google Authenticator to generate QR codes for adding accounts. This works fine with a Yubikey 5 NFC via the Yubico Auth app. Any reason why these same codes wouldn’t be installable on Apex Manager?
Misc
I’ve tried to get a new developer account set up with Fidesmo (or have my old one reinstated), but after asking me some initial questions they’ve gone radio silent (its been over a week). My guess is that because my response to their “What are you developing” questions wasn’t something with large (or even small) commercial applications, they aren’t really interested. I know others on the forum have had the same experience. Not faulting DT in any way, but it would have been nice to at least been given a “Thanks, but not interested” response.
The flexSecure looks like a good alternative to the Fidesmo developer issue, but there seems to be a lack of viable options for desktop readers, and the only Android app I found to install applets hasn’t been updated in 10 years and can’t even be installed on my device. The ACR122U is no longer being produced, and it already didn’t have great performance. From what @amal has said, its successors aren’t any better. I know @StarGate01 and others have mentioned good performance with the DL533R Stick, but they have been out of stock for a while. I ordered one of the last two full sized version but it seems to have worse performance than the ACR.
I have some hope that the NFC repeater I ordered from @Hamspiced will help with the phone and desktop. It should arrive in a couple of days.
Anyone have other suggestions for a USB reader and/or a relatively inexpensive Android phone that has good NFC performance with the flex style implants?